Capture the flag (aka CTF) is a cybersecurity game the main aim of which is to crack/solve/find the solution to the weirdest IT tasks and get the “Flag” – flag{cae7aa373c8224a6ad7e0aa6de356608}. Each task has its own value (usually from 50 to 500) and the winner is the hacker/team who reach the most points.
One of the such kind of CTF was last weekend called h@cktivitycon2021 organized by HackerOne in partnership with the HackTheBox, Offensive Security, Red Team Village and IOT village. John Hammond (https://www.linkedin.com/in/johnhammond010/) and congon4tor (Discord congon4tor#2334) were the authors of the tasks.
The CTF lasted for 48 hours and 15506 were the highest score. I have played that CTF for about 6-7 hours and succeeded to achieve top 10% of the leaderboard (284/2527), earned 1182 points. Not bad for the team with the only one player 🙂 (unfortunately my team was not available last weekend so I had to play by myself).
Let me describe some of the challenges which were presented to the game and which I was able to solve.
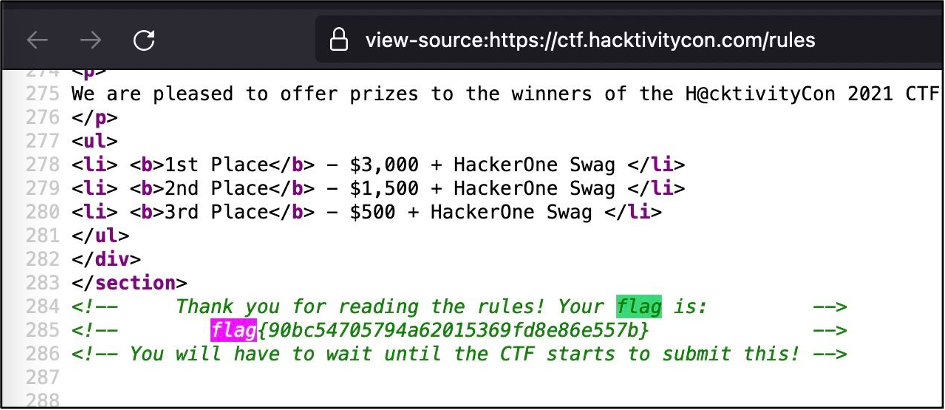
I started my game from the opening challenge valued with 50 points. As far as I remember it called “Read the rules”. You had to visit h@cktivitycon2021 rule web-page and found the flag. To capture the flag, you had to open the source code of the page and found the treasure 🙂
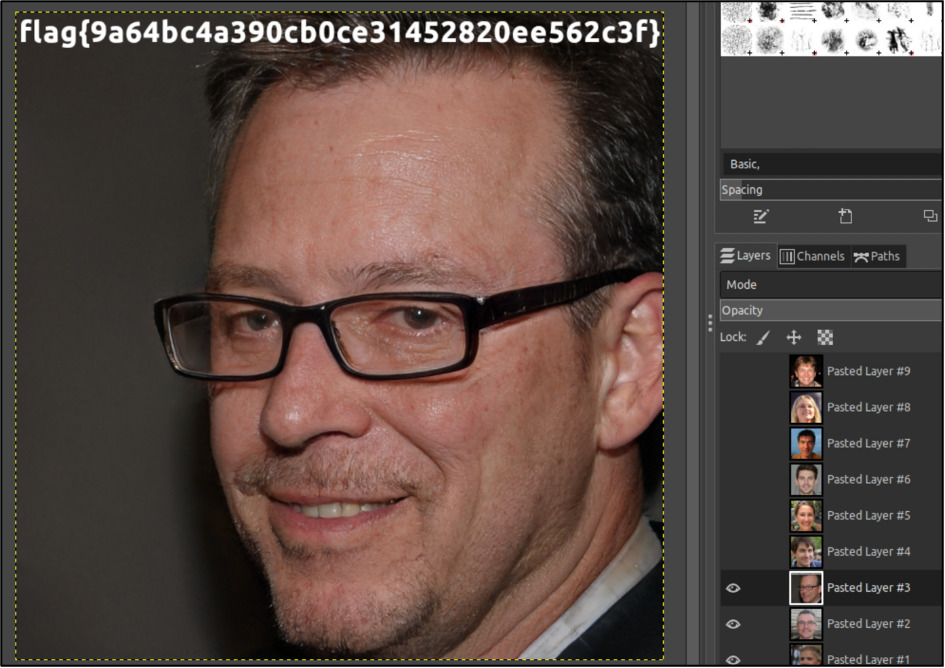
The next one was “Pimple”. You had to download a file and after the “file pimple” Linux command realized it was GIMP file. Ok, let’s open the GNU Image Manipulation Program (GIMP) and try to find a flag. As you can see there are plenty of layers, one of which contains the flag.
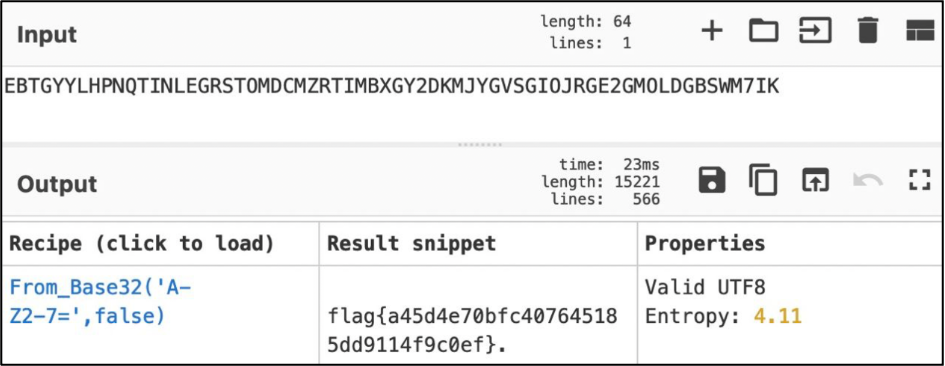
Let’s go further. The next challenge called “SIX FOUR OVER TWO” where you had to download the file as well. It was the simple text file contained the encoded string looked like as base64. Moreover, the name “Six four” is the link to the same encoding process. Unfortunately, it did not work to me so I decided to make some “magic” using Cyber Chef (https://gchq.github.io/CyberChef/).
Base32 is the solution and the flag is flag{a45d4e70bfc407645185dd9114f9c0ef}.
The next CTF task is called “Bass64”, pretty straightforward name. But, having opened the file I found some messy chars. After the stretching the text editor I realized chars changed their places. As a result, I had a very loooooooong text string base64 encoded. The flag is flag{35a5d13da6a2afa0c62bfcbdd6301a0a}.

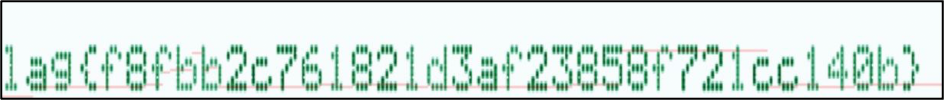
“Tsunami” was my next target. I downloaded the attached file and that was an audio. I used the online audio analyzer https://morsecode.world/international/decoder/audio-decoder-adaptive.html to see the spectrogram. The flag appeared in 10 seconds – flag{f8fbb2c761821d3af23858f721cc140b}.
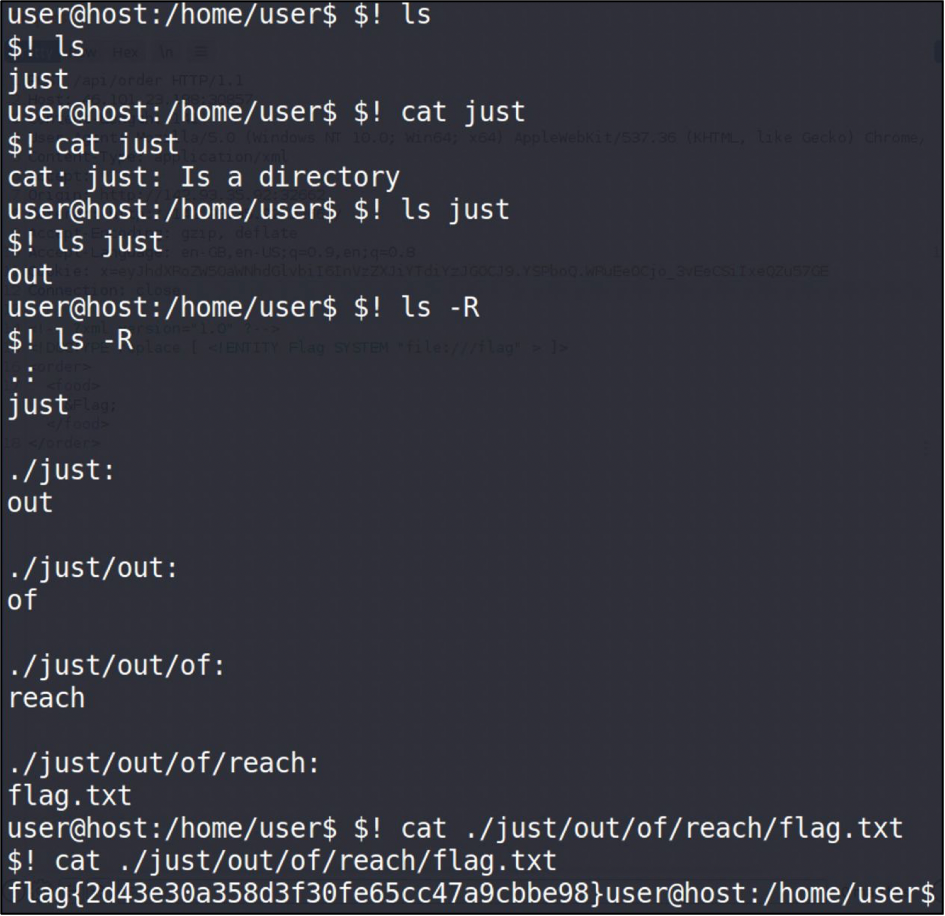
The next one is “Badwords”. You connect to the server and try to read the flag. But you cannot do that due to some bash restrictions. After a little research I found the solution – it’s needed to place $! in front of the command. The flag is flag{2d43e30a358d3f30fe65cc47a9cbbe98}.
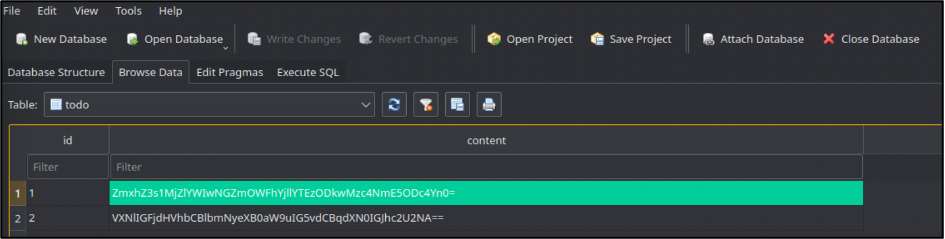
What’s next? “To do” is an android challenge. At first, I was afraid to take that due to my lack of mobile hacking, but positive experience from some last similar HackTheBox challenges pushed me forward 🙂 I downloaded an APK file and unzipped that. There were tons of file, but “grep” is our magic stick. Having search the “admin” string I found the SQL Lite database with 2 base64 encoded strings, one of which was the flag – flag{526eab04ff9aab9ea138903786a9878b}.
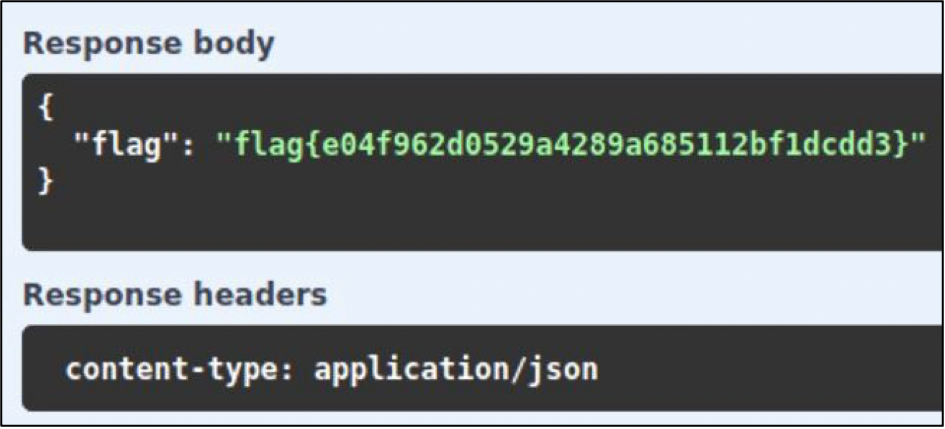
The next challenge on my way was “Swaggy”. That was an API core with identification. After entered admin:admin as a default credentials I was able to send a query and get the flag – flag{e04f962d0529a4289a685112bf1dcdd3}.
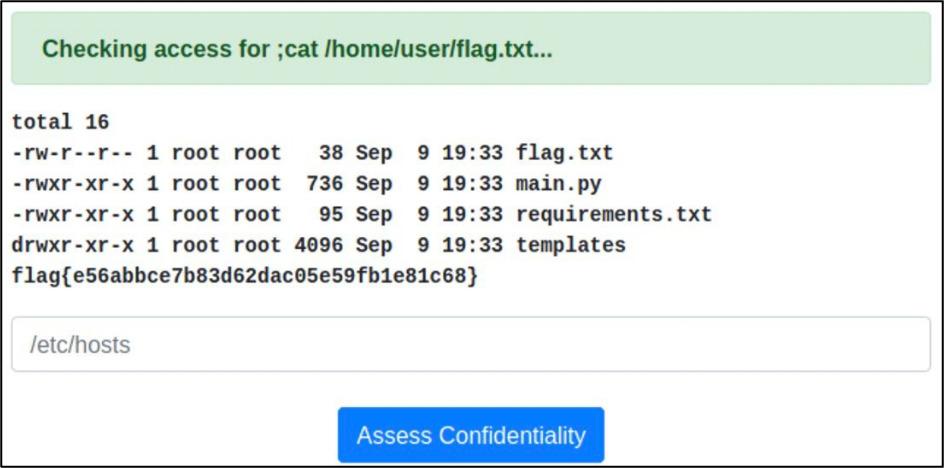
“Confidentiality” was a perfect task for educational purposes. It was a server-side application which executed the “ls -la” command. Due to it’s a common task on CTF hackatons, bypassing was pretty straightforward – use the pipe by “;”, “&&” or “||”. The flag is flag{e56abbce7b83d62dac05e59fb1e81c68}.
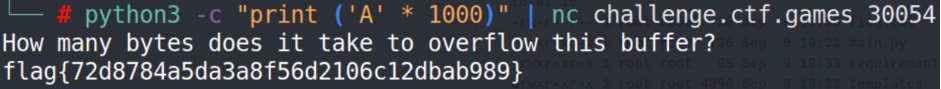
“Buffer overflow” – I assume some teams even didn’t try to launch that task 🙂 what was their big mistake. The challenge consists of 2 parts – I had to download pile of files, read and understand them and after that launch the solution to the server. Having read the C-program file I found there is 0x200 (512 chars) stack which we have to overflow. Got it. Let’s try to get the flag which, by the way, is flag{72d8784a5da3a8f56d2106c12dbab989}.
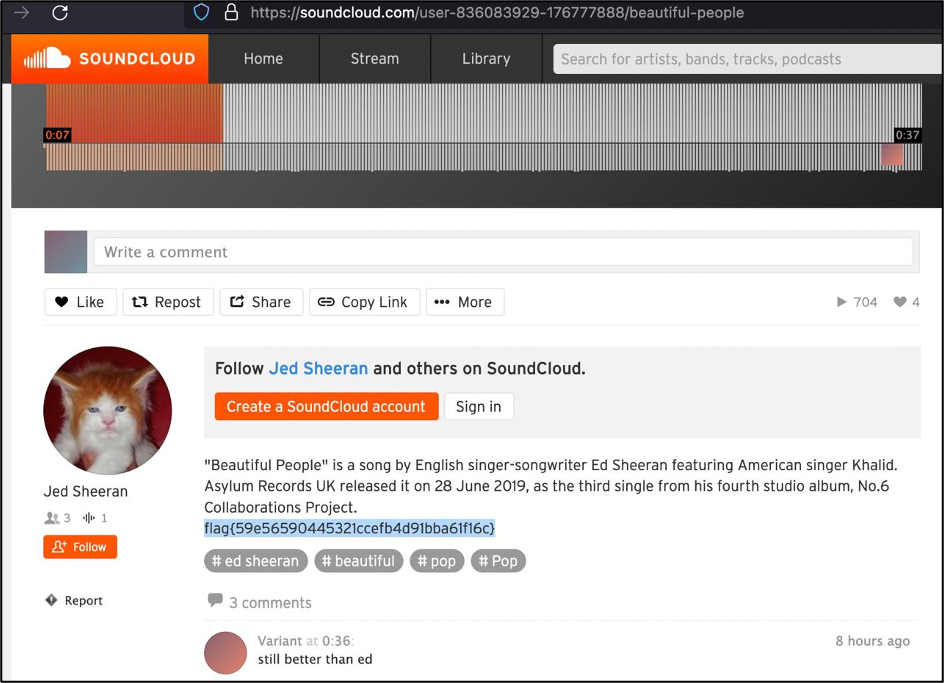
My next target was the OSINT challenge. I do not remember the name, but it was about a music and Jed Sheeran. The 3rd google link follows us here (https://soundcloud.com/user-836083929-176777888/beautiful-people), so the flag is flag{59e56590445321ccefb4d91bba61f16c}.
“Titanic” was my one of my favorite challenges during the h@cktivitycon2021. It was a Server-side request forgery (SSRF) vulnerability which allowed us to read the restricted files.
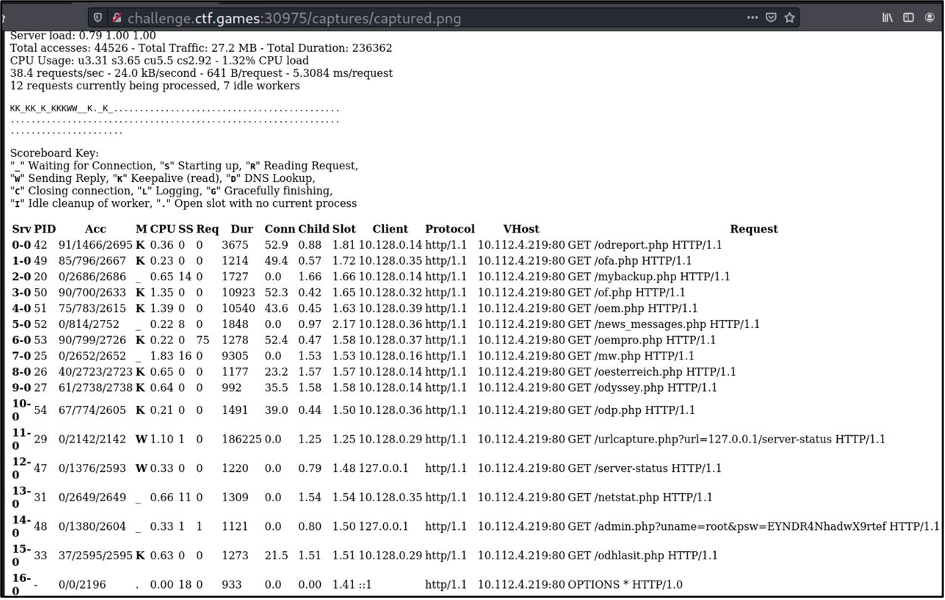
First of all, I started with the enumeration and launched WFUZZ app which showed me “server-status” page. Unfortunately, that was 403 error – Unauthorized access. Moreover, robots.txt pointed to “server-status” web-page as well. That was a hint. But how to read that restricted page?
Having browsed the web-site I found an application that made internet web-site’s screen shots. But what about the localhost and our restricted page? What if we enter http://localhost/server-status?
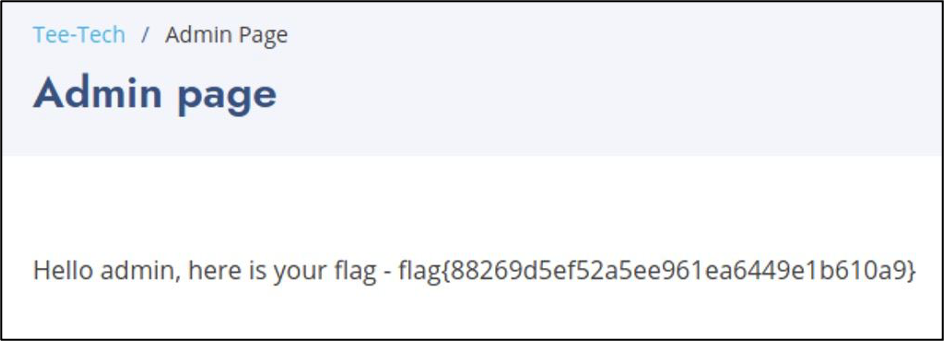
We got root login and password hurray. The next step is to enter the credentials to the login page and we’ve got a flag – flag{88269d5ef52a5ee961ea6449e1b610a9}.
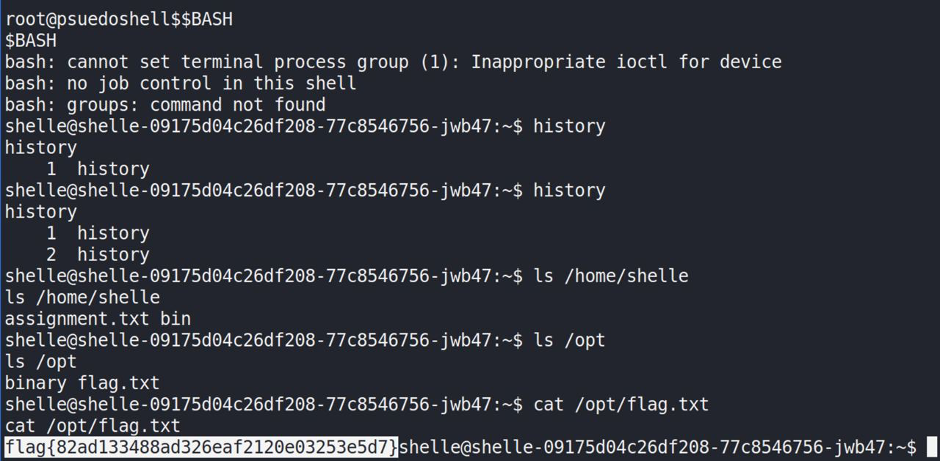
The next one was “shelly” and that was quite tough. I’ve spent for about 30-40 minutes to get the right way. It was a restricted shell (something like rbash) where worked only several commands and backslash was denied. Fortunately, “export” app was working and I was able to read the preinstall values. One of them was “BASH=/bin/bash” – exactly what I needed.
Having launched $BASH I started new terminal with a well-known shell 🙂 By the way, the flag is – flag{82ad133488ad326eaf2120e03253e5d7}.
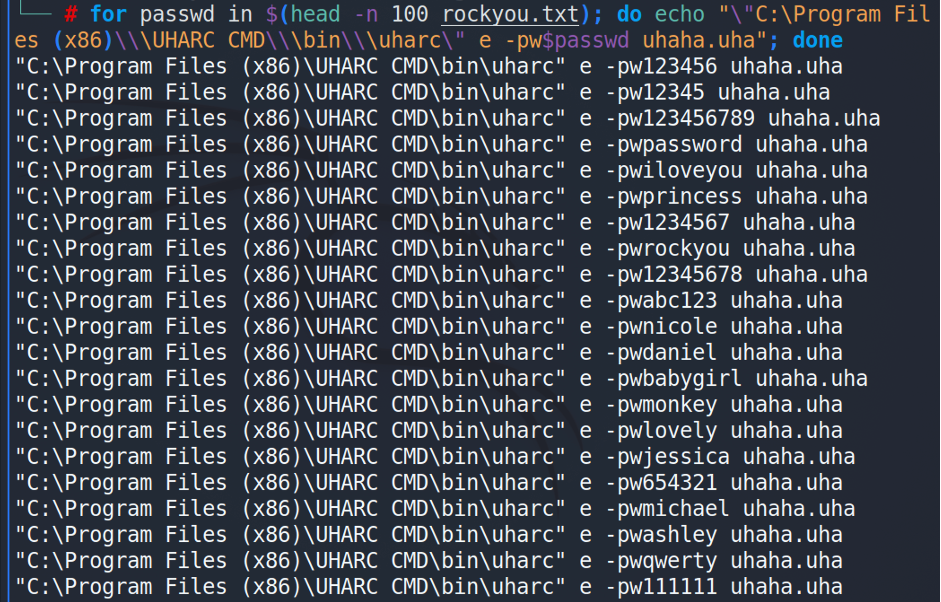
“UHAHA” was totally an outstanding challenge and only 87 teams of 2527 succeeded to solved that. The task based on uharc file compressor and I had to decompress that several times to get the flag. The issues were that each container protected by the password (top 100 rockyou passwords) and uharc is working under the Windows.
So, I launched the Windows 10, downloaded and installed uharc program, learned the documentation and started working. To increase the speed of solving the CTF, I created a script to generate the commands:
for passwd in $(head -n 100 rockyou.txt); do echo “\”C:\Program Files (x86)\\\UHARC CMD\\\bin\\\uharc\” e -pw$passwd uhaha.uha”; done
After that I copied the output and launched to the Windows’ CMD. Due to the specific of the task, I also created one more script to delete the old archive and renamed the new one. The full method is on the screen shot below.
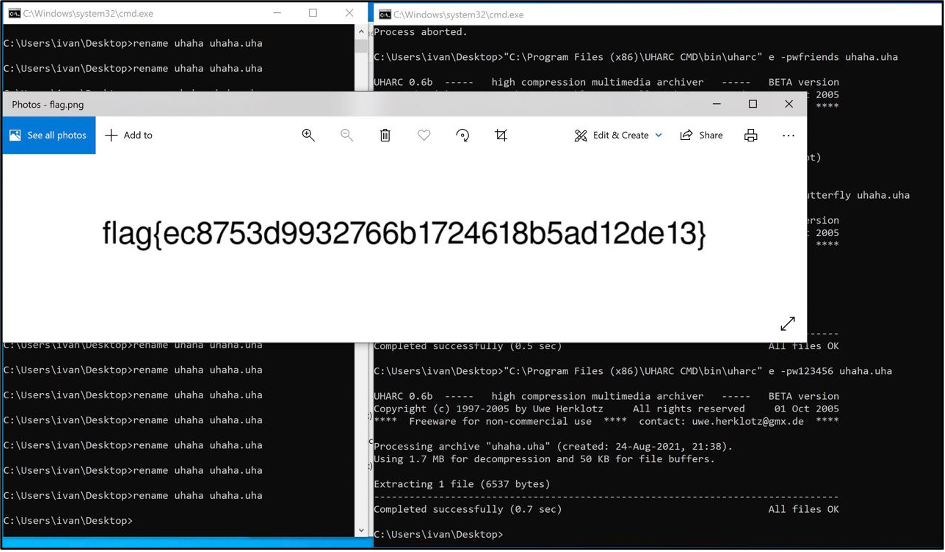
That was my personal h@cktivitycon2021 CTF journey. I found 6 or 7 more flags which allowed me to reach closely to the top. I would like to thanks all players with our interesting weekend, HackerOne for the event and personally John Hammond for the tasks.
Hack ‘em all.
