How to install and set up BurpSuite | HydrAttack 1. Download BurpSuite Community Edition application – https://portswigger.net/burp/communitydownload 2. Install the application, start the application andView More
Author: Ivan Glinkin
Ethical Hacking: Easy Way to Get Into / CyberYozh with Ivan Glinkin
Ethical Hacking: Easy Way to Get Into / CyberYozh with Ivan Glinkin #войти_в_it Hey everyone! 👋 I wanted to take a moment toView More
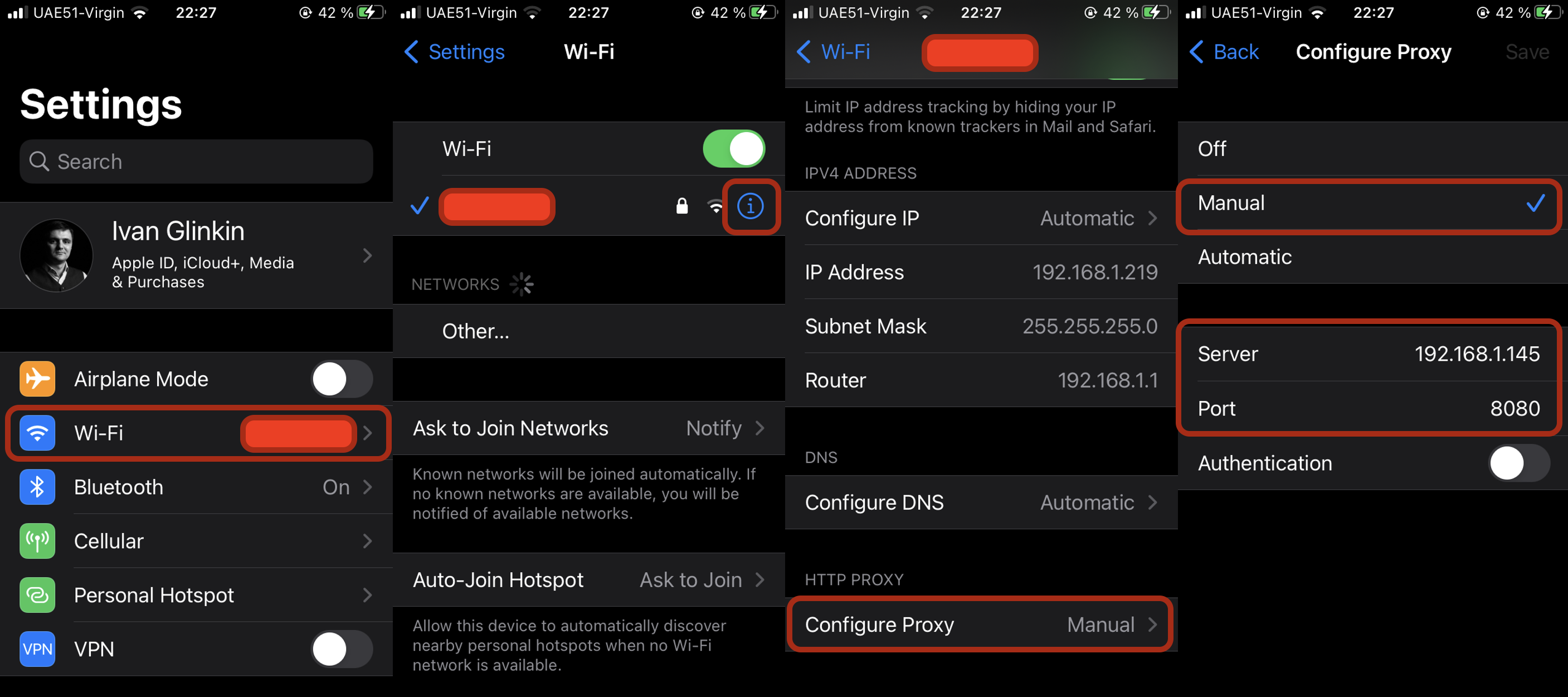
Linksys Velop WiFi 5 Hacking (CVE-2024-36821)
IoT Hardware Penetration testing / Hacking against Linksys Velop WiFi 5 (WHW01v1) version 1.1.13.202617 (issued on September 18, 2020) Useful links: Web-site: https://www.ivanglinkin.com/ Twitter: https://twitter.com/glinkinivanView More
IoT Firmware emulation
1. binwalk firmware.bin binwalk firmware.bin 2. dd if=firmware.bin skip=538952 bs=1 of=firmware_squash.sqsh dd if=firmware.bin skip=538952 bs=1 of=firmware_squash.sqsh 3. unsquashfs firmware_squash.sqsh unsquashfs firmware_squash.sqsh 4. ls ls 5.View More
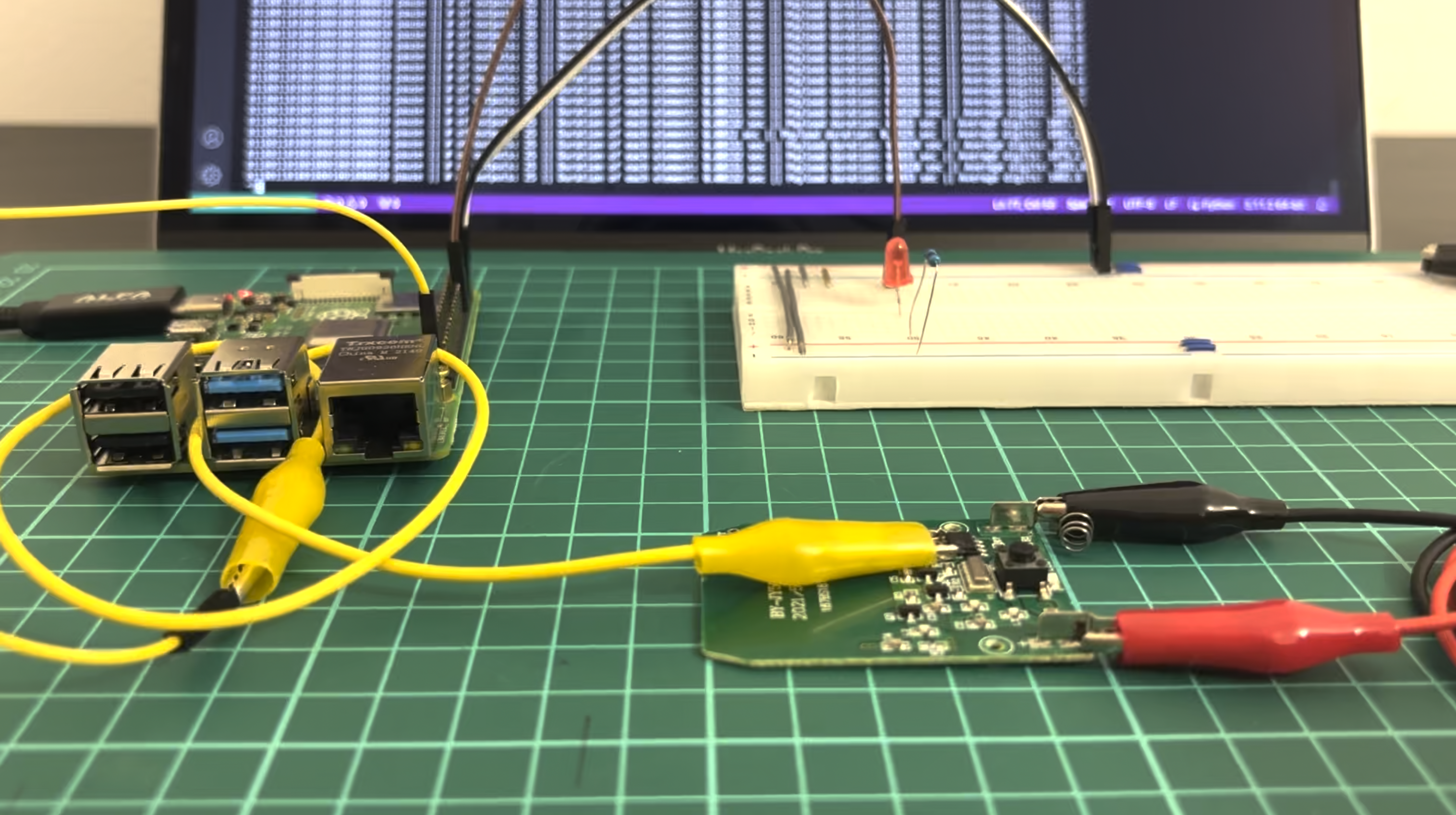
Hardware hacking: Wireless doorbell payload harvesting
Cybersecurity from the offensive perspective is not only related to web-applications and Active directory attacks. There are a lot of hacking areas beside mentioned ones:View More
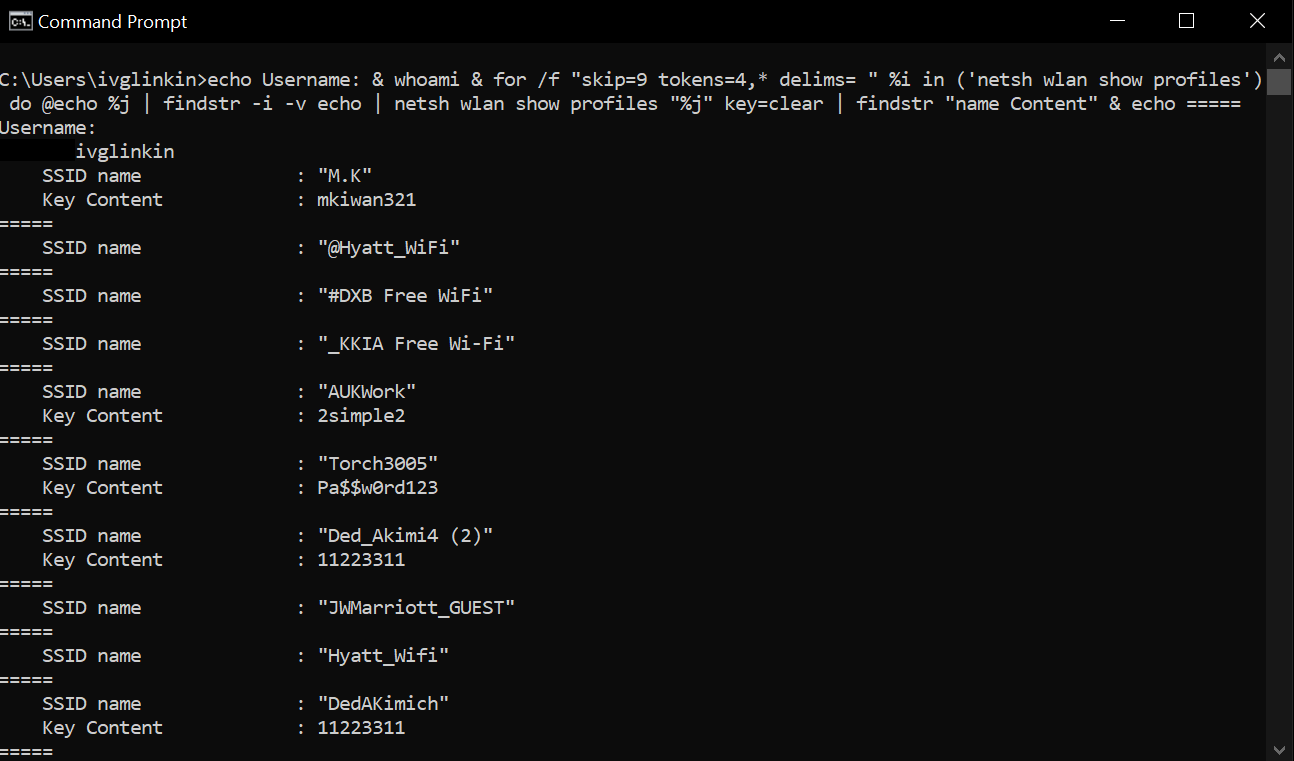
Windows Wi-Fi passwords revealing
Show Wi-Fi SSIDs netsh wlan show profiles Show password for the specific Wi-Fi SSID netsh wlan show profiles “SSID_name” key=clear One-liner to getView More
HackRF as the best SDR friend for hackers
Annotation Being skilled at identifying vulnerabilities in source code, executing SQL injection attack, exploiting outdated services in well-known scripts, and even infiltrating enterprises to gainView More
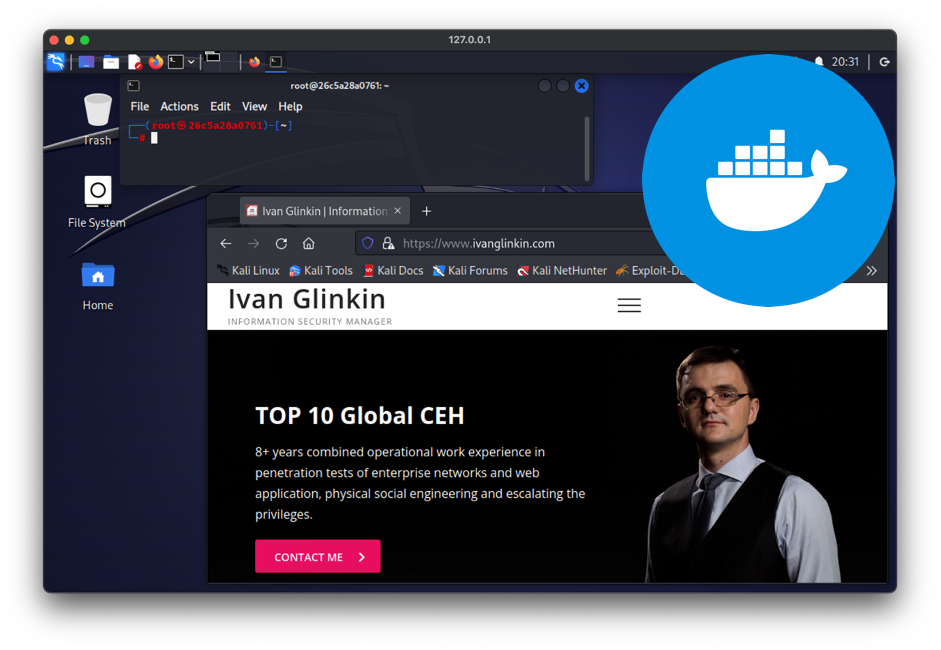
Docker for pentesters or switching GNU/Linux environment from virtual machines into containers
From ages ago till now there are plenty of discussions regarding the best/appropriate approach of using a pentesting OS: as a main, live system, dualView More
Brief iOS apps analysis (without Jailbreak)
For cyber security analysts and penetration testers dealing with mobile applications is the day-to-day activity. But if we are talking about Android applications, it’s quiteView More
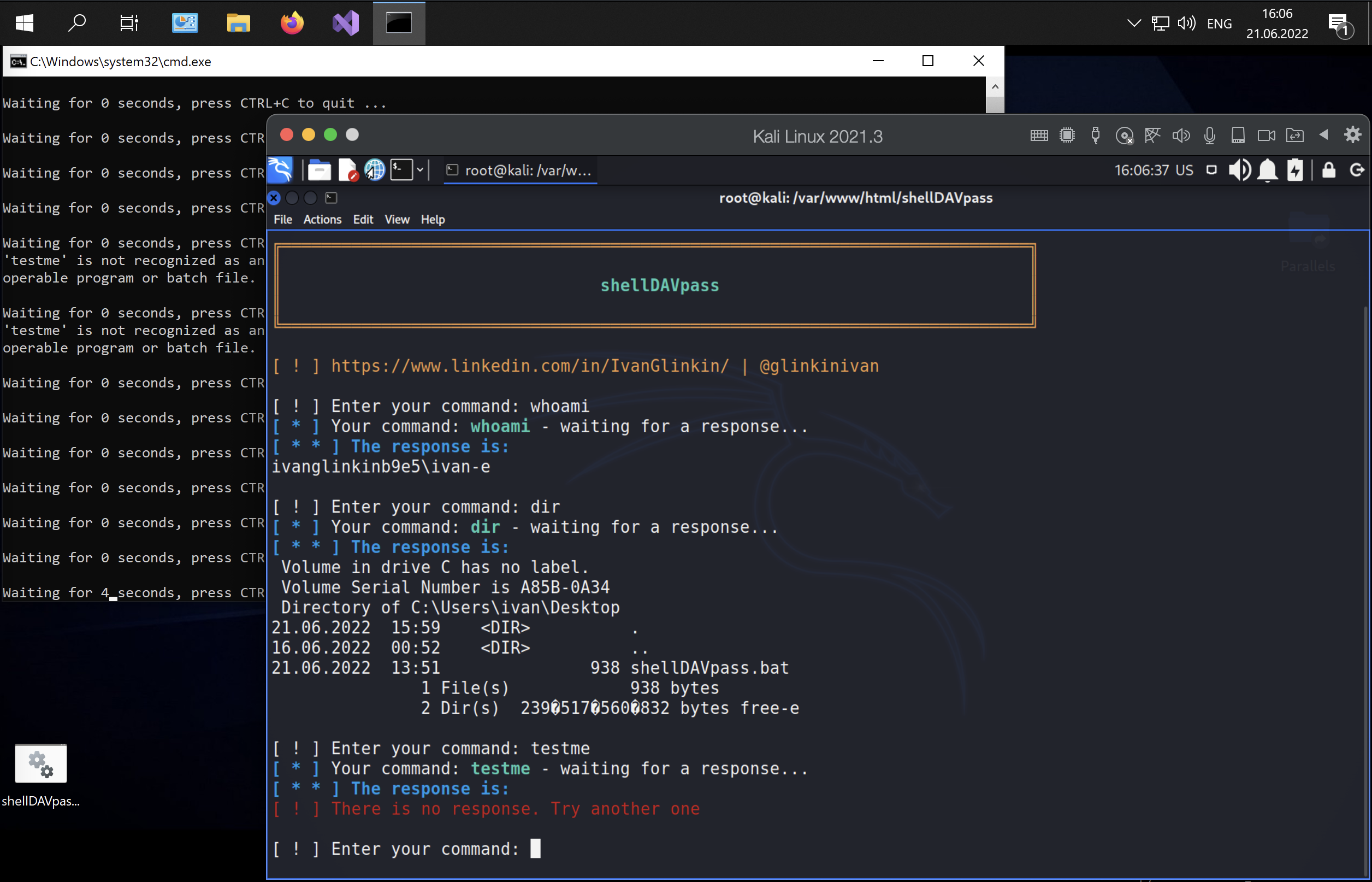
shellDAVpass – non interactive reverse shell to bypass the defender and AntiVirus detections
When we are talking about hacking, basically, the main purpose of any penetration testing is to get the full control over the server aka theView More
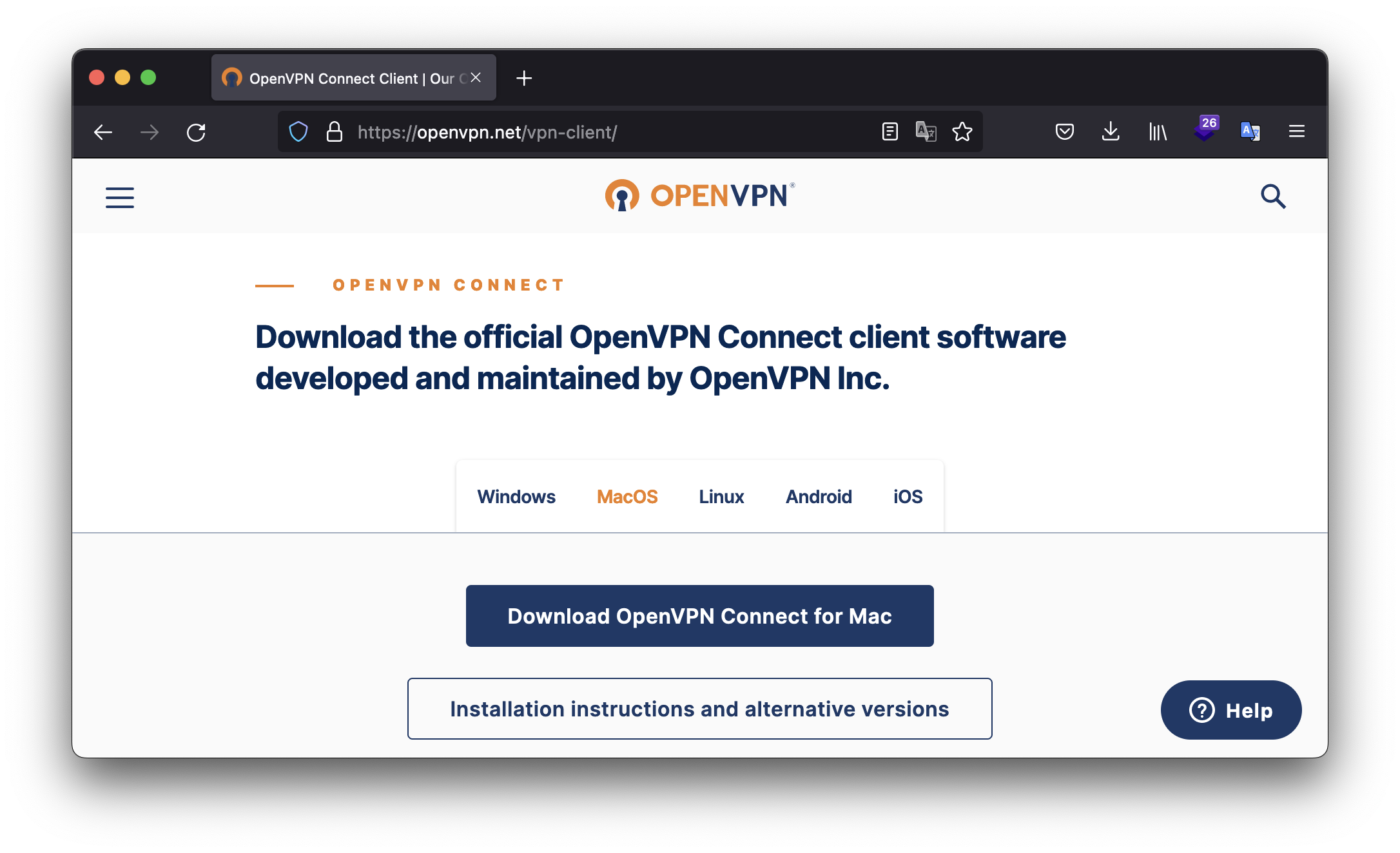
Are free VPNs safe enough?
Nowadays, more and more people are using VPN (virtual private network) for different purposes. For one of them that’s a good stuff to hide theirView More
Alfa AWUS036ACH WiFi adapter install on Kali Linux
That is the single instruction how to install Alfa AWUS036ACH WiFi adapter on Kali Linux (including M1 Mac CPU). INSTALLATION (approach 1) 1. sudoView More
Install Volatility on Kali Linux (including M1 Mac CPU)
That is the single instruction how to install Volatility application on Kali Linux (including M1 Mac CPU). INSTALLATION #!/bin/bashsudo apt-get updatesudo apt install -y python2.7sudoView More
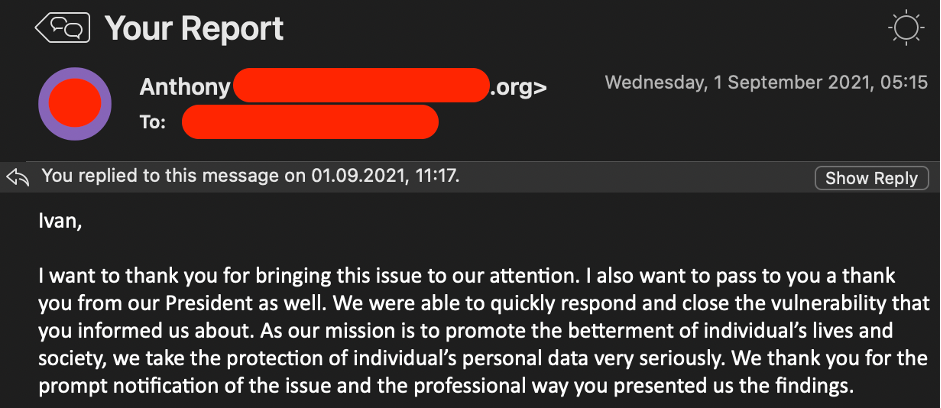
Big companies “Childhood diseases”
There is a widespread opinion as big the company is as harder to find breaches there: all the well-known vulnerabilities are fixed and mitigated, DevOpsView More
AutoSUID
AutoSUID application is the Open-Source project, the main idea of which is to automate harvesting the SUID executable files and to find a way forView More