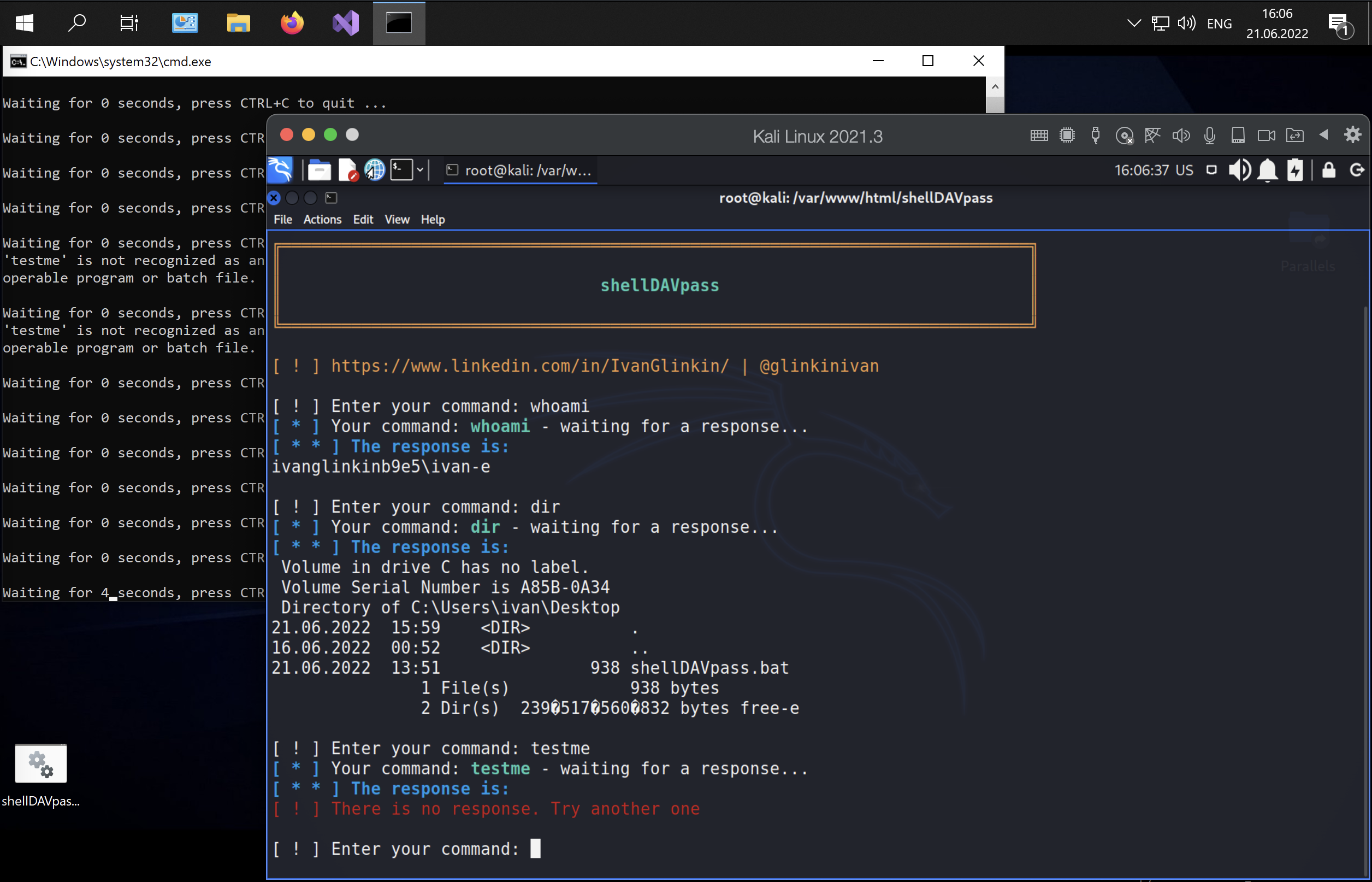
When we are talking about hacking, basically, the main purpose of any penetration testing is to get the full control over the server aka theView More
Tag: shell
Red Teaming – Through PostgreSQL to shell
The easiest way to get reverse shell through the PostgreSQL database. 1. Connect to the DB2. Create a new table CREATE TABLE demo(t text);3. RunView More
Simple port enumeration
Hello hackers! What’s your favorite network scanner: NMap, ZenMAP, Metasploit or “your answer”? If you ask me, NMap is the best and other are justView More