How to install and set up BurpSuite | HydrAttack 1. Download BurpSuite Community Edition application – https://portswigger.net/burp/communitydownload 2. Install the application, start the application andView More
Category: CheatLists
IoT Firmware emulation
1. binwalk firmware.bin binwalk firmware.bin 2. dd if=firmware.bin skip=538952 bs=1 of=firmware_squash.sqsh dd if=firmware.bin skip=538952 bs=1 of=firmware_squash.sqsh 3. unsquashfs firmware_squash.sqsh unsquashfs firmware_squash.sqsh 4. ls ls 5.View More
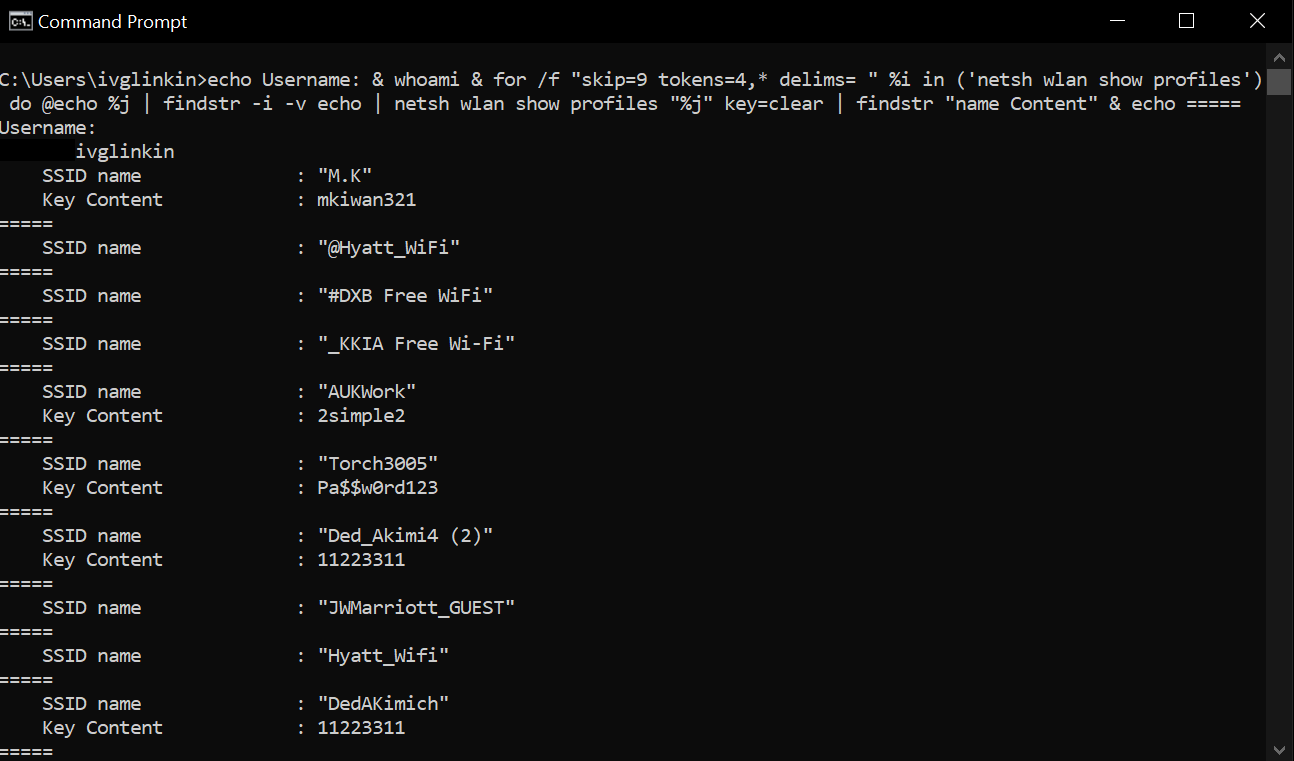
Windows Wi-Fi passwords revealing
Show Wi-Fi SSIDs netsh wlan show profiles Show password for the specific Wi-Fi SSID netsh wlan show profiles “SSID_name” key=clear One-liner to getView More
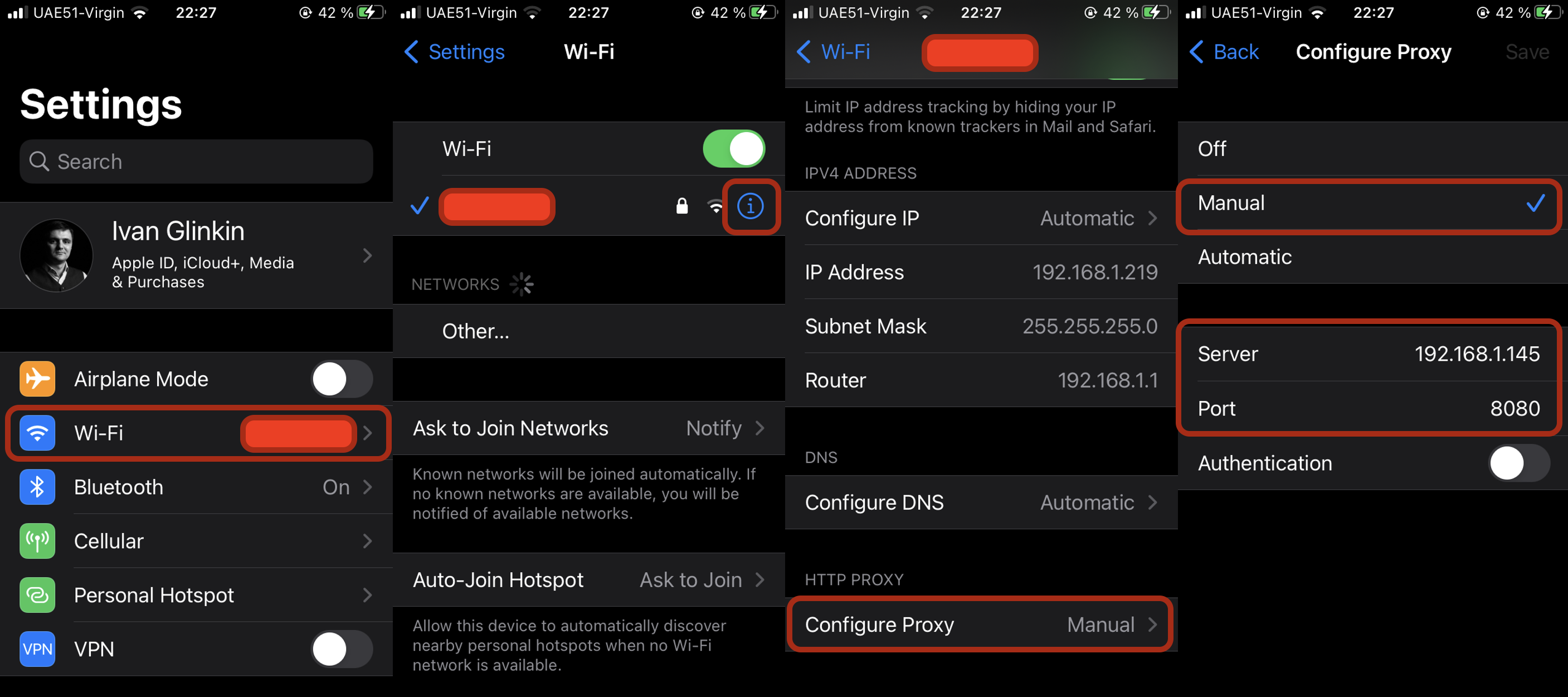
Docker for pentesters or switching GNU/Linux environment from virtual machines into containers
From ages ago till now there are plenty of discussions regarding the best/appropriate approach of using a pentesting OS: as a main, live system, dualView More
Brief iOS apps analysis (without Jailbreak)
For cyber security analysts and penetration testers dealing with mobile applications is the day-to-day activity. But if we are talking about Android applications, it’s quiteView More
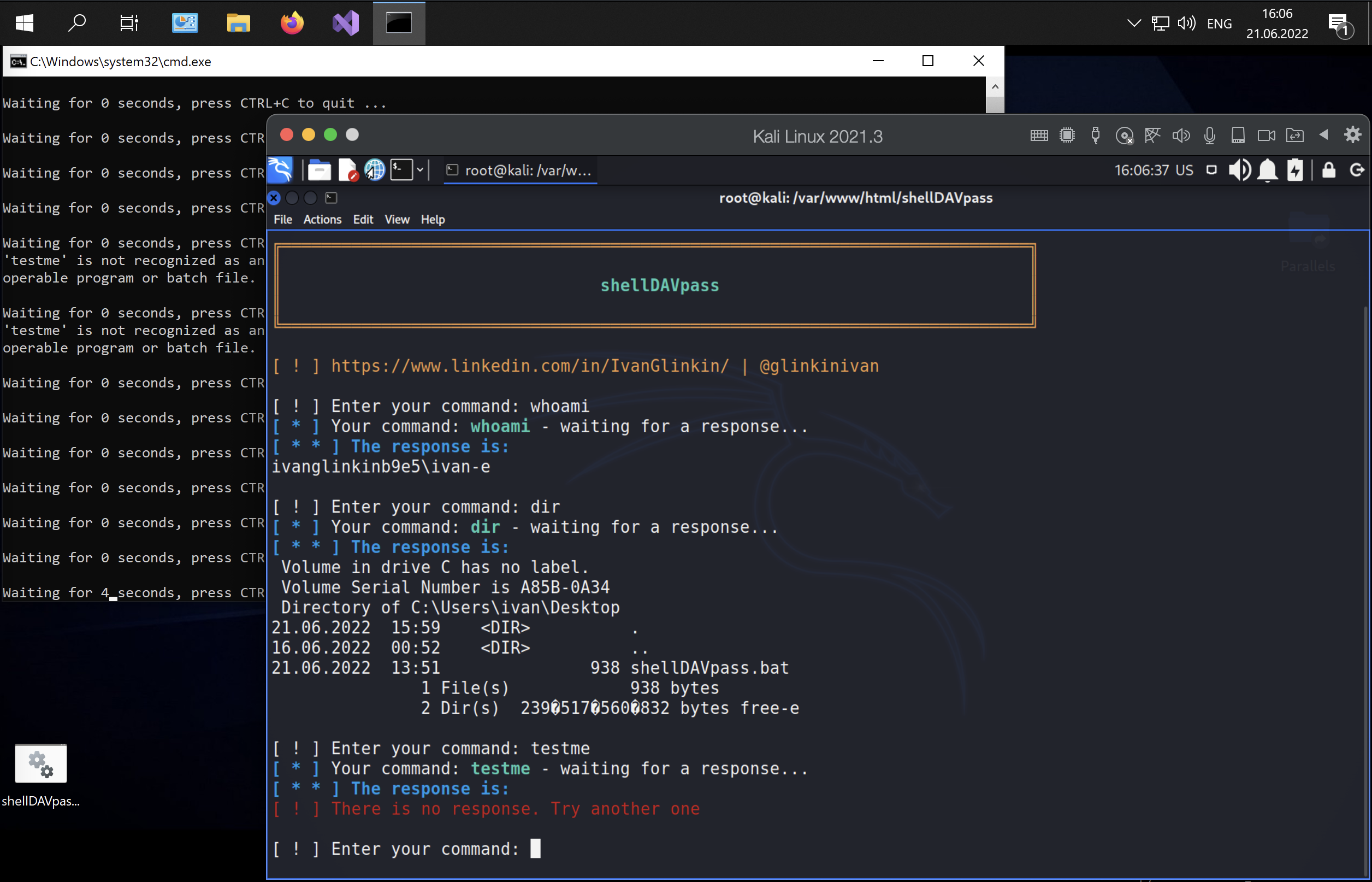
shellDAVpass – non interactive reverse shell to bypass the defender and AntiVirus detections
When we are talking about hacking, basically, the main purpose of any penetration testing is to get the full control over the server aka theView More
Alfa AWUS036ACH WiFi adapter install on Kali Linux
That is the single instruction how to install Alfa AWUS036ACH WiFi adapter on Kali Linux (including M1 Mac CPU). INSTALLATION git clone https://github.com/aircrack-ng/rtl8812au.git # DownloadView More
Install Volatility on Kali Linux (including M1 Mac CPU)
That is the single instruction how to install Volatility application on Kali Linux (including M1 Mac CPU). INSTALLATION #!/bin/bashsudo apt-get updatesudo apt install -y python2.7sudoView More
AutoSUID
AutoSUID application is the Open-Source project, the main idea of which is to automate harvesting the SUID executable files and to find a way forView More
The Russian Kerbrute
The first thing every penetration tester performs getting into a controller domain subnet is to brute force discovery of users which is called a KerbruteView More
Fast Google Dorks Scan
“Enumeration is the key” – that’s the main tagline of the Offensive Security Certified Professional certification. Indeed, as a statistic says, more than a halfView More
h@cktivitycon2021 by HackerOne
Capture the flag (aka CTF) is a cybersecurity game the main aim of which is to crack/solve/find the solution to the weirdest IT tasks andView More
Red Teaming – Through PostgreSQL to shell
The easiest way to get reverse shell through the PostgreSQL database. 1. Connect to the DB2. Create a new table CREATE TABLE demo(t text);3. RunView More
How to cheat on a Cyber Security exam
Cheating is unfair, wrong and, in particular cases, strictly prohibited by the law. It may cause you lose your friends, family, achievements, work and whatever.View More
Useful bashrc configuration file
Hello Linux users! When I’m doing my job I’m trying to set my working place as efficient and useful as it’s possible. Bash terminal isView More