“Enumeration is the key” – that’s the main tagline of the Offensive Security Certified Professional certification. Indeed, as a statistic says, more than a half of all the successful hack were performed after a great reconnaissance. Moreover, that’s the first step every cyber kill chain starts with. In this article we will reveal reconnaissance stage using one of the useful applications – Fast Google Dorks Scan.
- Google dorks
If you are an OSINT professional or cyber security enthusiast with at least 1+ years’ experience you have already known or at least heard about Google dorks. If so, I will repeat, otherwise:
Google hacking, also named Google dorking, is a hacker technique that uses Google Search and other Google applications to find security holes in the configuration and computer code that websites are using.
How does it work? In a nutshell, Googlebot goes through the internet and save all the web-pages to its database, sorting by the categories.
Web-site | Title | Text | Date | Filetype |
website1.com | Hack tools | Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. | 01.07.2021 | php |
Website2.com | Avatar | – | 13.10.2020 | jpg |
After that, a researcher, using the prepared commands, get the data from the specific database’s tables. A search query with “site:*ru filetype:sql $6$“ would locate all SQL files from the RU domains, which contain $6$ (password with the SHA-512 encryption) text.
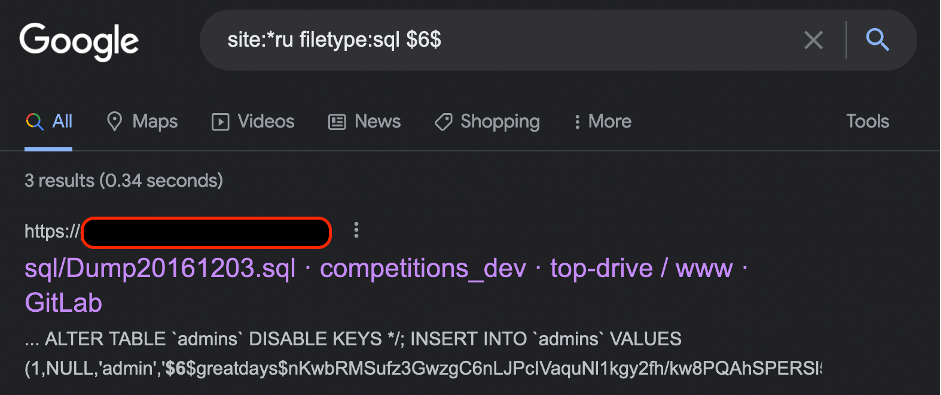
As you may see we successfully found the database’s dump with admin hashed password. Because of admins of small web-sites do not change their passwords regularly I bet, if we can decrypt the hash, we will get into the CMS under the admin privileges.
Another useful search is following “intitle:IP Webcam” inurl:”/greet.html” which will list you web-servers with online webcams.
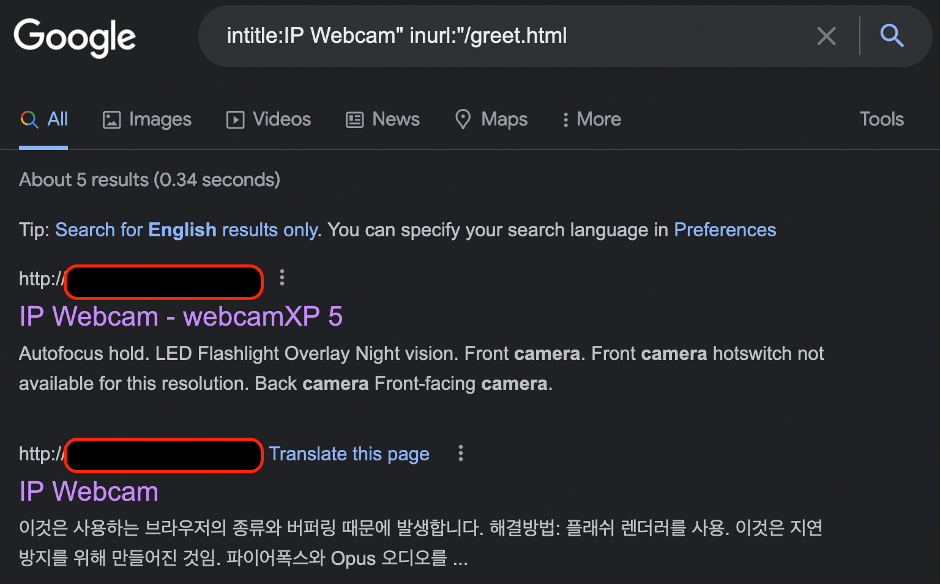
Let’s check that out.
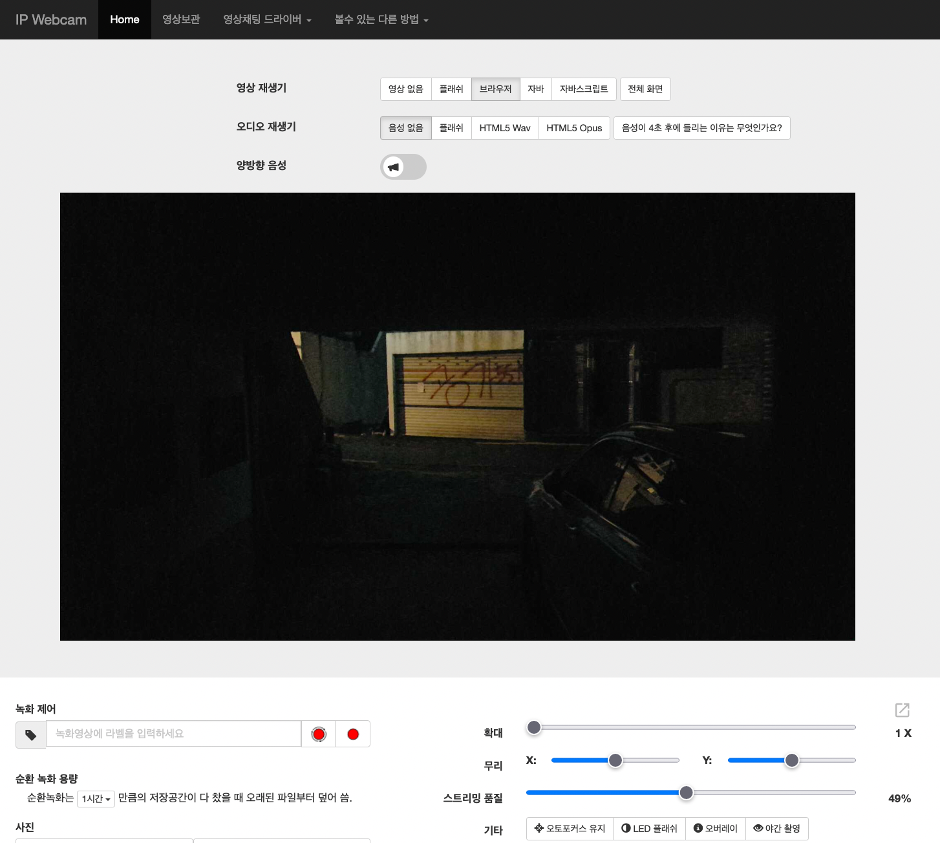
Perfect, we succeeded to get access to a personal webcam. Moreover, there is a dashboard, which means we can control the device. And the crucial thing is it’s no password there at all, consequently any person all across the globe can do whatever he/she wants.
Your next question may be the next: “Is there any some list or database of such dorks I may use?” Our answer is “yes”.
There is a huge list of preset dorks on the “Exploit database” website, which collects since the Google was developed. There are at least 6910 dorks by the date this article was written.
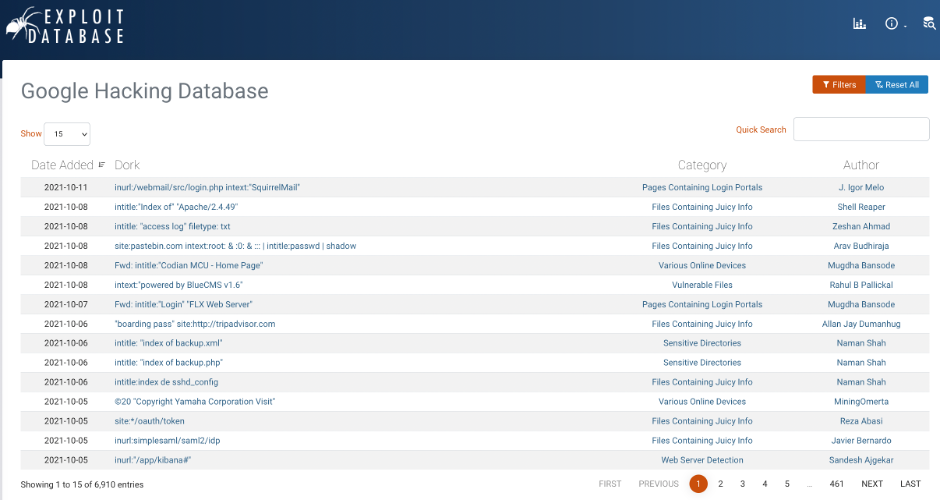
Using preset dorks is interesting, but what if they are not fitted our aims. Let’s go further and try to understand how to prepare dorks for our personal purposes.
We will start with SITE: operator. This specific operator tells Google that you want to get the information only from the define web-site. Let’s try to find information on hakin9 website:
site:hakin9.org
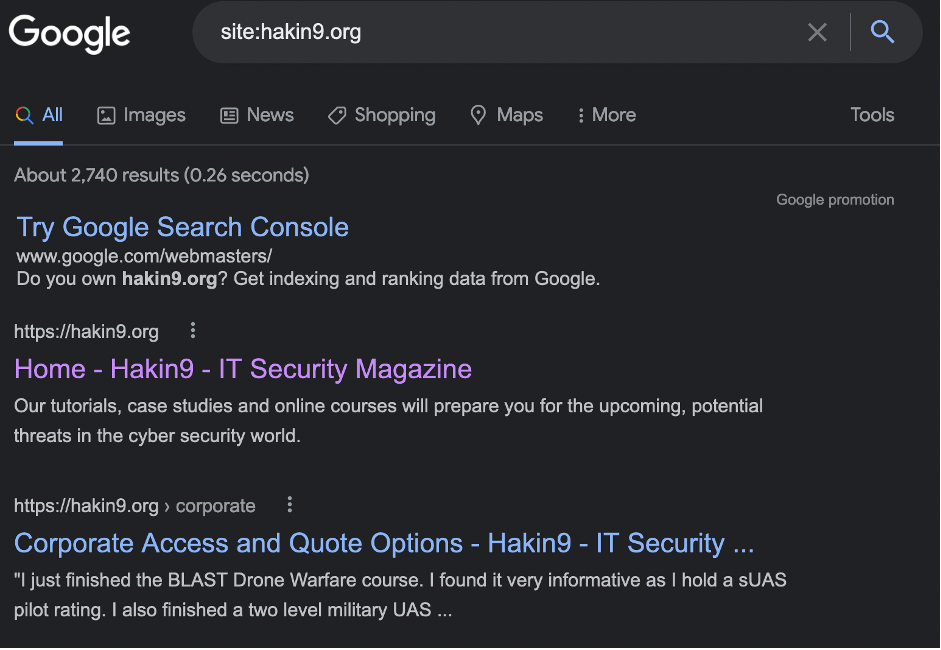
Indeed, when we perform an audit, we do it for the customer with his local network, enterprise and other assets. Other resources will disturb us. To limit the output SITE: is the perfect choice.
The next one is FILETYPE: operator, which search results will only be of this file type. Let’s try to find any text files on our testing web-site:
site:hakin9.org filetype:txt
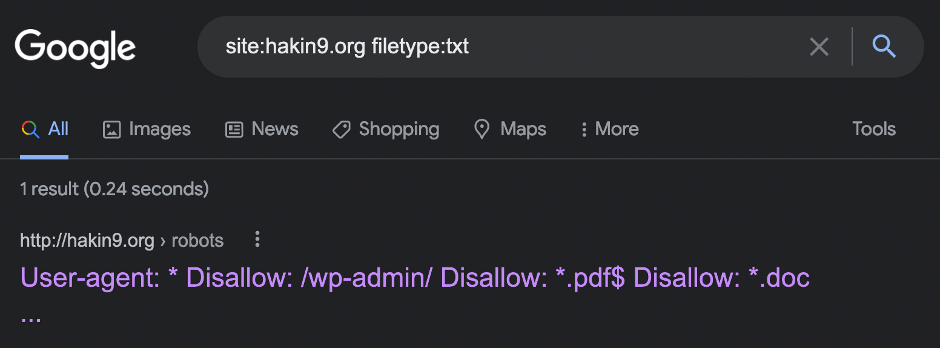
Even the simple TXT output tells us the site is hosting on WordPress CMS and prohibit any search bots to harvest any information from the resource.
Let’s go for INURL: operator which allows us to search the specific word within the URL. As we have already known that Hakin9 is under the WordPress CMS, so let’s find the wp-content links. In spite of the Googlebot is prohibited, who knows maybe it’s ignoring the robots.txt rules.
site:hakin9.org inurl:wp-content
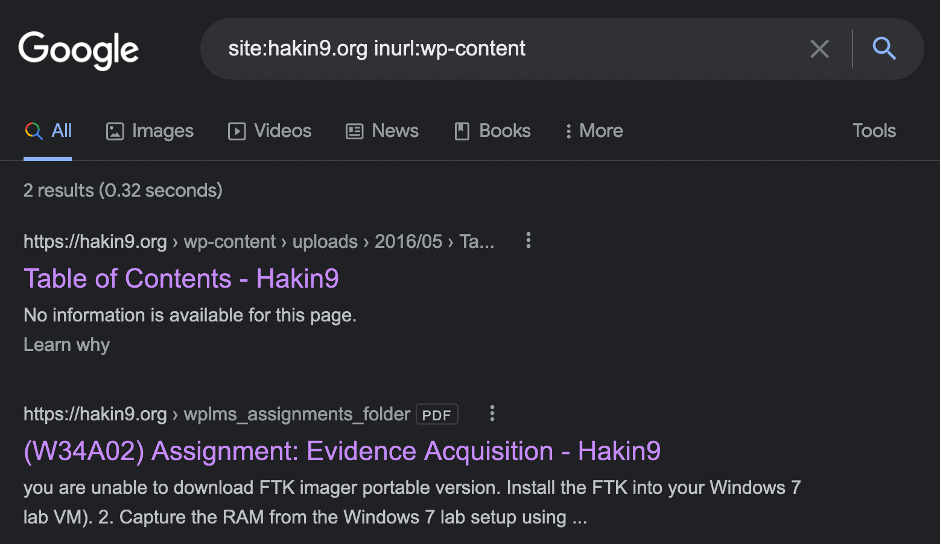
Not too much but it works. How could it be?
- Google dorks automatization
Google dorks are powerful stuff, especially when you know how to deal with that properly. But performing that manually is time consuming and, to be honest, quite boring. How do you think is there an application to save your time and automate the search?
“Fast Google Dorks Scan” by Ivan Glinkin is an open-source application which has been made in an “one button” manner that you do not have to set any arguments or know how it works. All you have to do is only launch the app and set the web-site.
Let’s figure out what each line is mean.
First of all, let’s preset the dorks: login pages, file types and directory traversal.
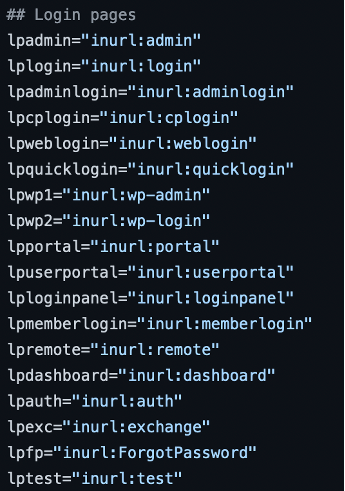
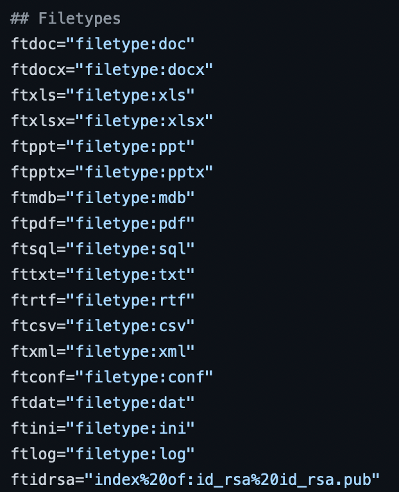

Then we check if user has input the domain. If no, we exit.
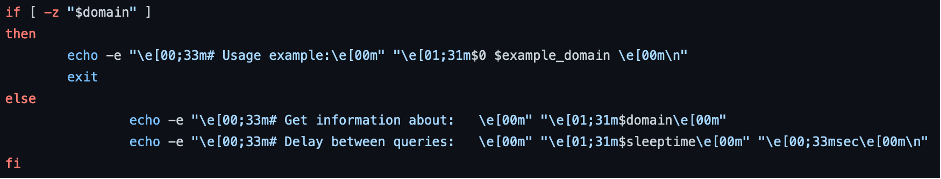
After that there is a heart of our app – search function:
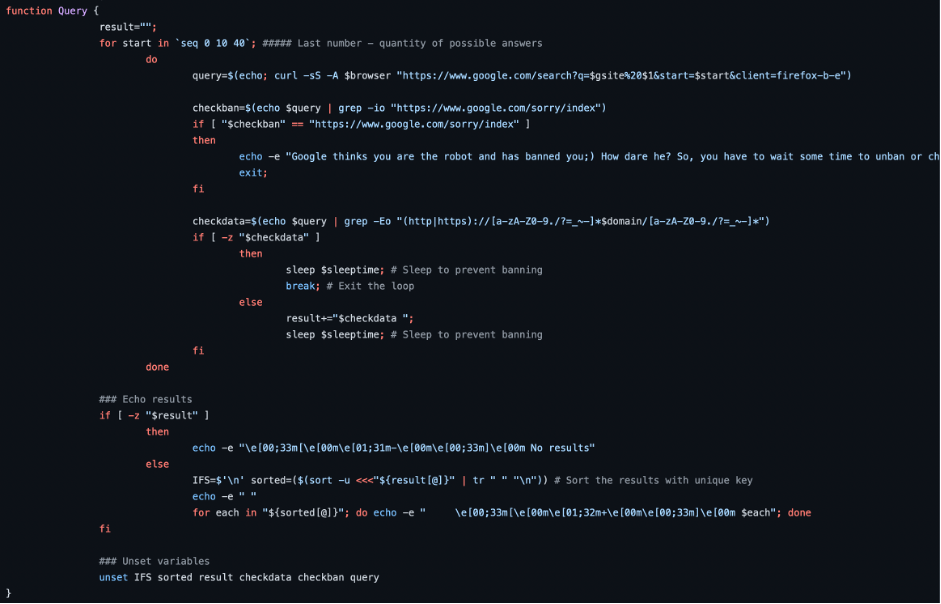
Our program set to get only the first 3 google results pages, so we set 0, 10 and 40 as a starting point.
Then we perform a request to google and save the respond into the QUERY variable.
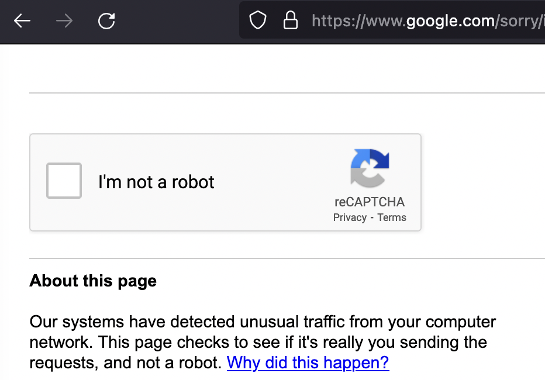
After that we check if google banned us (“Google thinks you are the robot and has banned you;) How dare he? So, you have to wait some time to unban or change your ip!”).
If we are free to go, we check the respond. If there is no any information, we break the loop and move further to the next operator. If there is at least one result, we sorted them and remove the repeated.
The last thing the program has to do is to perform a search.
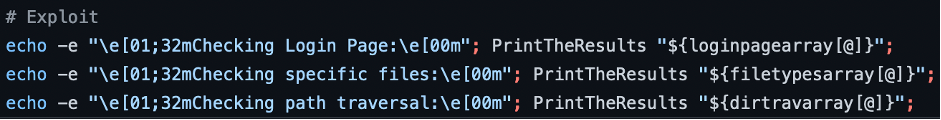
- Exploitation
For the test let’s try to scan haking9.org domain by FGDS app.
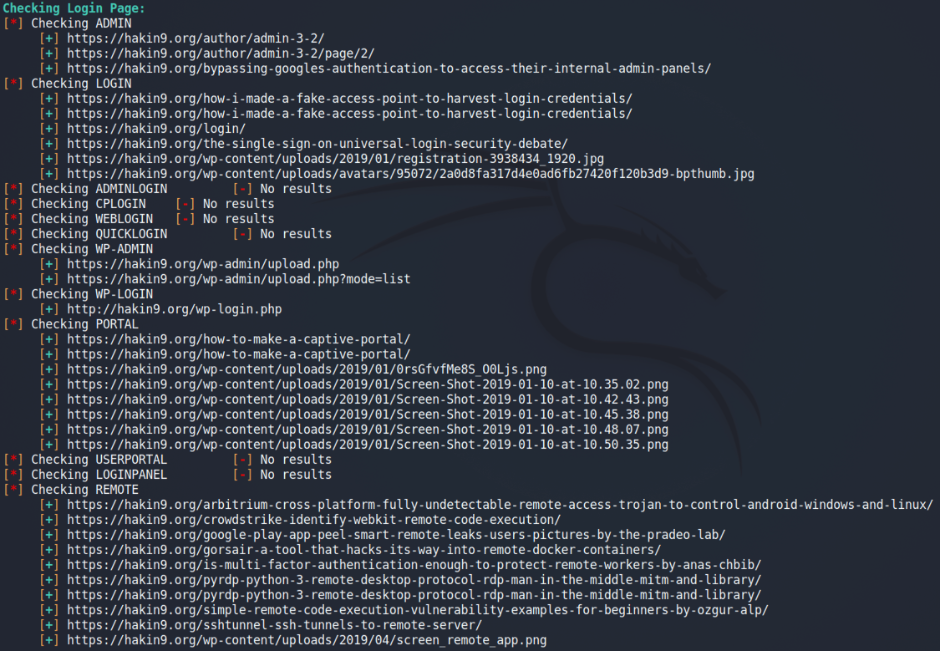
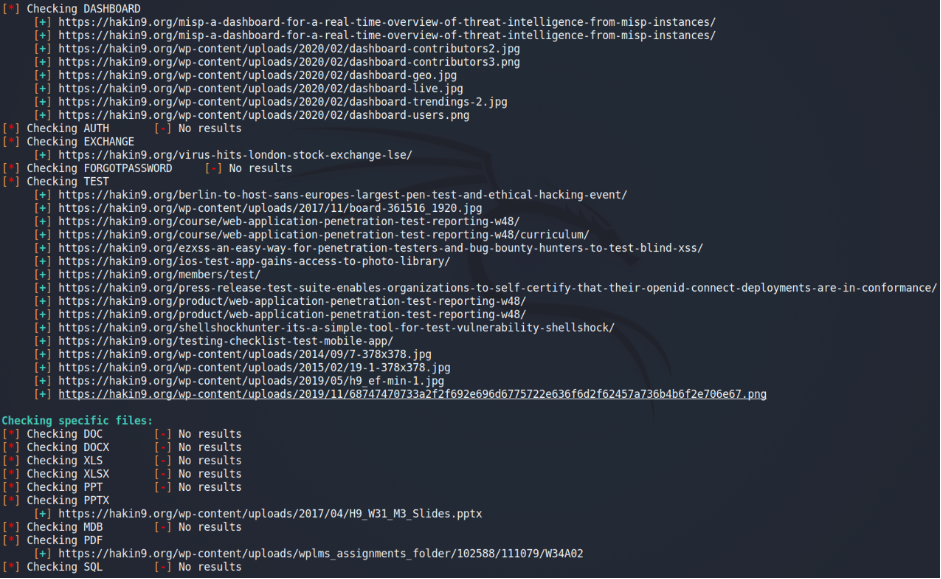
Excellent. Now it’s time to check each link the application gave us.
We will start with PowerPoint Presentation file.
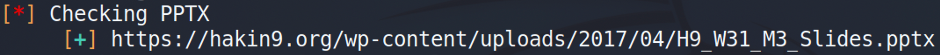

Seems like it’s a wireless hacking course. I don’t know if it’s free or not, but we may freely download it and learn something.
What’s next? I would suggest the member link.
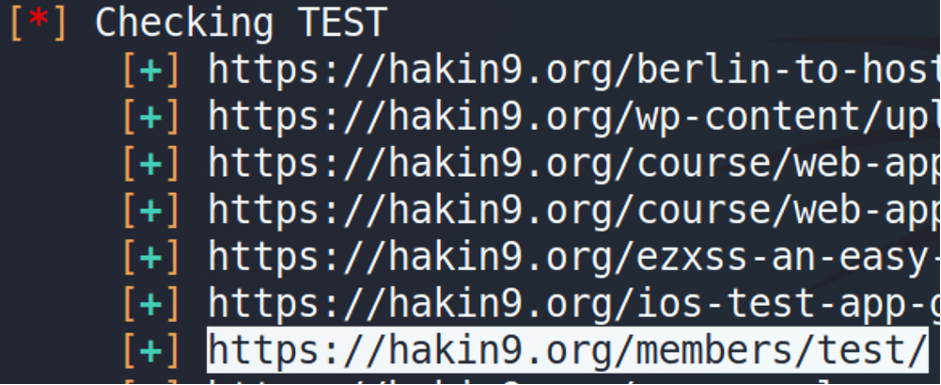
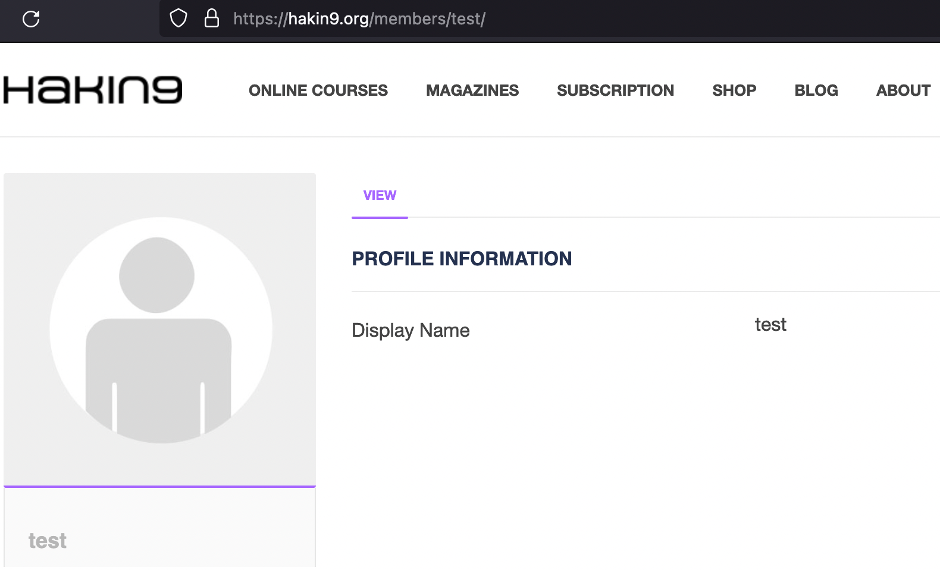
What the good news. I assume we found a valid link for user enumeration. What about an IDOR – https://hakin9.org/members/{IDOR}? We will leave it to you as a homework 😉
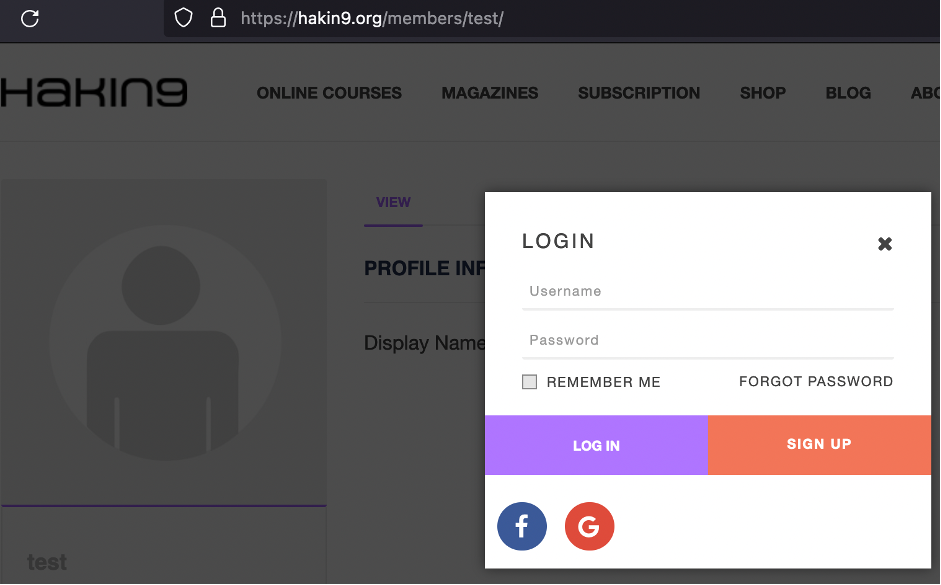
But, if we combine it with the login page, password brute force is the next step for the possible attacker.
And the last for today – Avatar from uploads.

Hm, interesting. Let’s try the simple google search by the photo.
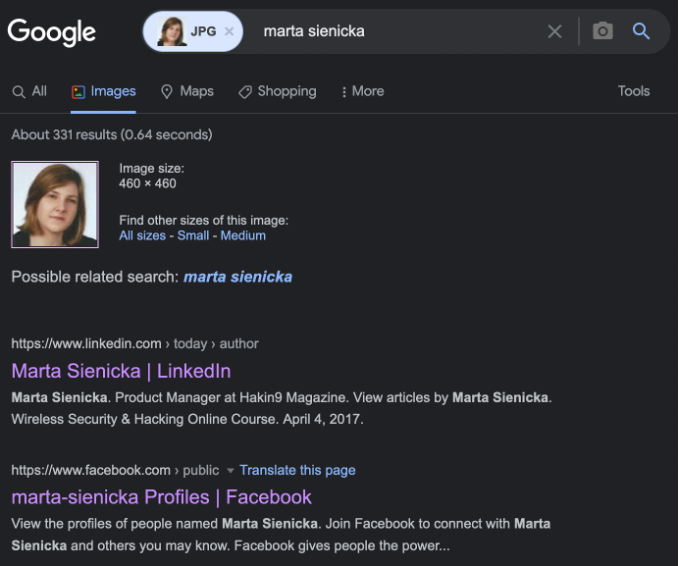
Hello Marta, how are you? Hope you and your family are doing well.
As you can see, we have successfully found Marta Sienicka, the Product Manager at Hakin9 Magazine.
- Conclusion
Having considered all the arguments above we may conclude, that reconnaissance, as a first stage of any penetration test, is crucial. The right application you choose to find the information will reveal gaps and give you some tips for the successful penetration, consequently the last thing you have to do is to use that properly. “Enumeration is the key”
=====
Original article link -> https://hakin9.org/product/open-source-tools-for-2021/
You may download the full magazine after a free registration.
