Cybersecurity from the offensive perspective is not only related to web-applications and Active directory attacks. There are a lot of hacking areas beside mentioned ones:View More
Tag: remote
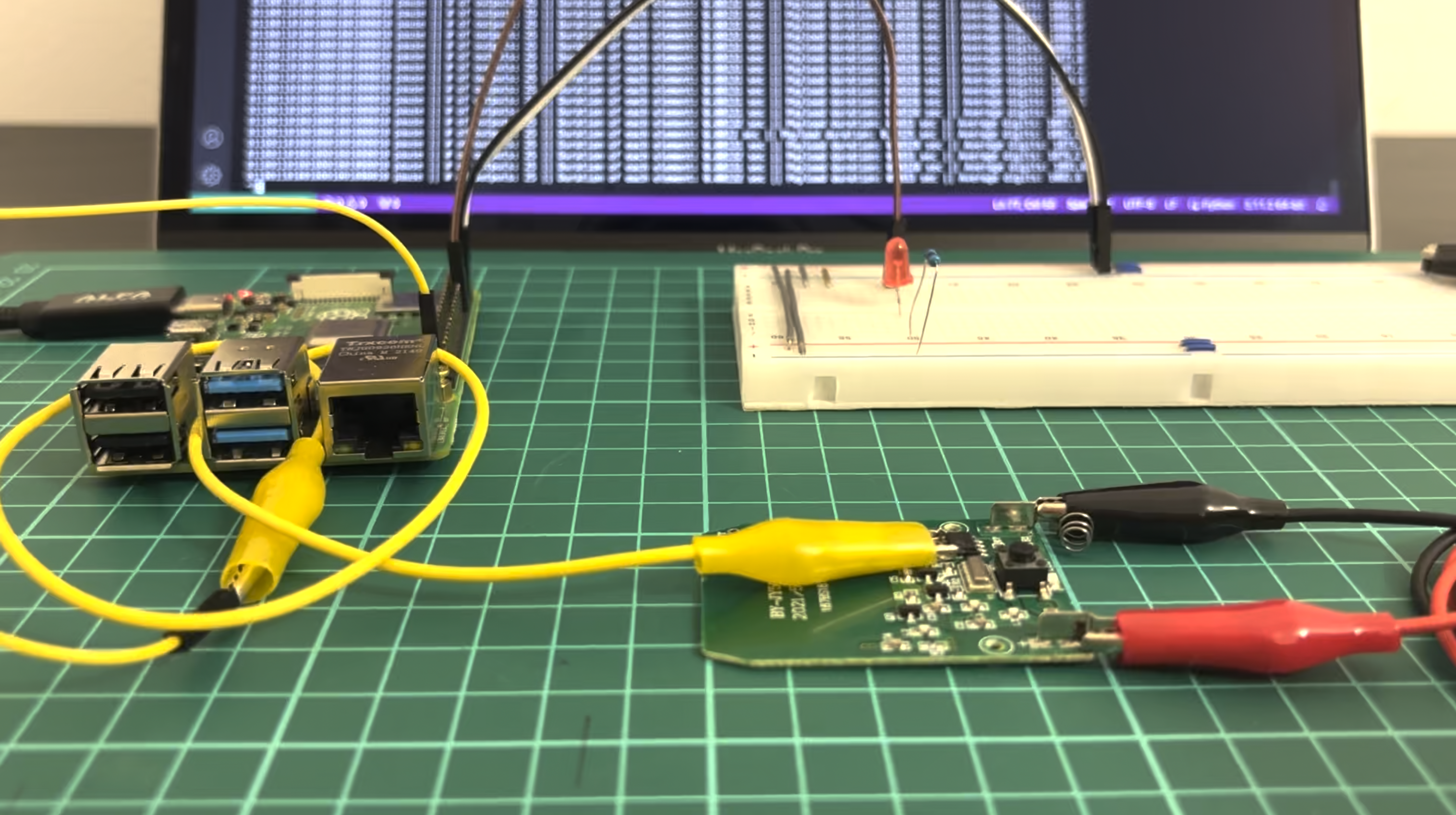
HackRF as the best SDR friend for hackers
Annotation Being skilled at identifying vulnerabilities in source code, executing SQL injection attack, exploiting outdated services in well-known scripts, and even infiltrating enterprises to gainView More
Docker for pentesters or switching GNU/Linux environment from virtual machines into containers
From ages ago till now there are plenty of discussions regarding the best/appropriate approach of using a pentesting OS: as a main, live system, dualView More